 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| The base commander's plan of action must achieve adequate protection to ensure accomplishment of missions by base elements with as small a force as necessary, since any drain of time and personnel from operational activities will adversely affect the accomplishment of their missions. |
| Preface, FM 31-81 (Test), Base Defense, March 1970 |
This appendix provides basic guidance for commanders and staff officers on the organization of forces, control measures, and planning, preparing, and executing considerations pertaining to rear area and base security and route and convoy security operations. The tactics and techniques expressed in this appendix are applicable across the full spectrum of operations (offense, defense, stability, and support). However, commanders must interpret them in accordance with the enemy's capabilities. For example, the physical layout of a base will be vastly different if the enemy has a significant air capability than if the enemy has no air capability. The purpose of rear area and base security operations is to prevent interruption of current and future operations. Rear area and base security operations constitute one of the five elements that constitute sustaining operations. (See FM 3-0 for a discussion of sustaining operations as part of the battlefield framework.)
|
E-1. One of the fundamental considerations in rear area and base security is the resolution of command authority. The echelon commander must clearly define command relationships before initiating any operations. A conflict of interest can occur if command relationships and responsibilities for rear area and base security are not clearly identified. All tenant units in a specific geographical area are responsible to the commander of that area for rear area and base security. Therefore, a rear area commander has tactical control (TACON) over tenant units for conducting rear area and base security. The echelon commander resolves conflicts between the tactical and functional command elements. (See Figure E-1.)
E-2. There are units subordinate to commanders other than the echelon commander located throughout an echelon's rear area. Many units operating in the rear areas of a corps, division, or brigade are not organic to those echelons. For example, units from the theater support command and other theater organizations, such as the theater signal command or theater engineer command, operate within the corps rear area. The division has elements of corps support groups (forward) and other corps organizations, such as a corps signal battalion, operating within the division rear area. The brigade many have elements of theater, corps, and division organizations operating within its rear area.
E-3. However, an echelon rear area, base cluster, or base commander is responsible for the rear area and base security of all units in his assigned area. The echelon rear area commander has the authority for terrain management within the echelon rear area and assigns every unit to a base or base cluster. All units assigned to a base or base cluster are TACON to the commander of that base or base cluster when an emergency or tactical situation requires the implementation of rear area and base security measures unless specifically exempted by order of the echelon commander.
E-4. The echelon commander establishes the relationships between the subordinate forces of different countries occupying the same geographical area. This structure unifies the different forces to the maximum degree feasible. Resulting language, doctrinal, and philosophical differences may be resolved by—
Recognizing national affinities and permitting homogenous elements to operate together.
Combining units of different nationalities only where a clear requirement exists.
Cross-assigning liaison personnel to improve understanding.
Organizing area responsibilities along national lines.
Establishing a mutually supporting warning system.
E-5. Using host nation forces presents a distinct advantage to a commander responsible for rear area and base security because of their knowledge of the area, its language, and customs. Commanders involved in sustaining operations take all possible efforts to use these assets effectively.
E-6. Civilian employees supporting US military forces are subject to hostile action. Protecting DOD civilians and contractors providing battlefield support to Army units is the responsibility of the commander of the host base. The supported base or military unit assures the protection of its operations and personnel. DOD civilians and contractor personnel cannot take an active role in conducting security operations, but retain the inherent right to self-defense.
E-7. Commanders and staff planners assess the need for protecting these individuals and designate forces to provide security when appropriate. The mission, threat, and location where DOD civilians or contractors operate determine the degree of security required.
E-8. Protecting DOD civilians and contractors involves not only active protection through the use of armed military forces to provide escort or perimeter security, but also training and equipping of these personnel for self-protection. Base cluster commanders may train and equip DOD civilian and contractor personnel, if they agree, to work in a nuclear, biological, and chemical (NBC) environment and to carry individual, military specification weapons for personal protection when the threat exists and the geographic combatant commander grants approval.
E-9. The base commander identifies specific security and protection requirements for DOD civilians and contractors located on or transiting the base and designates resources and forces to address those requirements. He includes these decisions in the base's OPLANs/OPORDs and their supporting plans and standing operating procedures (SOP). This allows the base's tenant units and civilians to properly integrate these protection requirements into their operational procedures.
E-10. DOD civilians and contractors are responsible for following all protection requirements and policies-as stated in the contractual agreement. This includes ensuring they receive training in NBC protection and weapons familiarization, when authorized, and informing them of local threats, facility and travel security requirements, and off-limits restrictions directed by the base commander. Failure to adhere to protection requirements and policies could result in disciplinary actions for DOD civilians and possible contract termination for contractors.
E-11. The success of rear area and base security hinges on binding together diverse resources. The commander must meet the following requirements to eliminate a potential confusion and to achieve a cohesive effort—
There must be a single responsible commander.
Geographical areas of operations (AOs) and thus responsibility must be clearly defined.
E-12. Overall responsibility for conducting sustaining operations in a commander's AO rests with the commander. Because the commander cannot afford to focus strictly on sustaining operations he assigns that responsibility to another officer and gives that individual a staff to help him accomplish that operation. The individual responsible for a tactical echelon's sustaining operations is called the rear area commander.
E-13. A corps commander normally assigns the mission of sustaining operation to the deputy corps commander. In a similar manner, the assistant division commander (support) is responsible to the division commander for sustaining operations in the division rear area. The forward support battalion commander supporting the brigade is normally responsible to the maneuver brigade commander for sustaining operations in the brigade rear area. While the echelon commander has the authority to designate someone else as the echelon's rear area commander, doing so complicates staff relationships.
E-14. The responsible rear area commander at each of these three echelons uses the echelon rear command post to monitor the echelon's sustaining operations. This assures the synchronization of the five elements of sustaining operations and an orderly, effective, and timely escalation when conducting rear area and base security. This encompasses the use of host nation and organic combat support (CS) and combat service support (CSS) units through employing a tactical combat force (TCF). The echelon rear command post develops plans integrating the rear area and base security activities of all units located within the echelon rear area. Each echelon rear area commander has the authority to further divide the echelon rear area into subordinate AOs, base clusters, and bases.
E-15. A rear operations center (ROC) provides the corps or division rear area commander with the nucleus of an operations cell within the corps or division rear command post. It is a reserve component organization since the functions it performs are not required in garrison. It contains no organic life support capabilities, such as mess, supply, and maintenance, and relies on the echelon headquarters' commandant for those functions. The soldiers assigned in peacetime to these organization lose their separate identity after being activated and deployed. They are assigned to the corps or division headquarters company and become the rear command post representatives of the echelon G2 and G3.
E-16. A corps rear area commander generally subdivides the corps rear area into subordinate AOs that correspond to the AOs of his subordinate corps support groups. A rear area operations center (RAOC) provides the corps support group commander with a greatly increased plans and operations capability for his operations center to assist in conducting terrain management, rear area and base defense, movement control and area damage control (ADC) within his AO. It also provides him a limited capability to conduct liaison with subordinate base cluster defense operations centers (BCOCs) and base defense operations centers (BDOCs). (See Figure E-2.)
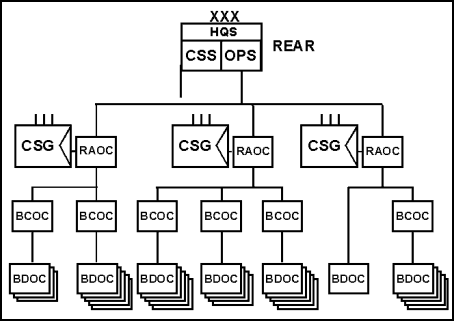
Figure E-2. Organization of C2 Facilities in a Corps Rear Area
E-17. Like a ROC, a RAOC is a reserve component organization that contains no organic life support capabilities, such as mess, supply, and maintenance. It must rely on its assigned CS/CSS brigade/group headquarters to which they are assigned for those functions. The soldiers assigned to a RAOC maintain their separate identity after being activated and deployed, unlike those assigned to a ROC. Therefore, the corps rear area commander can move them as necessary to provide additional command and control (C2) capabilities within the corps rear area.
E-18. Responsibility for overall rear area and base security, as well as defense against large enemy attacks, belongs to the echelon rear area commander. He charges each base and base cluster commander with responsibility for his local and internal security to safeguard the base/base cluster and its facilities from infiltration and small-scale attacks. Each base and base cluster defense plan is coordinated with, and becomes a part of, the echelon rear area defense plan.
E-19. A base is a locality from which operations are projected or supported (JP 1-02). It can contain one unit or multiple units. It has a defined perimeter, established access controls, and is situated and configured to take advantage of natural and man-made terrain features. Missions and security considerations determine the selection of a base site. To nullify or reduce the effectiveness of enemy attack, the rear area commander assigns all units located in the rear area that are not actively involved in operations to a base. Bases may be further organized into base clusters or organized as a separate bases that report directly to the ROC or RAOCs controlling rear area and base security for the AO where the base is located. A commander may name his base or use a mixture of alphanumeric characters to designate it.
E-20. In base defense operations, the base commander is the officer assigned to command a base (JP 1-02). The base commander is responsible for defending his base. He is normally the senior Army competitive category officer on the base unless the base contains only medical units. He exercises C2 over the base and necessary control of resident and transient units. The base commander's responsibilities include establishing the overall base defense organization as well as planning, preparing, executing, and assessing all local security measures. This includes the tactical control of US Navy, Air Force, and Marine Corps forces assigned to the base primarily for the purpose of local base defense, such as a US Air Force security flight. Forces of other services or functional components assigned or attached to the base for primary purposes other than local base defense will support local base defense during an imminent attack or threat of an attack. For more information on joint rear area and base security see JPs 3-10 and 3-10.1.
E-21. The base commander uses all assets within the base perimeter to create the required level of local security. He has the authority to position units assigned to his base in mutually supporting positions. He directs employing of obstacles, such as wire- and command-detonated antipersonnel mines, to defend each base within the guidance of his rules of engagement (ROE). He identifies shortages in materiel or weaknesses in required defensive capabilities early and requests the necessary reinforcements and supplies to correct those weaknesses.
E-22. A base commander is also usually a battalion commander, and the BDOC forms around the nucleus provided by his battalion staff. The echelon rear area commander normally does not assign the function of base command to MP commanders because of their need to exercise command over MP elements responding to Level II threats within the echelon rear area.
