 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| To move swiftly, strike vigorously, and secure all the fruits of victory, is the secret of successful war. |
| Thomas J. "Stonewall" Jackson, 1863 |
Offensive operations aim at destroying or defeating an enemy. Their purpose is to impose US will on the enemy and achieve decisive victory (FM 3-0). A commander may also conduct offensive operations to deprive the enemy of resources, seize decisive terrain, deceive or divert the enemy, develop intelligence, or hold an enemy in position. This chapter discusses the basics of the offense. The basics discussed in this chapter apply to all types of offensive operations.
3-1. The commander seizes, retains, and exploits the initiative when conducting offensive operations. Even in the defense, wresting the initiative from the enemy requires offensive operations.
3-2. Offensive operations are either force- or terrain-oriented. Force-oriented operations focus on the enemy. Terrain-oriented operations focus on seizing and retaining control of terrain and facilities.
3-3. Surprise, concentration, tempo, and audacity characterize the offense. Effective offensive operations capitalize on accurate intelligence and other relevant information regarding enemy forces, weather, and terrain. The commander maneuvers his forces to advantageous positions before contact. Security operations and defensive information operations keep or inhibit the enemy from acquiring accurate information about friendly forces. Contact with enemy forces before the decisive operation is deliberate, designed to shape the optimum situation for the decisive operation. The decisive operation is a sudden, shattering action that capitalizes on subordinate initiative and a common operational picture (COP) to expand throughout the area of operations (AO). The commander executes violently without hesitation to break the enemy's will or destroy him. FM 3-0 discusses the four characteristics of offensive operations.
3-4. The following vignette discusses the offensive operations of the 101st Airborne Division (Air Assault) during OPERATION DESERT STORM. The actions of the 101st Airborne Division between 24 and 28 February 1991 were a shaping operation for the XVIII Airborne Corps.
|
|
Types of Offensive Operations
|
3-5. The four types of offensive operations are movement to contact, attack, exploitation, and pursuit. Entry operations, while offensive in nature, are one of the six subordinate forms of force-projection operations. Force-projection operations are operational level tasks and fall outside the scope of this manual. Joint doctrine addresses force-projection operations. Appendix C addresses tactical airborne and air assault operations as vertical envelopments.
3-6. Movement to contact is a type of offensive operation designed to develop the situation and establish or regain contact (FM 3-0). The commander conducts a movement to contact (MTC) when the enemy situation is vague or not specific enough to conduct an attack. A search and attack is a specialized technique of conducting a movement to contact in an environment of noncontiguous AOs. Chapter 4 discusses MTC.
|
Forms of the Attack
|
3-7. An attack is an offensive operation that destroys or defeats enemy forces, seizes and secures terrain, or both (FM 3-0). Movement, supported by fires, characterizes the conduct of an attack. However, based on his analysis of the factors of METT-TC, the commander may decide to conduct an attack using only fires. An attack differs from a MTC because enemy main body dispositions are at least partially known, which allows the commander to achieve greater synchronization. This enables him to mass the effects of the attacking force's combat power more effectively in an attack than in a MTC.
3-8. Special purpose attacks are ambush, spoiling attack, counterattack, raid, feint, and demonstration. The commander's intent and the factors of METT-TC determine which of these forms of attack are employed. He can conduct each of these forms of attack, except for a raid, as either a hasty or a deliberate operation. Chapter 6 discusses the attack and its subordinate forms.
3-9. Exploitation is a type of offensive operation that rapidly follows a successful attack and is designed to disorganize the enemy in depth (FM 3-0). The objective of an exploitation is to complete the enemy's disintegration. Chapter 6 discusses exploitation.
3-10. A pursuit is an offensive operation designed to catch or cut off a hostile force attempting to escape, with the aim of destroying it (JP 1-02). A pursuit normally follows a successful exploitation. However, if it is apparent that enemy resistance has broken down entirely and the enemy is fleeing the battlefield, any other type or subordinate form of offensive operation can transition into a pursuit. Chapter 7 discusses the pursuit.