E-23. The base defense force (BDF) commander needs a BDOC to ensure the integration of defense plans and maximum effectiveness of the total base defense effort. A base defense operations center is a command and control facility established by the base commander to serve as the focal point for base security and defense. It plans, directs, integrates, coordinates, and controls all base defense efforts, and coordinates and integrates into area security operations with the rear area operations center/rear tactical operations center (3-10.1). The nature of the BDOC depends on the combination of forces involved and may be joint, interagency, or multinational depending on the combination of forces involved.
E-24. The BDOC is similar in many respects to the tactical operations center found in maneuver brigades and battalions. Representatives of the intelligence, maneuver, and fire support battlefield operating systems (BOS) staff the BDOC. The base commander provides other BOS representatives to his BDF commander on an "as required" basis. Multiservice, other agency, and multinational representation, with decision making authority, is present in the BDOC when elements of their armed forces, police, or paramilitary forces are directly involved in the overall base defense effort.
E-25. The center consists of two primary sections-the command section and the plans and operations section-with additional sections as deemed necessary. These additional sections could include a CSS section to plan the provision of services and support to the base, and an ADC section that provides inspection, planning, and control of the base's ADC resources. This center is fully manned and operates continuously. It primary functions are—
Keeping the base commander informed of the current situation within his AO, including enemy, friendly, and civilian activities.
Preparing comprehensive plans to implement the commander's overall base defense and security guidance.
Ensuring the participation of all units within the base perimeter in conducting active and passive defense and security measures.
Reducing any conflicting interests inherent in multiservice or multinational BDF environment.
Providing centralized collection and processing of information from various intelligence and operational sources and disseminating resultant intelligence products as appropriate.
Providing the essential C2 organization necessary to conduct coordinated defensive operations.
E-26. The base commander establishes the BDF from available base CS and CSS assets if MP and combat arms units are not available to provide the necessary local security. He designates the BDF commander to avoid confusion and provides that individual necessary guidance.
E-27. A base cluster in base defense operations, is a collection of bases, geographically grouped for mutual protection and ease of command and control (3-10). A base cluster normally does not have a defined perimeter or established access points. The base cluster is normally the next higher tactical C2 headquarters of the base. A base cluster typically contains five bases but can range from two to seven bases. The rear area commander designates each base cluster and assigns it either a name or an alphanumeric designation.
E-28. The senior Army competitive category officer in each cluster becomes the commander of that cluster. Like a base commander, he establishes a continuously operating BCOC to support the tactical chain of command. This officer is normally the commander of a CS or CSS brigade or group and his staff forms the BCOC nucleus. The BCOC integrates each base defense plan into the base cluster defense plan.
E-29. The BCOC keeps the base cluster commander informed of the situation in his area and of the resources available to cope with emergencies. It represents the commander's planning capability and provides him a C2 system to control the execution of rear area and base security missions. The BCOC can provide functional elements with current information they may require to conduct their normal CS and CSS functions. This includes—
Highway road conditions, new unit or activity locations, security and support activities, refueling points, emergency maintenance and recovery facilities, medical facilities, rest stops, and reroutes.
Intelligence data, including weather, terrain, and civil considerations.
Location of area communications sites that units, convoys, or soldiers on the move can link into to maintain a current common operational picture.
Location and level of contamination from enemy use of weapons of mass destruction or chemical contamination resulting from the use of conventional munitions and industrial accidents.
Location of hazards resulting from battlefield activities of both sides.
Available explosive ordnance disposal (EOD) support.
E-30. There are three basic considerations in determining command policies governing the authority and limitations of the echelon rear area commander. These three factors are—
The threat levels and situation within the echelon rear area.
The utility of different locations within the echelon rear area.
Political considerations.
E-31. Threats to bases in the rear area are categorized by the three levels of defense required to counter them. Any or all levels may exist simultaneously in the rear area. Emphasis on specific base defense and security measures may depend on the anticipated threat level. A Level I threat is a small enemy force that can be defeated by CS and CSS units operating in the rear area or by the perimeter defenses established by friendly bases and base clusters. A Level I threat for a typical base consists of a squad-size unit or smaller groups of enemy soldiers, agents, or terrorists. Typical objectives for a Level I threat include supplying themselves from friendly supply stocks; disrupting friendly C2, logistics, and facilities; and interdicting friendly lines of communication (LOC).
E-32. A Level II threat is enemy activities that can be defeated by a base or base cluster augmented by a response force. A typical response force is a MP platoon; however, it can be a combat arms maneuver element. Level II threats consist of enemy special operations teams, long-range reconnaissance units, mounted or dismounted combat reconnaissance teams, and partially attritted small combat units. Typical objectives for a Level II threat include the destruction, as well as the disruption, of friendly C2 and logistics and commercial facilities, and the interdiction of friendly LOCs.
E-33. A Level III threat is beyond the defensive capability of both the base and base cluster and any local reserve or response force. It normally consists of a mobile enemy force. The friendly response to a Level III threat is a TCF. Possible objectives for a Level III threat include seizing key terrain, interfering with the movement and commitment of reserves and artillery, and destroying friendly combat forces. Its objectives could also include destroying friendly CSS facilities, supply points, command post facilities, airfields, aviation assembly areas, arming and refueling points, and interdicting LOCs and major supply routes.
E-34. The utility of a given location is a vital factor to the rear area commander. Some areas are critical to conducting the echelon's sustaining operations. Others are priority areas important to conducting the echelon's sustaining operations. Still others are areas where he must exercise some general control but which are neither critical nor priority areas. Finally, there are areas of no importance in the echelon's sustaining operations.
E-35. A critical area is an area or geographical point essential to accomplishing the echelon's sustaining operations. The loss, neutralization, or interdiction of this area allows no alternate operations and adversely affects sustaining operations. An example of a critical area would be the only available port within an AO.
E-36. A priority area is also an area or geographical point essential to accomplishing the echelon's sustaining operation except that within an acceptable amount of time sustaining operations functions can be transferred to an alternate location without an immediate significant impact on the total CSS effort. An example of a priority area would be a supply point containing the ammunition designed to support an offensive operation or an installation performing an important function, such as repairing thermal sights. Another example of a priority area would be a bridge over a major waterway.
E-37. Areas retained under general control are normally the best areas for their designated purpose, but sustaining operations conducted within them can move to other locations without major problems. Examples of areas over which the rear area commander must have some general control are LOCs and main supply routes.
E-38. The rear area commander coordinates with the host nation, using available civil affairs (CA) and operational law personnel to obtain the necessary authority to conduct security measures required by the sensitivity of the area and the situation. These security measures include conducting patrols outside of base perimeters, establishing procedures for clearing indirect fires, and conducting counterintelligence operations. Negotiations also address such measures as establishing a curfew, imposing circulation control over civilian traffic, and similar policies for the host nation civilian populace as dictated by the factors of METT-TC.
E-39. At the division and corps echelons, there could be areas within the echelon rear area commander's AO that do not affect the echelon's sustaining operations. The rear area commander prefers not to commit his scarce intelligence, surveillance, and reconnaissance resources in those areas but leaves the responsibility for detecting and countering enemy activity in those areas to the host nation.
E-40. The degree of control that the rear area commander has over host nation authorities and the civilian population depends primarily on the political conditions under which US forces entered the AO. Generally, US military presence occurs in one of two ways:
Entry by invitation of the host nation.
Forcible entry.
The extent of and limitations on military activities are prescribed by customary international law or by international agreements to which the US is a party, or by both in either environment.
E-41. The rear area commander may encounter a range of situations extending from a host-guest relationship to total US authority under conditions of military government. He may have no power over the host nation authorities and civilian population except what he can exert through influence and coordination in some cases. Populace controls, mutual support between civilian and military resources, and the coordination of civilian and military security and damage control measures are of utmost importance to rear area and base security. The commander must constantly be aware of and understand his relationship with host nation authorities and the civilian population. A clear understanding of his authority is essential to the rear area commander in exercising that degree of control necessary to ensure security and safety to all friendly military forces and the civilian population located within the AO.
E-42. Through legitimate agreement by the interested governments, a host nation may request US forces to assist the host nation for a mutually agreed reason. Liaison and coordination are the primary means of establishing acceptable military-civilian communications. The commander's initial requirement is the provision of maximum civilian support for and the prevention of civil interference with military operations. Host nation forces may be effective in rear area and base security because of their knowledge of the area, its language, and customs. US military advice and assistance rendered in accordance with applicable laws and regulations may enhance their effectiveness.
E-43. Forcible entry entails the seizure of terrain and facilities from enemy forces. Depending on circumstances, the operation may require the removal of existing civil or martial governmental apparatus or the restoration of a suppressed government. In the absence of civil authority, Army forces establish measures to control the civilian population and provide basic services. When US combat forces enter enemy territory to occupy it, initial disclosure of the nature and extent of US authority should include basic occupation directives in accordance with the laws of land warfare and CA doctrine. (See FMs 1-27.10 and FM 3-57.) These actions include issuing necessary proclamations concerning US authority as it relates to civil government, curfew, movement control, public order, and similar matters. Civil affairs units initiate, coordinate, and supervise local compliance with these directives.
E-44. The rear area commander must have the authority to protect and secure his installations and protect resources traveling along LOCs within his AO. Since this control affects the host nation governmental agencies and the civilian populace, he must not use that authority in a manner that alienates those audiences to the US mission and objectives.
E-45. Within the limits of the authority granted to them under local law, host nation civil officials may delegate political authority over local government to the military commanders of their own nation. The rear area commander must coordinate his operations with the host nation military area commander in conformance with US policy directives and requirements when this condition exists. Otherwise, the rear area commander coordinates his operations with the appropriate host nation agency.
E-46. The host nation military commander normally assumes responsibility for reconnaissance and security outside the perimeter of US military bases. The base commander provides for interior guard and control within the confines of his base and the security of his perimeter. The rear area commander may not have exclusive authority over local national civilian employees within his installation. Authority to hire and fire, investigative jurisdiction in matters of sabotage or espionage, and other vital matters of mutual concern to both the US command and the host nation must be delineated and agreed on for effective rear area and base security. The US rear area commander must maintain authority to control access to his bases when the situation warrants. Counterintelligence units are responsible for investigating sabotage, espionage, and subversion. Military police criminal investigation teams assist them as appropriate. In response to events having significant high-level interest, other governmental agencies, such as the FBI, may participate in these investigations.
E-47. Base and base cluster defense is the cornerstone of an echelon's successful rear area and base security effort. The following paragraphs outline the organization of forces, control measures, and considerations pertaining to planning, preparing, and executing base and base cluster defense.