3-11. This section defines in alphabetical order those common offensive control measures that a commander uses to synchronize the effects of his combat power. The commander uses the minimum control measures required to successfully complete the mission while providing the flexibility needed to respond to changes in the situation.
3-12. An assault position is a covered and concealed position short of the objective from which final preparations are made to assault the objective. Ideally, it offers both cover and concealment. These final preparations can involve tactical considerations, such as a short halt to coordinate the final assault, reorganize to adjust to combat losses, or make necessary adjustments in the attacking force's dispositions. These preparations can also involve technical items, such as engineers conducting their final prepare-to-fire checks on obstacle clearing systems and the crews of plow- and roller-equipped tanks removing their locking pins. It may be located near to either a final coordination line (FCL) or a probable line of deployment (PLD). (Paragraphs 3-18 and 3-23 define a FCL and a PLD respectively.)
3-13. The assault time establishes the moment to attack the initial objectives throughout the geographical scope of the operation. It is imposed by the higher headquarters in operations to achieve simultaneous results by several different units. It synchronizes the moment the enemy feels the effects of friendly combat power. It is similar to the time-on-target control method for fire mission processing used by the field artillery. A commander uses it instead of a time of attack (defined in paragraph 3-26) because of the different distances that elements of his force must traverse, known obstacles, and differences in each unit's tactical mobility.
|
3-14. An attack-by-fire position designates the general position from which a unit conducts the tactical task of attack by fire. (Appendix B defines the tactical mission task of attack by fire.) The purpose of these positions is to mass the effects of direct fire systems for one or multiple locations toward the enemy. An attack-by-fire position does not indicate the specific site. Attack-by-fire positions are rarely applicable to units larger than company size. Figure 3-2 depicts attack-by-fire position BRANDON.
3-15. The attack position is the last position an attacking force occupies or passes through before crossing the line of departure. An attack position facilitates the deployment and last-minute coordination of the attacking force before it crosses the LD. It is located on the friendly side of the LD and offers cover and concealment for the attacking force. It is used primarily at battalion level and below. Whenever possible, units move through the attack position without stopping. An attacking unit occupies an attack position for a variety of reasons; for example, when the unit is waiting for specific results from preparatory fires or when it is necessary to conduct additional coordination, such as a forward passage of lines. If the attacking unit occupies the attack position, it stays there for the shortest amount of time possible to avoid offering the enemy a lucrative target. (Figure 3-3 shows attack positions BLUE and GOLD used in conjunction with other common offensive control measures.)
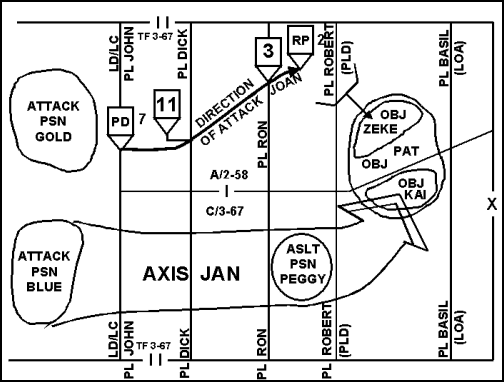
Figure 3-3. Attack Positions Used with Other Common Offensive Control Measures
|
3-16. An axis of advance designates the general area through which the bulk of a unit's combat power must move. There are three primary reasons why a commander uses an axis of advance. First, to direct the bypass of locations that could delay the progress of the advancing force, such as known contaminated areas. Second, to indicate that he does not require the force to clear the AO as it advances. His force will be required to clear the axis in accordance with specified bypass criteria. The third primary reason is to indicate to a unit involved in offensive encirclement, exploitation, or pursuit operations the need to move rapidly toward an objective. Figure 3-4 depicts axis of advance DEBRA.