E-48. The rear area commander uses a combination of base and base cluster defense forces, designated response forces, and TCF, to provide the required security within the echelon rear area. Special operations forces (SOF) may conduct counterterrorism operations within the rear area on an exception basis.
E-49. A base defense force is a security element established to provide local security to a base. It normally consists of the combined security assets provided by each unit on the base toward the ongoing security requirements of the base. These assets include crews, weapon systems, and radios of combat vehicles temporarily located on the base for maintenance or other reasons. It may consist of MP, infantry, armor, or cavalry units when the echelon commander's mission focuses on stability or support operations. The mission of the BDF is to conduct reaction operations to deter, resist, or destroy an enemy Level I force attacking the base. The BDF must be sufficiently flexible to defend the base perimeter, provide for the base's interior guard requirements, and conduct local offensive operations beyond the base perimeter if allowed by the host nation.
|
E-50. The base commander normally appoints a BDF commander to assist in executing base defense functions. He tasks units located within the base to provide soldiers, equipment, and materiel to form the BDF. The principal BDF tactical increments are normally provisionally organized security platoons. (See Figure E-3.) The base commander organizes his BDF as required by the intensity of enemy activity within the rear area.
E-51. A BDF should have a high degree of direct-fire lethality provided by a mixture of small arms, automatic weapons, and antitank systems. It should also have access to supporting indirect fires, a high degree of tactical mobility, and a reasonable span of control. It should be capable of—
Conducting reconnaissance patrols for detecting and reporting the location, strength, and capabilities of enemy forces located near the base.
Developing positions within and outside the base from which enemy advances can be stopped or destroyed.
Using reserve elements to attack relatively small enemy units that threaten to penetrate the base perimeter.
Providing internal security for critical capabilities located on the base.
The base commander must reconcile any issues about personnel and equipment resources shortfalls affecting the BDF and the desired level of security.
E-52. Most CS and CSS companies can provide a platoon-size security element toward the defense of their assigned base. (Figure E-4 shows a possible organization of such a security platoon.) A base having more than one security platoon also establishes a provisional security company headquarters for the BDF. The BDF commander will be the commander of this provisional security company. Most CS and CSS battalion headquarters can provide the resources for a provisional security company headquarters. The BDF commander designates a portion of the available security force as his reserve. In an emergency, the BDF is augmented by the defensive efforts of all units assigned to or transiting the base.
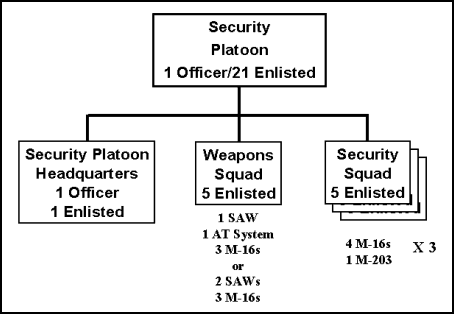
Figure E-4. Security Platoon
E-53. Operational requirements frequently modify a unit's ability to contribute resources to the defense effort of its base. Responsibility for reporting such modifications rests with the individual unit. The base commander brings these unrelated and unfamiliar groups together when creating his BDF. Every effort must be made to retain the unit integrity of these security platoons while assigning security tasks to the BDF.
E-54. Providing a BDF from CS and CSS organizations results in two undesirable conditions—
Reduced operational effectiveness of the units from which the resources are drawn.
Soldiers performing duties other than those for which they are specifically trained.
The unit commanders providing these security platoons assign personnel to them. Soldiers assigned to the BDF should remain there if operations permit, in order to facilitate training, provide for continuity of defense operations, and ensure force efficiency.
E-55. The base commander considers all available Army, joint, and multinational resources and forces in determining the exact organization of the BDF. Host nation police, paramilitary, and military elements will frequently be available to assist in providing rear area and base security. Early clarification of the positions, responsibilities, and authority of these elements reduces possible confusion and duplication of effort. The degree of cooperation the base commander attains from local host nation or third nation officials largely determines the effectiveness of those countries resources as they apply to base defense, regardless of the existence or absence of agreements made between forces at the national level. Special considerations for US employment of host nation elements include—
Designated host nation security force must be responsive to the demands of the base commander.
Caution may be necessary when assigning host nation security forces tasks requiring specialized equipment or skills.
The base commander should consult with the appropriate civil-military operations office to clarify any restrictions that might apply to the use of these forces.
E-56. The base cluster defense force consists of all of the BDFs within the base cluster. The base cluster commander can direct the employment of BDFs within the base cluster or segments of those BDFs to counter identified Level II threats within the geographical area of the base cluster. The more normal course of action (COA) is to have a response force engage these Level II threats. Base commanders must reconstitute those portions of their BDFs committed to these missions.
E-57. The purpose of rear area security forces is to facilitate a base's ability to return to mission accomplishment as quickly as possible rather than devoting CS and CSS resources to limited tactical operations. Rear area security forces can be further broken down into response forces and TCFs.
E-58. Response Forces. A response force is a mobile force with appropriate fire support designated, usually by the area commander, to deal with Level II threats in the rear area (JP 1-02). It usually consists of MP forces supported by available fire support and Army aviation assets. They are usually either platoon- or company-size forces. Military police elements may be temporarily or permanently unavailable in sufficient strength for response force operations because of their commitment to other missions. The commander should designate alternative response forces before this occurs. Other possible response force options include engineer units, chemical units, transiting combat units, elements of the reserve, or host nation assets. The rear command post coordinates with the echelon G3/S3 before committing forces other than MP units to response force missions.
E-59. The MP chain of command directs the size and composition of the response force when the echelon is primarily focused on conducting offensive and defensive operations. The nature and size of the threatening enemy force influences the size and number of MP elements that make up the response force. So, too, does the current rear intelligence preparation of the battlefield (IPB) and the echelon's rear area commander's risk assessment. The echelon provost marshal, in coordination with his rear area commander, considers—
The priority of ongoing operations.
The criticality of the base under attack.
The amount of time needed for given elements to consolidate.
The rear area commander continuously assesses the situation and, if appropriate, commits more response force assets to deal with the threat.
E-60. Tactical Combat Forces. A tactical combat force (TCF) is a combat unit, with appropriate combat support and combat service support assets, that is assigned the mission of defeating Level III threats (JP 1-02). These threats can result from enemy forces infiltrating friendly positions or penetrating friendly defensive positions and moving into the friendly rear area, or conducting airborne/air assault operations. A successful defense against such a Level III threat requires planning and preparing for the TCF's employment. The echelon commander can dedicate a TCF to deal with such a threat, designate another force as the on-order TCF, or accept the risk of not having a designated TCF. A dedicated TCF has the necessary assets, such as artillery and combat engineers, allocated to it to accomplish the mission. The echelon commander decides the exact composition of the TCF after weighing the risk of allocating forces to the TCF and thus decreasing the combat power available for his decisive operation.
E-61. The echelon G3 designates the number of TCFs in accordance with the situation and the echelon commander's guidance. Designating more than one TCF provides flexibility of response to competing needs. The primary advantage of having a dedicated, rather than an on-order, TCF is the assurance that it will be available when needed. Other advantages include the ability of the TCF staff to focus the force's planning and preparing activities on just one mission. This includes establishing liaison and communications with supported bases or base clusters and echelon Level II response forces. It also allows the dedicated TCF to rehearse its plans. When the commander assigns a subordinate unit an on-order TCF mission, he must establish criteria on when to commit that unit as the TCF.
E-62. A TCF can expect support from the following types of assets:
MPs with working dogs.
Military intelligence (includes counterintelligence).
Field artillery.
Engineers.
Army aviation (attack, air cavalry, air assault, C2, and possibly special electronic mission aircraft).
Public affairs.
Air defense artillery.
Area signal nodes.
Civil affairs assisted by psychological operations (PSYOP) elements.
CSS elements required to sustain the force conducting area security.
Any or all of these types of assets may not be immediately available to the TCF on its commitment. They are limited assets and may be engaged in other missions. The force conducting the rear area security mission may also receive support from other US and allied services, including the host nation.
E-63. The factors of METT-TC determine the size of the TCF. For a corps, this normally results in at least one battalion task force being assigned the mission. A division typically designates a reinforced company team as its TCF. The echelon commander configures his TCF to conduct offensive operations. The TCF must be extremely mobile and capable of moving by air and ground modes because of limited reaction time and extended distances between units common to the rear area. The TCF must be as mobile as the enemy. It should be capable of destroying armor-protected vehicles and dismounted infantry and of suppressing enemy shortrange air defense (SHORAD) systems. Consequently, a TCF typically consists of infantry, Army aviation (attack and utility helicopters), and air cavalry elements with engineer and field artillery support. The commander may also organize a TCF with armored cavalry, armor, and mechanized infantry units if the situation so dictates.
E-64. The commander strives to obtain tactical self-sufficiency within both the response force and the TCF. He does this by attaching or placing in direct support adequate fire support, CS, and CSS elements so that they can perform semiindependent operations. In addition, he must obtain resources, such as CA, PSYOPS, and interpreters, for interacting with the civilian population of the area being secured.
E-65. Special operations forces other than CA and PSYOP may combat terrorism within the AO of a conventional unit. A unit conducting rear area and base security may be tasked by a higher headquarters to provide conventional support to SOF elements conducting counterterrorism operations within its AO. If SOF operate in the area, a special operations command and control element (SOCCE) will normally be deployed at the Army forces or corps echelon, with liaisons attached lower for a specific mission to the unit responsible for the appropriate AO for the duration of the SOF mission.
E-66. Control measures in base defense operations are the same as those used in other defensive operations. (See Figure E-5.) The headquarters establishing the base or base cluster designates the base's AO using rear, lateral, and forward boundaries. The AO for the base may or may not be contiguous to the AO of other units. The echelon rear area commander may further subdivide his assigned area into subordinate AOs, bases, and base clusters. He can assign maneuver forces to assembly areas and battle positions. He establishes phase lines, contact points, objectives, and checkpoints as necessary to control his maneuver. He establishes fire support coordinating measures (FSCM) to permit or restrict fires in and around the base. (See Chapters 2, 3, and 8 and FM 3-09 for a discussion of FSCM.) No-fire areas may be required to protect civilians, prevent disruption of sustaining operations, or protect combat outposts, observation posts, and patrols from friendly fire. All established control graphics are coordinated with host nation agencies to minimize interference, misunderstandings, and unnecessary collateral damage. The BDF commander, in coordination with the base commander, designates the base perimeter, target reference points, and sectors of fire to organizations located within the base.