3-17. The direction of attack is a specific direction or assigned route a force uses and does not deviate from when attacking. It is a restrictive control measure. The commander's use of a direction of attack maximizes his control over the movement of his unit, and he often uses it during night attacks, infiltrations, and when attacking through smoke. The commander establishes a direction of attack through a variety of means, such as target reference points, checkpoints, global positioning system (GPS) way points, using ground surveillance radar to track the attack force, and the impact of artillery shells. Target reference points placed on recognizable terrain provide the commander with the capability to rapidly shift fires and reorient his maneuver forces. When using a direction of attack, the commander designates a point of departure (PD). (Figure 3-5 depicts direction of attack JOAN and PD 6.)
3-18. The final coordination line (FCL) is a phase line (PL) close to the enemy position used to coordinate the lifting or shifting of supporting fires with the final deployment of maneuver elements. Final adjustments to supporting fires necessary to reflect the actual versus the planned tactical situation take place prior to crossing this line. It should be easily recognizable on the ground. The FCL is not a fire support coordinating measure. (Figure 3-6 shows PL ROBERT as the FCL for the 4th Brigade.)
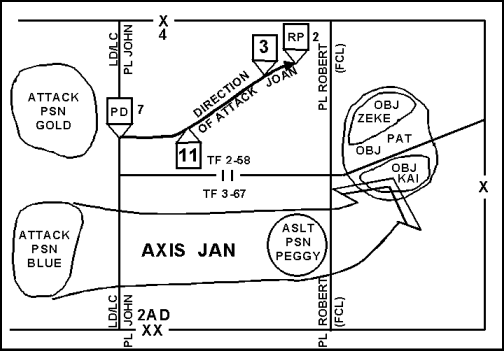
Figure 3-6. Final Coordination Line (FCL) ROBERT Used in Conjunction with Other Offensive Control Measures
3-19. The limit of advance (LOA) is a phase line used to control forward progress of the attack. The attacking unit does not advance any of its elements or assets beyond the LOA, but the attacking unit can push its security forces to that limit. A commander usually selects a linear terrain feature, perpendicular to the direction of attack, on the far side of the objective as the LOA because such a terrain feature is easily identifiable. The commander employs a LOA to prevent overextending the attacking force and reduce the possibility of fratricide by fires supporting the attack. The commander positions a LOA far enough beyond the objective to allow the unit to defend the objective. An LOA prevents units from exploiting success and launching a pursuit; therefore, a commander should only use it if he does not want the unit to conduct an exploitation or pursuit. A forward boundary is always a LOA, but a LOA is not necessarily a forward boundary. In fact, a LOA and the unit's forward boundary should rarely coincide because of the resulting limitations that a forward boundary places on supporting fires beyond the forward boundary. Figure 3-7 shows PL BASIL used as 4th Brigade's LOA.
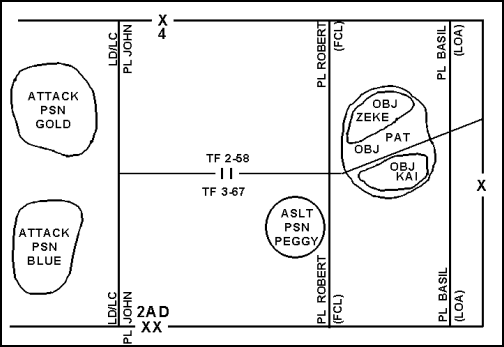
Figure 3-7. Limit of Advance Used with Other Common Control
|
3-20. The line of departure is a phase line crossed at a prescribed time by troops initiating an offensive operation. The purpose of the LD is to coordinate the advance of the attacking force so that its elements strike the enemy in the order and at the time desired. The LD also marks where the unit transitions from movement to maneuver. The commander can also use it to facilitate the coordination of fires. Generally, it should be perpendicular to the direction the attacking force will take on its way to the objective. Friendly forces should control the LD. The commander analyzes the terrain before designating his LD. Different units have different movement rates on leaving their assembly areas (AAs) based on their inherent mobility characteristics and the terrain being crossed. The commander considers these different characteristics when establishing the LD to prevent these differences from affecting the synchronization of the operation. When possible, the commander selects the LD so that the terrain the attack unit traverses before crossing the LD provides sufficient cover for the attacking unit's final deployment into a combat formation before crossing the LD. In many cases the LD is also the line of contact because the unit in contact is conducting the attack from its current positions. Figure 3-8 depicts PL DON as the LD. (Chapter 2 contains a definition for a line of contact.)