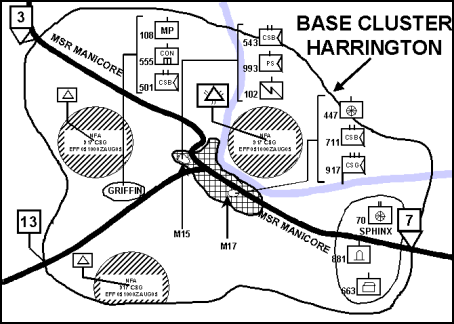
Figure E-5. Base Cluster Harrington
E-67. The echelon commander designs his rear area and base security system to ensure—
Maximum effectiveness of BDFs provided by CS and CSS units.
Minimum degradation to unit mission performance while providing the unit's contribution to the BDF.
Combat arms units are not diverted to provide dedicated rear area and base security forces.
E-68. Commanders in the rear area can improve their capability to effectively use available manpower and materiel by establishing logical priorities. The commander must allocate resources available to protect personnel, supplies, and facilities in consonance with the degree of risk involved. Sufficient personnel and materiel will not usually be available in the rear area to provide simultaneous protection to all of the echelon's sustaining operations.
E-69. Base defense plans are flexible and allow for differing degrees of security based on the probability of threat activity to maximize unit mission accomplishment. The common defensive planning considerations outlined in Chapter 8 apply to planning for base security. The following paragraphs explain fundamental principles of rear area and base security. They also address BOS specific planning considerations that apply to base security.
E-70. The fundamentals of base defense are—
Understand the enemy.
See the AO.
Use the defender's advantages.
Concentrate at critical times and places.
Conduct counterreconnaissance and counterattacks.
Coordinate critical defense assets.
Balance base security with political and legal constraints.
Know the ROE.
Responsiveness.
E-71. Understand the Enemy. Defenders must be familiar with the capabilities and limitation of enemy forces, weapons, equipment, and tactics. The base commander also must have access to the latest intelligence concerning probable enemy intent.
E-72. See the AO. Intelligence operations are key to assembling an accurate picture of the AO. The IPB process provides the commander a continuous, integrated, and comprehensive analysis of the effects of enemy and neutral capabilities, terrain, and weather on operations. It helps the commander anticipate events and develop the priority intelligence requirements and information requirements tied to those events. Intelligence and multidiscipline counterintelligence estimates are prepared, continuously updated, and integrated into the base commander's staff decision making process. Space-based, airborne, and ground sensors, patrols, and counterintelligence activities are all means that rear area commanders can employ to detect possible indicators of planned enemy action.
E-73. Use the Defender's Advantages. Defender's advantages may permit a numerically inferior force to defeat a much larger one. Some of these advantages are:
The ability to fight from cover.
More detailed knowledge of local terrain and environment.
The ability to prepare positions, routes between them, obstacles, and fields of fire in advance.
The ability to plan communications, control measures, indirect fires, and logistic support to fit any predictable situation.
The ability to deceive enemy forces about friendly defensive capabilities, dispositions, and execution of operations.
E-74. Concentrate at Critical Times and Places. A base commander must measure and continually evaluate the various risks to his base. An enemy usually concentrates his resources on the most sensitive or vulnerable targets. Defense of a base is normally conducted along interior lines, permitting the timely and secure movement of forces to engage the most critical threats. The commander must mass enough combat power at points of decision by economizing in some areas, employing a reserve, and maneuvering to gain local superiority at critical points.
E-75. Conduct Counterreconnaissance and Counterattacks. A major contributing factor to vulnerability in the rear area is the relatively fixed nature of operations. An enemy can study the operational patterns of semifixed units and installations to determine their existing defensive measures. Further, fixed bases having well-established perimeters usually have limited depth. Counterreconnaissance and counterattack add depth to the battle outside the perimeter, allowing the base to continue its primary mission with minimal interference.
E-76. Coordinate Critical Defense Assets. Synchronization of indirect fires, air and missile defense resources, tactical aircraft, engineers, dismounted troops, armored vehicles, naval surface fire support, and helicopters can produce a combined arms effect. Synchronizing forces and fires produces a synergy capable of defeating a larger enemy force. This synergy results from making enemy movement difficult or impossible and by causing a reaction that may make enemy forces more vulnerable to other friendly capabilities. Periodic rehearsals of security plans ensure effectiveness of the alert system, proficiency of key individuals, and identification of potential problem areas.
E-77. Balance Base Security with Political and Legal Constraints. Base security may have to be designed around numerous political constraints.
E-78. Know the ROE. The base commander and his subordinates must comply with established ROE. He ensures the reconciliation of any inconsistencies between service component and multinational ROE.
E-79. Responsiveness. The echelon rear area commander and his subordinate base cluster and base commanders have the authority and the capability to communicate operational requirements directly to units located within their AOs. The chain of command frequently changes from the functional to the tactical chain of command after implementing a rear area and base security plan. Therefore, the rear area commander must critically analyze and test his communication systems that filter through various levels of command to assure that they are responsive under given emergency conditions. The echelon rear area commander establishes direct communication links between the echelon rear command post and its subordinate base cluster and base operations centers if existing information systems are not adequate to transmit rear area and base security-related information to those centers in a timely manner.
E-80. Responsiveness may be attained by many different procedures and capabilities, some of which are listed below:
Clearly established authority granted to base cluster and base commanders.
A wide-area information system that provides a flexible warning system for a large variety of situations.
Continuous identification and tracking of resources that can assist in providing rear area and base security, such as maintenance float weapon systems and replacement crews.
Response forces have communication systems capable of using the existing wide-area information systems to communicate directly with the threatened BDOC. They also can communicate with the BCOC located in the threatened base cluster and the echelon rear command post.
MP forces responding to Level II rear area threats have combat vehicles with a mixture of firepower, armor protection, and a high degree of tactical mobility.
Identifying dual-capable units. For example, a rear area security force identified to respond to Level I or Level II threats also has capabilities to perform rescue or provide labor in an ADC mission. However, a rear area security element is not concurrently identified as an ADC element.
E-81. When the rear area commander commits his forces to semifixed installations or sites, the rear area security mission may become defensive in nature. Therefore, he must carefully balance his approach with the need for offensive action. Detecting enemy activity early is critical when conducting rear area security; it provides the commander with time to react to any threat. Proper integration of the BOS is key to successful operations.
E-82. Intelligence. A review is made of all available information about the general area before occupying a site. The IPB process addressing the rear area includes not only enemy information, but terrain, weather, and information about the civilian population and infrastructure. Intelligence, cavalry, scout, and CA organizations obtain relevant information about the area from host nation governmental organizations and the civilian population.
E-83. In the commander's visualization of the factors of METT-TC for the rear area security mission, he focuses on the enemy situation to determine how to organize and conduct the mission. Tactical intelligence is the key to defeating enemy operations directed against friendly sustaining operations. It provides the commander with information on current and possible future enemy locations, activities, strengths, weaknesses, and plans, which helps him seize the initiative. The commander should exploit all relevant sources of information within his AO, including information provided by civilian agencies and individuals. The IPB process is a vital part of answering the commander's intelligence requirements which include—
Size and capabilities of enemy forces within the commander's AO.
Natural defensive characteristics of the terrain.
Movement corridors throughout the AO for mounted and dismounted operations.
Conditions of existing roads, railways, pipelines, and waterways for use as both military LOCs and civilian commerce.
Proximity of enemy forces to critical facilities and installations, such as airfields, power generation plants, petroleum tank farms, and civic buildings.
E-84. Maneuver. The commander should not employ any organization in a role or configuration for which it is not principally designed unless such action is unavoidable. Rear area commanders employ the defensive potential of CS and CSS units to counter enemy actions. The defensive potential of each unit is that portion of a CS or CSS unit that may be used to provide rear area and base security with minimum degradation to overall mission capability. The echelon commander does not divert his combat forces to provide rear area and base security unless required by the factors of METT-TC. The rear area commander takes maximum advantage of host nation capabilities to provide response forces and TCFs.
E-85. Site selection is also an important factor in planning rear area and base security. Combat support and CSS operational requirements do not correspond to security requirements. Supporting units need a good road net, ready source of labor, storage areas, and other facilities that are available in established commercial areas. However, such placement decreases the security capabilities. The best site, from a security standpoint-given no air threat-is in a cleared area, occupying high ground with sufficient vegetation to conceal base facilities from observation. The worst site contains complex terrain and large numbers of noncombatants. The former extremely limits observation and fields of fire from the base and the latter limits the firepower that can be employed to defend the base. The most common tendency is to occupy the low ground through which most roads run, a balance between operational requirements and security requirements. A commander can justify the cost, time, and manpower needed to relocate a site to more defensible terrain rather than secure a poor position. The base commander locates his base in a place that enhances its physical security. The base cluster and echelon rear area commanders must approve the location.
E-86. Forces engaged in rear area security must be flexible and able to adapt to rapidly changing tactical situations. Rear area and base security are normally the domain of small units. The organization of forces for base defense also differs, depending on how the commander plans to accomplish his mission. The base commander task-organizes his forces into combined arms elements to counter the level of enemy capabilities as determined by his intelligence assets. This enables him to find the enemy with the smallest possible element, maintain contact without risking the destruction of the element in contact before it can receive outside support, and mass his combat power rapidly to destroy the detected enemy.
E-87. All security measures must have an inherent offensive capability. The echelon TCF, response forces provided by echelon MP and other assets, and local security measures undertaken by bases and base clusters contain the rear area commander's offensive capabilities. The base commander uses the potential combat power available within CS and CSS units located within his AO to provide those local security measures. He organizes and trains that identified potential combat power to conduct limited offensive operations against confirmed enemy Level I threats that threaten his bases and base clusters.
E-88. Absent a direct enemy threat, there is a tendency to relax security measures after completing the base's fighting and survivability positions. However, well-established security patterns allow enemy elements to reconnoiter the base and determine its points of vulnerability with little risk.
E-89. The base commander designates reconnaissance and patrol areas outside the base's perimeter to provide additional security if allowed to do so by the host nation. The objective is to provide the base additional early warning.
E-90. The factors of METT-TC and unit capabilities determine the specific security element tasks of subordinate maneuver units. For example, mounted forces are more suited to secure key points, such as major road junctions, bridges, tunnels, canal locks, dams, and power plants; while dismounted forces are well-suited for securing areas containing restricted terrain or large numbers of civilians.
E-91. The base commander should plan to use only the minimum firepower required to accomplish the base security mission. While his right to self-defense is never denied, it may be limited in some manner. For example, unlimited use of firepower that negatively affects civilians in the secured area may cause them to embrace the enemy's cause or withhold support to the friendly force. Soldiers must understand this and follow strict ROE when conducting sustaining operations.
E-92. Because of the decentralized nature of sustaining operations and the intermingling of military forces and civilians, the commander must address fratricide prevention when planning for rear area and base security. Fires that miss their intended targets can affect other forces, routes, and installations in the secured area. When considering a COA, the commander weighs the risk of fratricide against losses to enemy fire.
E-93. Fire Support. Artillery and mortars, if available, are the fastest means of responding to intruders beyond the base perimeter in the absence of maneuver forces positioned there. The commander desires the designation of a free-fire area beyond the base perimeter to allow for the optimum employment of available fire support systems. He positions no-fire or restricted fire areas over locations occupied by civilians and friendly forces operating outside the base, such as patrols and observation posts. These areas are large enough to provide the necessary degree of standoff protection.
E-94. Air Defense. Air and missile attacks are perhaps the greatest threats to units in the rear area. Rear area bases normally rely on passive air defense for protection against enemy air threats. Most rear area bases will not be supported by SHORAD systems. They will normally be located within the coverage provide by high- to medium-altitude air defense (HIMAD) systems. They will not normally control the positioning of HIMAD systems. (Chapter 8 discusses passive and active air defense considerations. Ballistic missile defense is an operational-level task addressed in FM 3-01.12.)
E-95. Mobility/Countermobility/Survivability. The commander directs the construction and improvement of perimeter barriers. This includes establishing clear fields of fire and implementing physical security measures, such as checkpoints on vehicle and pedestrian routes leading into the base, to improve overall base security. Barriers, natural obstacles, and aggressive offensive actions deny enemy access to the area immediately surrounding the base. If the force keeps the enemy at a distance, he cannot launch damaging attacks toward the base. The commander continues to direct improvement in his base defenses, as time and other resource permit, to ensure a stable security system.
E-96. Force protection considerations against terrorist attack are part of base defense planning. The base commander assesses the vulnerability of the base to terrorist attack and other nonbattlefield threats. He must assess the base's vulnerability to each identified threat. Risk and vulnerability assessments are the foundation for priorities of work and resource distribution.
E-97. The base defense plan includes those ADC measures necessary to minimize damage to the base's critical facilities resulting from fire, natural disaster, or enemy action. The commander dedicates resources to protect areas that, if destroyed, could cause catastrophic loss or mission failure since force protection resources are limited. The plan delineates responsibilities for ADC activities, such as fire fighting, light rescue and labor, and decontamination, and assigns appropriate priorities for assistance furnished by each unit on the base.
E-98. Combat Service Support. Since base security forces generally operate in close proximity to the base, the commander tailors the load carried by his dismounted elements to the immediate requirements of METT-TC. Resupply of dismounted elements takes place using ground or air modes.
E-99. Command and Control. Planning for rear area and base security operations, like all planning, requires the rear area commander to have an accurate common operational picture of his AO. This includes the strength and security potential of available units, terrain and environmental data, and intelligence information. The rear area commander uses existing echelon rear command posts and information systems to provide him and his subordinate commanders that common operational picture.
E-100. In planning for base security, a simple, flexible defensive plan disseminated to the lowest level of command is normally the best COA. The plan should include the maximum use of standing operating procedures (SOPs) and battle drills at the user level. It should incorporate adequate control measures to ensure the safety of friendly troops and civilians. Such a plan minimizes the impact of the inevitable miscues that accompany any combat operation.
E-101. The base commander integrates the base security plans with those of its base cluster and supporting rear area security forces. He periodically reviews the base defense plan. Alterations in the units assigned to the base and changes to their defense capabilities because of mission requirements also require updating the base defense plan. Frequent alterations of base security procedures reduce the base's vulnerability. The continuous monitoring of plans also allows adjustments based on experience to be incorporated into those plans.
E-102. The base commander establishes communications with the BCOC (or the echelon rear command post if the base in not part of a base cluster). He also establishes communications with the headquarters of the designated Level II response force.
E-103. Communication problems can occur in information exchanges during the planning for base security involving multinational forces. The commander must address any language barriers because units operating in the rear area normally need to communicate with various host nation governmental agencies and the civilian population. The ability to communicate with these different agencies and the local population helps to protect the force.
E-104. The echelon rear area commander maintains simplicity by making the minimum number of plans necessary. Rear area and base security is a secondary mission for CS and CSS units. The echelon rear command post, BCOC, and the BDOC must ensure that rear area and base security is not neglected in favor of the parent organization's primary mission. A BDOC sends out liaison teams to each base in its base cluster, with RAOC assistance, to ensure that each base's defensive plans are workable, coordinated with the BCOC, and routinely practiced.
E-105. Preparing for base defense begins before base units arrive, if possible. Normally, combat units provide the initial defense in the base area, as they are the first forces into an area. An exception may occur when conducting force projection operations supported by a host nation. In this case, the host nation's forces are the first forces into the area. These forces can be conventional military forces or police and internal security forces.
E-106. The rear area commander uses his available resources to initiate an area reconnaissance to determine the physical characteristics of the area and the presence or absence of enemy forces. Since rear area and base security is normally an economy of force measure, it is unlikely that sufficient forces will be available to secure the echelon's entire rear area at one time. Therefore, they concentrate on those areas immediately adjacent to the protected element, such as friendly forces. It is essential that base, base cluster, and other rear area security forces conduct continuous reconnaissance operations. They may focus their efforts on people, materiel, buildings, or terrain.
E-107. Reconnaissance operations that involve only US forces may not be effective if language problems prevent communication with the local population. In these instances, interpreters-US Army or host nation-should accompany forces conducting reconnaissance. When possible, host nation authorities, such as the civil police, should also accompany the reconnaissance force. Distributing leaflets and handbills before or during an area reconnaissance and using loudspeaker teams during the reconnaissance can aid the reconnaissance effort by informing civilians of what information the US reconnaissance force is seeking and how they can report that information to US forces.
E-108. The rear area commander directs units within his AO to establish bases and base clusters even while this initial area reconnaissance is ongoing. These bases and base clusters provide security to units located within them and can provide perimeter security around critical locations. Perimeters vary in shape depending on the factors of METT-TC. The perimeter shape conforms to the terrain features that offer the best use of observation and field of fire.
E-109. When the units constituting the base arrive, they immediately start organizing the defense of the base. Many tasks occur simultaneously, but some may require priority. The base commander specifies the sequence for preparing the defense system. (Chapter 9 provides a recommended sequence in its discussion of the preparation for an area defense.)
E-110. Construction of personnel shelters throughout the billeting, administrative, and maintenance areas provides individual protection against standoff attacks. These shelters may vary in construction. Shipping containers, dugouts, and double-walled plywood shelters with sand or gravel fill, all with sandbag reinforcement and overhead cover, provide acceptable protection. These shelters are close to the billets and work areas to permit rapid access. (To the degree possible, construction will be in consonance with the guidance provided in FM 3-34.34.)
E-111. Units may construct fighting positions or prefabricate and move them into position for assembly. These bunkers are constructed to withstand a direct hit by a medium antitank missile on the front and sides and a direct hit by a mortar on the top. Installing chain link fences around these positions can prematurely detonate shaped-charge warheads.
E-112. Constructing revetments for critical resources provides protection against mortar or rocket fragmentation. These revetments may be sand-filled, double-walled construction with either plywood or steel plate sides. Units within the base provide overhead cover for critical facilities and functions when possible. The base commander's preventive measures to avoid or minimize effects of enemy attacks also contribute to his ADC efforts by providing units, soldiers, facilities, and supplies on the base protection from major accidents and natural disasters as well.
E-113. The commander uses tactical wire barriers within the perimeter to limit and canalize penetrations by enemy groups or individuals. These interior barriers can be as simple as a single roll of concertina wire. Generally, the commander should place them to prevent a direct approach to vital facilities within the base. He should make provisions to cover these barriers by automatic weapons. The base should construct inconspicuous barriers and periodically relocate them to prevent counterplanning by the enemy. Further, the barriers should not be so intensive as to preclude freedom of movement by the reaction or reserve force. These forces, as well as all soldiers, should be familiarized with the location of all barriers through daylight and night drills.
E-114. Base defense training is an essential element of preparing to conduct a base defense. Base defense requires integrating the BDF and its emergency augmentation by all units on the base. Because they rarely function together, the commander can form an efficient fighting entity only through proper training. The BDF commander carefully coordinates the training of base units for base defense operations with the support operations of the base. All individuals receive training to allow them to participate, at least to a limited degree, in the base's defense. All units receive training to provide at least limited local security for the facilities they operate. Conducting rehearsals that test the base defense plan is an essential part of base defense training. Some equipment deemed necessary for base defense or for training purposes may not be available. The BDF commander must use his initiative to overcome these shortfalls.
E-115. Most of the training required to support base defense operations is currently a part of individual and unit training programs. Soldiers designated to take any part in base defense operations will probably require additional training in the following areas as applicable to their roles in the base defense effort:
Ambush techniques and defensive measures against enemy ambushes.
Use of hearing, sight, and smell as detection means.
Police-type patrolling and operating roadblocks and checkpoints.
Limited-visibility operations to include using night vision devises, sensors, and techniques for using sign and countersign procedures.
Marksmanship, especially night firing.
Observation post operations with emphasis on security, sound and light discipline, and reporting procedures.
Operation and operator maintenance of base defense equipment, such as sensors, night observation devices, radios, and computer systems.
Cross-training on all communications equipment available within the base and communication techniques.
Barrier construction and, if authorized, using mines and boobytraps.
Patrolling.
Small-unit attacks, such as the employing movement formations, rushes, and a base of fire.
Fire control and fire distribution of available weapons.
E-116. The existence of a common operational picture and the commander's situational understanding are the keys to knowing how and when a response force will be needed. Separate bases and base clusters establish continuous communications with the echelon rear command post to allow timely response and information dissemination.
E-117. The commander of the response force has a copy of the base defense plan so he can effect necessary coordination between the base and the response force once the latter is activated for the response mission. This coordination occurs through the BDOC. The response force commander coordinates with the base to ensure that he understands the base defense plan, to include—
Method of contacting the BDOC or BCOC, including call signs and frequencies.
Base defense plans and layouts to include—
Positions of critical internal assets, external coordination points, and no-fire areas.
Locations of any obstacles or mines near the base.
Locations and direction of fire of crew-served weapons.
Locations of target reference points and preplanned fires.