3-21. An objective is a location on the ground used to orient operations, phase operations, facilitate changes of direction, and provide for unity of effort. An objective can be either terrain- or force-oriented. Terrain objectives should be easily identifiable on the ground to facilitate their recognition. The commander determines his force-oriented objectives based on known enemy positions. The commander normally assigns his subordinate commanders only their final objectives, but can assign intermediate objectives as necessary. Figure 3-9 depicts objective STEVE. Objective STEVE is further broken down into two subordinate objectives, objective JOHN and objective HARRY.
3-22. The point of departure is the point where the unit crosses the LD and begins moving along a direction of attack. Units conducting reconnaissance and security patrols and other operations in a low-visibility environment commonly use a PD as a control measure. Like a LD, it marks the point where the unit transitions from movement to maneuver under conditions of limited visibility. Figure 3-10 depicts PD 7.
3-23. A probable line of deployment is a phase line that a commander designates as the location where he intends to completely deploy his unit into assault formation before beginning the assault. The PLD is used primarily at battalion level and below when the unit does not cross the LD in its assault formation. It is usually a linear terrain feature perpendicular to the direction of attack and recognizable under conditions of limited visibility. The PLD should be located outside the range where the enemy can place the attacking force under effective direct fire. It has no use except as it relates to the enemy. In Figure 3-11, PL ROBERT is also the PLD.
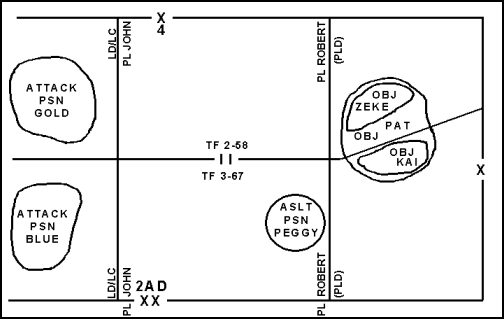
Figure 3-11. Probable Line of Deployment ROBERT Used with Other Control Measures
|
3-24. A rally point is an easily identifiable point on the ground at which units can reassemble and reorganize if they become dispersed. Alternatively it is an easily identifiable point on the ground at which aircrews and passengers can assemble and reorganize following an incident requiring a forced landing. Forces conducting a patrol or an infiltration commonly use this control measure. The objective rally point (ORP) is a rally point established on an easily identifiable point on the ground where all elements of the infiltrating unit assemble and prepare to attack the objective. It is typically near the infiltrating unit's objective; however, there is no standard distance from the objective to the ORP. It should be far enough away from the objective so that the enemy will not detect the infiltrating unit's attack preparations. Figure 3-12 depicts Rally Point 14.
3-25. A support-by-fire position designates the general position from which a unit conducts the tactical mission task of support by fire. (Appendix B defines the tactical mission task of support by fire.) The purpose of these positions is to increase the supported force's freedom of maneuver by placing direct fires on an objective that is going to be assaulted by a friendly force. Support-by-fire positions are located within the maximum friendly direct-fire range of the enemy positions. The commander selects them so that the moving assault force does not mask its supporting fires. For this reason, support-by-fire positions are normally located on the flank of the assault force, elevated above the objective if possible. Support-by-fire positions are rarely applicable to units larger than company size. The support-by-fire position graphic depicted in Figure 3-13 indicates the general location and direction from which the unit provides fires; it does not indicate a specific site.