Locations of OPs and friendly patrols if employed by the base.
Signal for final protective fires.
How to obtain available fire support.
E-118. The response force commander designated for each base must have the capability to mass the effect of supporting fires and support TCF operations. He must know which fire support targets are approved for engagement and the locations of the nearest medical treatment facility, NBC decontamination site, and ammunition supply point. He must be able to communicate with—
Any supporting artillery and Army aviation units tasked to respond.
The TCF, BDOC, BCOC, and the echelon rear command post.
E-119. The preferred way to conduct a base defense is as an offensive operation designed to clear the area of enemy forces. Detecting and destroying significant enemy forces are responsibilities of the echelon rear area commander. However, the individual conducting rear area security may be forced to adopt a primarily defensive posture because of—
The size of the rear area.
A lack of resources.
Inability to detect and track the enemy.
Enemy capabilities in relation to the friendly force capabilities.
E-120. Forces engaged solely in base defense operations conduct aggressive patrols, develop and occupy defensive positions within their assigned AOs, and provide security forces to counter enemy attacks. These actions may be multiservice or multinational depending on the composition of the base.
E-121. Rear area commanders at all echelons request ground maneuver forces to use as BDFs when the net effect of enemy activities in the echelon's rear area is beyond the limited defensive capabilities of CS or CSS resources. If a threat exceeds a base's ability to defend itself, the base commander requests response force support through his BCOC or the echelon rear command post if he commands a separate base.
E-122. The conduct of base defensive operations against a ground attack is the same as for conducting a perimeter defense. (Chapter 8 discusses the perimeter defense.) The paragraphs below discuss those execution considerations unique to base defense.
E-123. Base defense operations to counter small enemy forces include aggressive, frequent patrolling by squad- and platoon-size forces to detect and capture or destroy small enemy bands. Host nation personnel are well suited to assist BDF patrols. Their knowledge of the terrain, inherent ability to operate effectively in the environment, language skills, and familiarity with local customs increases the effectiveness of these patrols.
E-124. Small, highly mobile units conduct patrols by moving on foot or by land, water, or air vehicles during daylight and darkness. They search populated areas contiguous to the base and establish surprise checkpoints along known or suspected routes used by enemy forces.
E-125. The BDF mans dug-in or concealed night ambush sites located outside of the base's external barrier system on a random basis. Host nation security personnel should accompany patrols traveling through populated areas. The base develops fire support targets to support the ambush in accordance with their availability and the ROE. If the area adjacent to the base perimeter is a free fire area, it is seldom necessary to occupy ambush sites there. When local restrictions preclude establishing a free-fire area, ambush sites are manned forward of the perimeter and the BDF is prepared to assist those elements conducting the ambush as necessary.
E-126. Patrols can install sensors in locations enemy forces threatening the base would cross to provide early warning of enemy movements. Such patrols also observe and report enemy activities, such as assembling personnel; moving weapons, amunition, or other supplies; and preparing firing positions for indirect-fire weapons. In addition to the acquisition of specific targets, patrols may confirm or deny the presence of enemy activity in named areas of interest located near to base.
E-127. The base uses any available small boats to patrol nearby rivers and coasts. An infiltrating enemy takes advantage of waterways to transport heavy weapons because of their weight and bulk. Detecting these weapon systems is an important river and coastal surveillance mission for the BDF commander. The Army has type-classified small watercraft suitable for use in this type of patrol, as does the Navy and Coast Guard.
E-128. Military working dogs are a valuable asset in base defense operations. Their employment should habitually be considered in planning all patrol and security operations. Successfully using these dogs depends on the skill of the handler and the knowledge and full understanding of the capabilities and limitations of the dogs by employing commanders and staffs. (Army Regulation 190-12 provides this information.)
E-129. During base security operations, the base commander monitors the location of friendly troops and their relationship to friendly fires. The base commander must be constantly aware of the relative location of enemy, friendly, and neutral personnel. Subordinate elements, such as patrols, must understand the importance of accurately reporting their positions. Automation and navigation aids, such as the global positioning system (GPS) tied to combat net radios, assist in maintaining a common operational picture. When employing artillery, mortars, and air support, the commander must exercise positive control, whereby an observer must be able to see the target area. Unit SOP at all levels must address specific procedures for clearing indirect fires directed against identified targets located within the rear area.
E-130. The static positions of the base defense consist primarily of the bunkers and towers forming the base's defensive positions. Positioning bunkers and towers correctly affords maximum observation and mutually supporting fires over the area forward of the perimeter to include the perimeter barrier and sensor system.
E-131. The base commander establishes communications between the BDOC, the command posts of the units occupying the base, and the base's bunkers, towers, and reserve. In addition, each node be able to communicate laterally with adjacent units and defensive positions.
E-132. Bunkers. Although full-time observation and all-around defense of the base are essential, the BDF commander may reduce the number of soldiers conducting static defense mission by designating key bunkers around the perimeter to be manned at all times, with the remainder to be fully manned during periods of reduced visibility and increased enemy threat. The base prepares individual fighting positions near the bunkers to provide supporting fires. Night vision devices, binoculars, automatic weapons, grenade launchers, and hand grenades are commonly available within the bunker positions, and antitank systems cover possible ground vehicle approaches.
E-133. Towers. Towers provide increased visibility, which may be desired in specific situations. Elevated platforms enhance the capability of detecting perimeter infiltration when coupled with night vision devices, binoculars, and spotter scopes. They may enhance the base's ability to determine the firing positions of enemy indirect weapon systems. Towers can be constructed according to standard military design using standard construction materiels or constructed from local materiels. Multistory buildings, such as grain silos, can also serve as towers. Installating sandbags or steel plating around the observation platform provides protection against automatic weapons and small-arms fire. Constructing a ground-level bunker near the base of the tower provides additional protection when the enemy directs fires against the tower. Access to the bunker from the tower may be by means of a fireman's pole or a ladder. Towers should incorporate the following safety measures—
Lightning arresters.
Built to withstand strong winds and to support two observers and their equipment.
Enclosed mounting ladder.
Provision of safety nets around tall towers.
Painted an appropriate color to reduce reflection from moonlight.
Installation of a suitable roof to shield observers from the elements without interference to observation. (A double-roof design can cause some types of mortar rounds to detonate at a height that affords some protection to the observers positioned in the tower.)
The base commander's decision to use towers is a result of his analysis of the factors of METT-TC. For example, he must decide if the additional security they provide is worth the effort to construct them in a fluid situation or the risk that they will attract additional enemy attention to the base.
E-134. Reaction operations are operations conducted by the BDF, operating from the base or from positions outside the base, for the purpose of countering local enemy activities. They are offensive in nature and conducted as either spoiling attacks or counterattacks.
E-135. The commander uses his BDF to destroy any small enemy units detected in the vicinity of the base. The base requests assistance if its forces cannot destroy or contain the enemy force in its current location. Elements of the BDF do not pursue a retrograding enemy outside of supporting distance from the base, because it could be part of a diversion designed to weaken the base's defensive capabilities. Pursuit of such fleeing enemy forces is turned over to rear area response forces instead.
E-136. Reaction operations are simple, planned, and rehearsed because the majority of actions are required at night. Designating primary and alternate checkpoints within the base facilitates response to multiple contingencies. Within security limitations, the force uses actual checkpoints during rehearsals to promote familiarity with the area and the reaction plan.
E-137. Response force operations are offensive operations conducted by the response force to countering Level II attacks. The response force moves quickly to counter the enemy before he can extensively damage the base. The base commander lifts or shifts base defense fires to support the maneuver of the response force. The response force attempts to delay and disrupt the threat until a TCF arrives if it cannot destroy or deter the enemy. The base commander notifies his BCOC if the base defense and the response forces engage an enemy they cannot defeat. They maintain contact with the enemy force until the TCF arrives. The TCF commander has operational control (OPCON) of all base and response forces within his designated AO on commitment of the TCF.
E-138. The BDF commander integrates available host nation and third country forces in the overall base defense effort. Particular emphasis is placed on integrating host country forces in patrol and population control activities. Both host nation and third country forces provide local security for their own units. However, to ensure maximum benefit, all such local plans should be coordinated with and integrated in the base defense plan. The actual degree of host nation and third country force participation in base defense depends on the orders and guidance of their respective governments and the personal relationship their commanders have with the base commander.
E-139. An enemy may conduct an attack by fire against a base when he knows that he is unable to penetrate the base perimeter. He wants to place a large volume of fire on the base to inflict casualties and destroy resources. Such an attack is normally of short duration, from 10 to 20 minutes. He may also direct harassing fires toward the base to accomplish the same purpose. The weapon systems delivering these attacks normally displace after completing their mission to prevent their destruction by friendly maneuver, and direct fires, and counterfires.
E-140. The base develops an aggressive reconnaissance and surveillance plan to detect the infiltration of enemy mortars, artillery, rockets, and antitank systems and to locate firing positions. The BDF commander considers likely firing positions and routes to them, intelligence reports, and available resources when formulating this plan. He plans offensive opertions to locate and destroy the enemy force prior to, during, and after such attacks and passive defensive actions to reduce friendly casualties and damage associated with them.
E-141. Primary active measures employed against these types of attack are airborne observers, establishing a critical friendly zone (CFZ) over the base, and using reaction forces. An unmanned aerial vehicle or attack helicopter may provide the airborne observer. The airborne observer orbits the base area, checking likely or suspected positions and noticeable changes in the terrain. The base acts against an enemy weapon system on its discovery by employing friendly fire support systems or maneuver forces against it. A CFZ over the base allows friendly counterfires against the enemy weapon system as soon as it attacks the base. In the absence of radar coverage, the base may use visual observation of the muzzle blast from two or more points to provide an intersection. This requires these observation posts to have properly oriented azimuth boards so the direction of sightings can be rapidly determined and reported to the BDOC. Using a reaction force deployed by helicopter or tactical vehicle to engage and destroy the enemy weapon system is a primary consideration. The reaction force must be careful to prevent establishing a pattern, such as always using the same route or landing zone. If the enemy is aware of the pattern, he can set up an ambush to destroy the reaction force.
E-142. Sniper teams are useful when forces come under harassing small-arms fire by a small enemy element firing from, among, or near areas where civilians or cultural monuments protect it from the return fires of more nondiscriminating weapons. These teams allow the BDF commander to fix the enemy and move other BDF elements into positions where they can engage the enemy without endangering civilian lives or causing excessive collateral damage. The commander can employ smoke and, if authorized, riot-control agents to aid in this maneuver. If the force cannot engage the enemy without endangering civilian life or property, the BDF commander can try to disengage his forces and move them to positions that block the enemy's escape routes. However, the base commander must use all available means to protect his forces, even when it may place civilians at risk.