3-26. The time of attack is the moment the leading elements of the main body cross the LD, or in a night attack, the PD. A commander uses it when conducting simultaneous operation where a shaping operation must accomplish its mission to set the conditions for the success of the decisive operation. When determining the time of attack, the commander considers the time required for his subordinate to—
Conduct necessary reconnaissance, prepare plans, and issue orders.
Synchronize plans between all subordinate units.
Complete attack preparations, such as precombat inspections.
Move to the LD or PD.
3-27. Orders normally designate the time of attack as H-hour. This is normally when the main body crosses the LD. However, H-hour can also designate the time to implement a phase of an operation, such as an airborne or air assault. The headquarters planning the offensive operation specifies the term's exact meaning. This is usually a part of the unit's standing operating procedures (SOP).
|
Forms of Maneuver
|
3-28. The forms of maneuver are envelopment, turning movement, frontal attack, penetration, and infiltration. Combined arms organizations seeking to accomplish their assigned mission synchronize the contributions of all battlefield operating systems (BOS) to execute these forms of maneuver. The commander generally chooses one form on which he builds a course of action (COA). The higher commander rarely specifies the specific form of offensive maneuver. However, his guidance and intent, along with the mission that includes implied tasks, may impose constraints such as time, security, and direction of attack that narrow the forms of offensive maneuver to one alternative. Additionally, the AO's characteristics and the enemy's dispositions also help determine the form of offensive maneuver selected. A single operation may contain several forms of offensive maneuver, such as a frontal attack to clear a security area followed by a penetration to create a gap in enemy defenses. An envelopment would follow to destroy the enemy's first line of defense.
3-29. An envelopment is a form of maneuver in which an attacking force seeks to avoid the principal enemy defenses by seizing objectives to the enemy rear to destroy the enemy in his current positions. At the tactical level, envelopments focus on seizing terrain, destroying specific enemy forces, and interdicting enemy withdrawal routes (FM 3-0). Also, at the tactical level, airborne and air assault operations are vertical envelopments. (See Appendix C.) The commander's decisive operation focuses on attacking an assailable flank. It avoids the enemy's strength—his front—where the effects of his fires and obstacles are the greatest. Generally, a commander prefers to conduct an envelopment instead of a penetration or a frontal attack because the attacking force tends to suffer fewer casualties while having the most opportunities to destroy the enemy. An envelopment also produces great psychological shock on the enemy. If no assailable flank is available, the attacking force creates one. The four varieties of envelopment are single envelopment, double envelopment, encirclement, and vertical envelopment. (See Figures 3-14 and 3-15.) For a discussion of the use of vertical envelopments, see Appendix C. For a discussion of encirclement operations, see Appendix D.
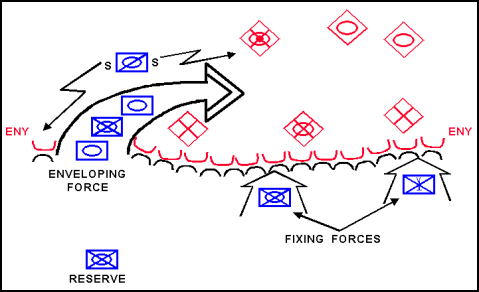
Figure 3-14. Single Envelopment
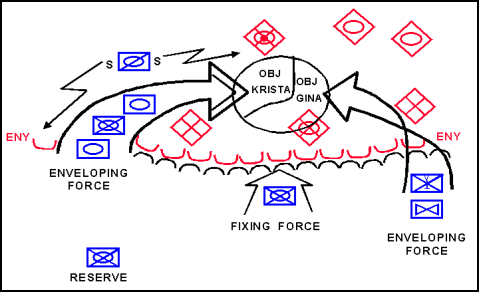
Figure 3-15. Double Envelopment
3-30. Single and double envelopments force the enemy to fight in two or more directions simultaneously to meet the converging efforts of the attack. A double envelopment generally requires a preponderance of force and can be difficult to control. A force seeking to execute a double envelopment must also have a substantial mobility advantage over the defender. A unit performs a double envelopment by conducting a frontal attack as a shaping operation in the center to fix the enemy in place while enveloping both hostile flanks. Because of the forces required, normally only divisions and larger organizations have the resources to execute a double envelopment.