E-143. These teams may be provided from infantry units. Alternatively, this capability may be provided by giving special training to selected BDF soldiers to maximized the capabilities of their assigned individual weapons or specialized equipment provided to them.
E-144. Passive defense measures are always practiced within the confines of the base. In addition, the commander employs CA and PSYOP programs to ensure the cooperation of the local civilian population. The BDOC evaluates all patrol, guard, and intelligence reports indicating an attack. Preparation of firing or assault positions, movement of weapons or ammunition, unusual actions or movement of the civilian population, and reports by host nation personnel may be indications of an attack.
E-145. When an attack occurs, the objective is to resume operations, including the maintaining or restoring of control, evacuating casualties, isolating danger areas, and reducing personnel and materiel losses. The base commander conducts an immediate survey of the damage and reports his assessment to the BCOC. Simultaneously, he initiates actions to isolate the danger areas and prevent extension or continuation of the damage, such as fighting fires and minimizing flooding.
E-146. Casualties receive self-, buddy-, and first aid care. If possible, medical personnel and vehicles evacuate casualties. However, timely transportation of casualties is important. The situation may require using nonmedical vehicles for mass casualties. If possible, medical personnel accompany those patients being transported in nonmedical vehicles to provide en route patient care.
E-147. The base establishes traffic control using MP or other elements to ensure fire-fighting equipment gains access to the area and ambulances and evacuation vehicles clear the area. The BDOC notifies the BCOC of blocked routes and necessary traffic diversions. The element conducting traffic control can also temporarily provide for controlling displaced civilians and stragglers and provide a degree of local security for the damaged area.
E-148. The BDOC coordinates with the BCOC and echelon rear command post for engineer support to restore critical facilities and any specialized fire fighting capabilities required. Engineer support is normally needed to clear debris and rubble to support the base damage control mission and extinguish extensive fires. The BDOC also coordinates for any necessary explosive ordnance disposal (EOD) and decontamination support.
E-149. The base commander takes precautions by maintaining local security and interior guard posts when receiving ADC support from host nation resources to ensure the security of the base. He cannot afford confusion surrounding the base's damage control efforts to provide an opportunity for saboteurs and other hostile personnel to penetrate the base perimeter.
E-150. Route security operations are a specialized kind of area security operations conducted to protect lines of communication and friendly forces moving along them. Enemy attempts to interdict LOCs may have little immediate impact on ongoing decisive and shaping operations because of unit basic loads and previously positioned caches. However, the security of those routes over which the echelon's sustaining operations flow is critical to sustained land operations, regardless of whether the commander is attempting to exploit success or recoup from failure.
E-151. The security of routes and LOCs, whether rail, pipeline, highway, or waterway, presents one of the greatest security problems in an echelon's rear area. Route security operations are defensive in nature and are terrain-oriented. A route security force prevents an enemy force from impeding, harassing, or destroying traffic along the route or portions of the route itself. Having a base permits the concentration of security resources. LOC security requires dedicated resources at almost infinite points or reaction forces to counter possible enemy action. Units performing missions that require the habitual use of LOCs, such as MP, transportation, supply, and service units, can perform route security operations in conjunction with their primary activities. The echelon rear area commander can employ the following techniques to provide route security:
Passive security.
Route reconnaissance.
Cordon security.
Combat security.
While the scope of these operations depends on the factors of METT-TC, route security operations tend to require significant resources. A combination of passive and route reconnaissance is commonly used over secured routes such as a LOC.
E-152. The passive security technique for provide route security includes measures initiated to achieve security without a significant expenditure of manpower or resources. It includes—
Camouflage
Formation and march control of convoys so they present the least lucrative target possible under prevailing conditions.
Proper selection of routes.
Capitalizing on security offered by other activities not related to the route's security requirements. These activities include aircraft traversing the route, maintenance activities taking place along the route, training exercises or troop movements adjacent to or along the route, military and host nation police traffic control activities, and the activities of the civilian population.
Defensive information operations.
E-153. The commander uses passive security for all conditions or situations and as an adjunct to any other technique of route security employed. They are the products of a long-term and continually improved program for an integrated security system.
E-154. Route reconnaissance addresses not only the route itself, but also all terrain along the route from which the enemy could influence a friendly force's movement. Route reconnaissance takes place at irregular intervals to avoid developing a regular pattern that an enemy could exploit. (Chapter 13 discusses route reconnaissance.)
E-155. It is normally not feasible to secure all points on a route by physically allocating resources to each point. Cordon security is the security provided between two combat outposts positioned to provide mutual support. A commander can assign air assault, mechanized, or motorized units to combat outposts established at critical locations along the route. He locates these combat outposts within supporting distance of each other whenever possible. Units assigned to these combat outposts provide response forces in the event of enemy activity along the route within their assigned AO. Forces based at these combat outposts conduct reconnaissance patrols and offensive operations to counter enemy activities between these two points on a frequent but irregular schedule. Cordon security requires considerable manpower and other resources. The commander uses it only when a clear and evident requirement exists.
E-156. Normally, each combat outpost contains at least a platoon-size element equipped with automatic weapons, communications, and sensors and supported by those fire support assets available to the rear area commander. (Chapter 12 contains additional information on the combat outpost.) The outpost commander rotates his soldiers between duty at the combat outpost and duty on patrol. The higher commander contacts each of his deployed combat outposts frequently to check its status.
E-157. The establishment of cordon security will do little to eliminate the rear area threats that require its adoption. A commander directing the establishment of cordon security should also direct a series of parallel corrective actions, to include—
Searching for a new route.
Vigorous search and attack operations to destroy the enemy within the echelon rear area.
Rigorously enforcing circulation control measures in coordination with the host nation over the civilian population.
Removing cover from areas offering concealment to an enemy.
Constructing new routes to bypass dangerous areas.
Repositioning supply activities to permit better route selection.
Mass evacuation of the civilian population from towns and villages along the route. (This is an extreme measure and requires consultation with host nation authorities and adherence to the laws of land warfare.)
E-158. The commander must recognize the loss of complete control over any given route early. The continued investment of resources into a "lost route" merely serves the enemy. Those resources and energy should be diverted to security measures elsewhere whenever feasible.
E-159. The combat security technique for providing route security includes all measures taken by combat arms units to seize and secure the terrain necessary to permit use of the route in question. Units conduct combat security along a route to prevent enemy ground forces from moving into direct fire range of the protected route. The route and its adjoining terrain compose the AO. A route security force operates on and to the flanks of a designated route.
E-160. Combat security is the most costly technique for providing route security and draws on the strength of the maneuver force. For example, because of the distances involved, a commander usually assigns at least one battalion-size unit, if not more, to secure one route through a division-size AO. The maneuver force establishes a perimeter around the route or cordons sections of it to search suspected enemy locations while establishing roadblocks and checkpoints along the main route and lateral routes to stop and search vehicles and people as they enter or leave the route. Special considerations include coordinating with segments manned by rear area security forces and the echelon rear command posts integrating the maneuver force's operations with other rear area and base defense activities, and clarifying of C2 arrangements.
E-161. Convoy security operations are specialized area security operations conducted to protect convoys. Units conduct convoy security operations anytime there are not enough friendly forces to continuously secure LOCs in an AO and there is a significant danger of enemy ground action directed against the convoy. The commander may also conduct them in conjunction with route security operations. A convoy security force operates to the front, flanks, and rear of a convoy element moving along a designated route. Convoy security operations are offensive in nature and orient on the force being protected. (Chapter 14 discusses convoy movement operations; this section only addresses convoy security concerns.)
E-162. To protect a convoy, the convoy escort element must accomplish the following critical tasks:
Reconnoiter the convoy route.
Clear the route of obstacles or positions from which the enemy could affect movement along the route.
Provide early warning of enemy presence along the route.
Prevent the enemy from attacking the convoy.
E-163. The size of the escort needed to conduct convoy security operations is METT-TC dependent. However, as a general rule, an average-size convoy of 50 vehicles normally requires at least a maneuver company, an MP company, or air defense artillery battery equipped with self-propelled cannons to conduct the mission. Without such an escort, the transportation unit will have to provide security using its organic assets. This results in the reduction of cargo-hauling capabilities of each transportation unit to the degree that it must convert cargo vehicles into ad hoc gun trucks and leave other trucks in a motor pool because of their drivers being diverted to provide the necessary degree of security.
E-164. Cavalry, tank, mechanized infantry units, and MP elements equipped with tracked or wheeled armored vehicles are well suited to protect a convoy because of their organic reconnaissance capabilities and combat power. The commander may reinforce the convoy security force with engineers, dedicated air defense, and other assets as required. Usually the convoy's trail party also provides CSS support to the convoy escort, such as vehicle recovery and medical evacuation. If the convoy's trail element cannot provide that support, then the convoy escort provides its own CSS support. Other METT-TC considerations, such as restrictive terrain and limited time, dictate how to use aviation assets as part of the coordinated effort.
E-165. The convoy security force organizes into several elements to accomplish its tasks. (See Figure E-6.) The advance guard performs a route reconnaissance forward of the convoy. The security element provides early warning and security to the convoy's flanks and rear. This element can also perform the duties of the escort element. The escort element provides close-in protection to the convoy. It may also provide an immediate response force to assist in repelling or destroying enemy forces if they engage the convoy. The rear guard prevents an enemy from overrunning the convoy from the rear. It can also act as an immediate response force to enemy contact made on either flank of the convoy. Finally, a reaction force is available to respond to emergencies. Since the reaction force is a committed force, and not a reserve, it is task organized to include available fire support assets and other combat multipliers. It provides firepower and support to all convoy elements to help develop the situation, conduct a hasty attack, or prevent the convoy's destruction. The headquarters directing the convoy, rather than the convoy commander, controls the reaction force. It monitors the progress of the convoy and responds if the convoy encounters an enemy unit the escort element cannot defeat or repel. It must be able to respond within 15 minutes. The reaction force always anticipates an ambush when moving to the relief of a convoy under enemy attack.
Figure E-6. Convoy Security Organization
E-166. When a lack of resources prevents establishing all five elements, the commander normally first resources his forward reconnaissance or advance guard. He then resources his escort, flank screening, and rear guard elements in that order. It is the responsibility of the headquarters directing the convoy to designate the response element.