3-31. The commander envisioning a single envelopment organizes his forces into the enveloping force and the fixing force. He also allocates forces to conduct reconnaissance, security, reserve, and sustaining operations. The enveloping force, conducting the decisive operation, attacks an assailable enemy flank and avoids his main strength en route to the objective. The fixing force conducts a frontal attack as a shaping operation to fix the enemy in his current positions to prevent his escape and reduce his capability to react against the enveloping force. A commander executing a double envelopment organizes his forces into two enveloping forces and a fixing force in addition to reconnaissance, security, reserve, and sustaining forces. The commander typically designates the more important of the two enveloping forces as the main effort for resources. That enveloping force will also be the commander's decisive operation if its action accomplishes the mission.
3-32. The commander, at a minimum, designates AOs for each unit participating in the envelopment by using boundaries. He also designates PLs, support-by-fire and attack-by-fire positions, contact points, and appropriate fire coordination measures, such as a restricted fire line or boundary between converging forces, and any other control measures he feels are necessary to control the envelopment. Figure 3-16 is an example of control measures used when conducting a single envelopment.
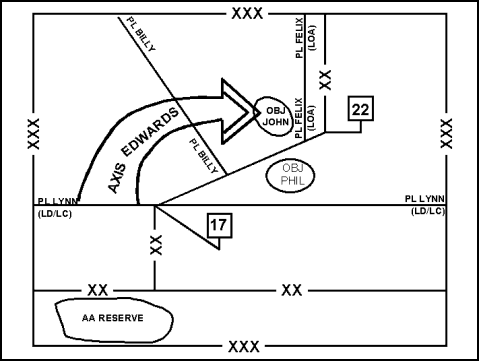
Figure 3-16. Control Measures for Conducting an Envelopment
3-33. Successful planning for an envelopment depends on knowing and understanding the enemy and his capabilities. The commander wants to maneuver his enveloping force around or over the enemy's main defenses to secure objectives on the enemy's flank or rear. From those objectives the enveloping force can use its positional advantage to employ superior combat power against a defending enemy oriented in the wrong direction. The commander uses his intelligence assets and personnel to determine the disposition and capabilities of enemy forces to detect and react to their operations.
3-34. The commander plans for the force conducting the envelopment to remain within supporting distance of the fixing force. (If the enveloping force is going outside of supporting distance, it is probably conducting a turning movement, not an envelopment.)
3-35. Sustaining the enveloping force requires deliberate planning because only intermittent ground lines of communication (LOCs) between the rear area and the enveloping force may exist. A line of communication is a route, either land, water, and/or air that connects an operating military force with a base of operations and along which supplies and military forces move (JP 1-02).
3-36. The commander plans how he will exploit the success of his envelopment as he encircles the enemy or transitions to a pursuit to complete the destruction of the enemy force. These plans are developed as branches and sequels to the envelopment operation.
3-37. A successful envelopment depends largely on the degree of surprise the commander achieves against his opponent or the presence of overwhelming combat power. The envelopment's probability of success also increases when the commander's forces have superior tactical mobility, possess air and information superiority, and his shaping operations fix the bulk of the enemy's forces in their current positions. The commander uses his intelligence, surveillance, and reconnaissance (ISR) systems to provide continuous intelligence and combat information to identify changes in enemy COAs throughout the execution of the envelopment.