E-167. If available, air cavalry assets can participate in the convoy security operation by screening the convoy's movement as it moves along the route of march. Alternatively, they can assist in clearing the route ahead of the convoy as it moves along the route of march, or clearing the route in conjunction with the route reconnaissance element. Air cavalry can also assist by controlling indirect-fire support and coordinating with forward air controllers from other services for close air support. The supporting air cavalry unit must know the maneuver intentions of the ground element if contact with the enemy occurs. If heavy forces are not available for use as a convoy escort, the commander can use light infantry to augment the self-defense capabilities of transportation units.
E-168. As shown in Figure E-7, convoy security control measures typically include the following:
Routes (primary and alternate).
Start point.
Release point.
Checkpoints.
Phase lines.
Observation posts.
Target reference points.
Areas of operation for various units that affect the convoy.
Staging or marshaling areas.
Known obstacles and lanes.
Figure E-7. Convoy Control Measures
E-169. Although convoy size, passage time, and march speed are not graphic control measures, they determine how long it takes to execute the convoy security mission. Rules of engagement are also not a graphic control measure, but they greatly influence how a commander conducts convoy security operations.
E-170. Because of the inherent dangers of convoy operations, the commander emphasizes security measures during the planning process. The best defense is to avoid being ambushed. These security measures include—
Secrecy when planning and disseminating orders.
Strict noise and light discipline during movement.
Varying routes and schedules.
Avoiding routes with known danger areas.
Conducting route reconnaissance using aerial and ground systems.
Using current intelligence information concerning the condition of the route and any enemy or other forces that may impact on the convoy's use of that route.
Coordinating with supporting air liaison officers to ensure the scheduling of close air support to assist the movement if the convoy warrants committing these assets.
Fire support elements to provide close and continuous fire support for the movement.
Training in immediate actions drills, including actions at danger areas and in case of a near ambush, a far ambush, booby traps, encounters with enemy tactical combat vehicles, sniper contact, aerial attack, and indirect fire.
Communications and coordination with supporting units and other units along the route, adjacent host nation forces, and higher headquarters, including airborne radio relay.
Various locations for leaders, communications, medical support, and weapon systems within the movement formation.
Questions asked of local civilians along the movement route for intelligence information, including possible enemy ambush sites.
E-171. The convoy commander must consider the unique requirements of convoy security when formulating his plan. He briefs his subordinates on the latest information regarding the enemy situation and the area through which the convoy will pass. He formulates his plan and issues his order, which includes the movement formation, intervals between echelons and vehicles, rate of travel, and a detailed plan of action if the convoy encounters an enemy force. Since there is seldom time to issue complicated orders during an ambush, subordinate commanders must plan the actions of the escort element and reaction force in the event of an ambush. Units should rehearse these actions before movement and execute them as drills if enemy contact takes place.
E-172. Communications are vital to the success of convoy movements. The convoy commander must plan for radio communication and ensure the availability and compatibility of communication means between convoy elements and indirect-fire support and air cavalry assets, as well as with units and host nation agencies in areas along the movement route. The convoy commander prearranges visual and sound signals, such as colored smoke, identification panels, whistles, or horns. Many of these signals can be SOP items. He must ensure that all convoy members understand these signals and rehearse the actions required by each. This is necessary because of the limited number of radios and other communications equipment in tactical vehicles.
E-173. The commander's fire support plan covers the entire convoy route, paying special attention to known danger areas and potential choke points. Convoy security elements may have mortars organic to the escort element or indirect fires provided by fire support elements positioned to range all or portions of the route. Coordinating with fire direction centers before the convoy's departure enables fire support teams in the convoy security element to enter the appropriate fire control nets, calling for and adjusting fires as necessary.
E-174. The convoy security commander must carefully plan for the appropriate CSS to support the operation. He should include fuel, maintenance, and recovery elements in the convoy or pre-position them in secure areas along the route. He also plans for casualty evacuation support that covers the entire route.
E-175. Convoy security operations in an urban environment or built-up area require different emphasis and techniques than those in rural areas. The population density and characteristics of the area may require using nonlethal weapons and carefully employing lethal weapons. When applying minimum-essential force to minimize loss of life and destruction of property, subordinate commanders must conduct detailed planning, coordination, and control. Whenever possible, convoys should move through populated areas when they are the least congested and, therefore, less dangerous to the security of the convoy. Convoy operations may require assistance from military or local police and other governmental agencies to secure the route before the convoy enters a built-up area.
E-176. The convoy commander must rehearse maintaining march intervals and actions on contact for a variety of scenarios, including air attack, artillery or indirect fire, snipers, and ambush. Since the purpose of a convoy is to reach its destination-not to destroy the enemy in a movement to contact-the goal of these responses should be to free the convoy from enemy contact so it can continue its mission. All soldiers and vehicles traveling in the convoy should undergo precombat inspections to ensure they know and adhere to unit SOP, and that vehicles have a reasonable expectation of completing the convoy without mechanical failure. During this stage, drivers act to harden their vehicles, such as adding sandbags and Kevlar blankets and cover loads to prevent an enemy from identifying the cargo. The convoy commander spaces prime targets throughout the convoy and cross-loads his trucks as much as feasible to avoid losing all of one type of supply, such as all artillery fuzes, if a single vehicle is destroyed.
E-177. If possible, the convoy commander and his key subordinates perform a route reconnaissance. Shortly before the convoy's departure, MPs or scouts should perform another route reconnaissance to determine current conditions. This last route reconnaissance should also remove or neutralize individual mines emplaced by the enemy that endanger the convoy.
E-178. Unless the security force encounters the enemy during the convoy, the convoy conducts operations as discussed in Chapter 14. If the forward reconnaissance element, advance guard, or flank screen first encounters the enemy, it performs those actions on contact discussed in Chapter 4. (Chapter 8 discusses the active and passive air defense measures a convoy can take.)
E-179. An enemy may use his fire support systems in an attempt to destroy convoys or to harass and interdict the movement of supplies and personnel. Artillery fires are either preplanned fires or fires called in and adjusted on a target of opportunity by a forward observer. The adjusted fires present the most complex problem, as the enemy can adjust the effects of his artillery fires to follow the actions of the convoy. The two active measures that a convoy can take against enemy artillery fires are using direct or indirect fires against the enemy forward observer, if his location can be identified and calling for counterfire if the direction and approximate distance to the enemy artillery system can be estimated.
E-180. The convoy commander has three passive options when the convoy comes under enemy artillery fire: halt in place, continue to march, or disperse quickly to concealed positions. Regardless of the option selected, the unit SOP should cover the action taken and the signal directing the action. The primary consideration is the immediate departure from the impact area. The convoy only halts when the artillery concentration is ahead of the convoy. The convoy commander looks for an alternate route around the impact area and the convoy should remain prepared to move out quickly. The mission or the terrain may require the convoy to continue through the beaten area. In this case, the convoy increases its speed of movement and spreads out to the maximum extent allowed by the terrain.
E-181. The convoy commander takes caution when receiving sniper fire to ensure that any return fire does not harm friendly troops or civilians in the area. The best reactive measures against sniper attack by a convoy are passive. Ensure all soldiers wear helmets and available body armor. Vehicles move through the area without stopping. Convoy escort personnel act as necessary to locate, suppress, and kill snipers in accordance with the ROE.
E-182. The very nature of an ambush-a surprise attack from a concealed position-places an ambushed convoy at a disadvantage. No single defensive measure, or combination of measures, prevents or effectively counters all ambushes. The training of the convoy elements directly relates to the effectiveness of counterambush measures. Immediate reaction and aggressive leadership are essential to limit casualties and damage to vehicles, cargo, and personnel. Small enemy forces are seldom able to contain an entire convoy in a single kill zone. This is due to the extensive road space occupied by even platoon-size convoys and because of the presence of security elements escorting the convoy. More often, an enemy is able to ambush only a part of a convoy-either the head, trail, or a section of the main body. Fire in the kill zone may be from only one side of the road, with a small holding force on the opposite side. An enemy frequently places mines and booby traps on the holding force side to contain the convoy in the kill zone. The part of the convoy that is in the kill zone and receiving fire must exit as quickly as possible if the road ahead is open. The security escort takes care in assaulting the main ambush forces because an enemy will commonly use mines and booby traps to protect his flanks.
E-183. The convoy leaves disable vehicles behind or, if they are blocking the road, pushes them out of the way with following vehicles. Combat vehicles providing escort to the convoy must not block convoy vehicles by halting in the traveled portion of the road to return fire. If the main body splits into two or more elements because of the ambush, those elements forward of the ambush site move to a secure location. Vehicles that have not entered the kill zone must not attempt to do so. They should stop, their personnel should dismount, take up a good defensive position, and await instructions. Since escort vehicles may have left the road to attempt to overrun a hostile position, elements of the convoy should not fire on suspected enemy positions without coordinating with the escort forces.
E-184. Other actions that the convoy commander can take to neutralize the ambushing enemy force include—
Calling for artillery fire on enemy positions.
Calling for attack helicopters to engage the enemy positions.
Directing the crew-served weapons mounted on convoy vehicles and the individual weapons of nondriving personnel to suppress the ambush force while the rest of the convoy's vehicles move out of the kill zone.
Calling for the reaction force.
E-185. A convoy with a limited escort is seldom able to defeat an ambushing enemy force and should not attempt to do so. When part of the convoy is isolated in the kill zone, vehicles that have not entered the ambush area must not attempt to do so. They should stop in a herring bone formation; personnel should dismount, take good defensive positions, and await instruction until supporting forces clear the ambush area. Normally, the transportation unit conducting the convoy will not maneuver to attack the enemy ambush force unless it is necessary for self-preservation. It relies on its escort force, fire support, and reaction forces.
E-186. Convoy personnel will dismount, take cover, and return fire on enemy positions when an element of a convoy halts in the kill zone and is unable to proceed because of disabled vehicles, damaged bridges, or other obstacles, Personnel dismount their vehicles away from the direction of enemy fire. Escorting security forces that have passed through the kill zone or have not yet entered the kill zone maneuver to destroy the ambushing element. The convoy commander calls for the reaction force as soon as the ambush occurs.
E-187. The convoy clears the route and movement resumes as soon as possible after the ambushing enemy force is defeated or withdraws. Wounded soldiers are evacuated using the fastest possible mode. When the convoy cannot tow disabled vehicles, it should distribute their cargo among other vehicles if time permits. The convoy destroys vehicles and cargo on order of the convoy commander if it is not feasible to evacuate them. The convoy recovers combat net radios and other critical items before it destroys the vehicles. These items should not fall into enemy hands.