3-38. Normally, a unit orients the majority of its combat power toward where it expects to engage enemy forces, while placing less combat power on its own flanks. Thus the flanks of most units are more vulnerable to attack. The commander creates an assailable flank using whatever means necessary. The enveloping force then moves rapidly to exploit the situation before the enemy strengthens an assailable flank by preparing positions in depth and by holding mobile forces in reserve. When faced with the threat of envelopment, the enemy commander might move his reserves to meet the enveloping force. Thus, rapid movement around the enemy's flank is essential to prevent him from occupying previously prepared positions. Vigorous shaping operations conducted by ground and air assets aim to prevent him from reconstituting reserves from other portions of his front.
3-39. The enemy may attempt to cut off the enveloping force and extend his flank beyond the area that the enveloping force is attempting to attack through. If the encircling force attempts to outflank such hostile extension, it may become overextended by moving outside of supporting distance from the fixing force. Therefore, it is usually better for the encircling force to take advantage of the enemy's extension and subsequent weakness by penetrating a thinly held area of the enemy's front rather than overextending itself in an attempt to completely outflank the enemy's position.
3-40. The enemy may attempt a frontal counterattack in response to an attempted envelopment. In this case, the fixing force defends itself or conducts a delay while the enveloping force continues the envelopment.
3-41. After the initial envelopment of one flank—which places the enemy at a disadvantage—the commander has many options. He may choose to establish favorable conditions for passing to a double envelopment by using reserves or exploit success by generating additional combat power along the same axis. Alternatively, he can destroy or defeat the enveloped enemy force in place, or transition to another type of operation, such as exploitation or pursuit.
3-42. A turning movement is a form of maneuver in which the attacking force seeks to avoid the enemy's principle defensive positions by seizing objectives to the enemy rear and causing the enemy to move out of his current positions or divert major forces to meet the threat (FM 3-0). However, a commander can employ a vertical envelopment using airborne or air assault forces to effect a turning movement. (Appendix C discusses airborne and air assault operations.) A commander uses this form of offensive maneuver to seize vital areas in the enemy's rear before the main enemy force can withdraw or receive support or reinforcements. See Figure 3-17 for a graphic depiction of a turning movement. This form of offensive maneuver frequently transitions from the attack into an exploitation or pursuit. A turning movement differs from an envelopment because the force conducting a turning movement seeks to make the enemy displace from his current locations, whereas an enveloping force seeks to engage the enemy in his current location from an unexpected direction.
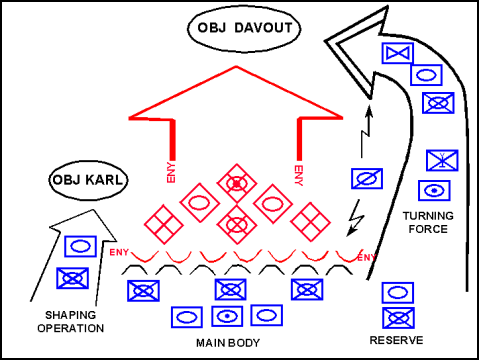
Figure 3-17. Turning Movement—Turning Force Conducting the Decisive Operation
3-43. The commander directing a turning movement task organizes his resources into a turning force, a main body, and a reserve. Each of these forces conducts security and reconnaissance operations. Either the turning force or the main body can conduct the echelon's decisive operation given the appropriate factors of METT-TC. A turning movement is particularly suited for division-size or larger forces possessing a high degree of tactical mobility. It is not until a commander has access to the resources of these echelons that he has the combat power to resource a turning force that can operate outside supporting range of his main body to allow the turning force to force enemy units out of their current positions. He bases the exact task organization of these forces on the factors of METT-TC and his concept of operations for the turning movement.
3-44. The maneuver of the turning force is what causes the enemy to leave his position. A turning force normally conducts the majority of its operations outside of the supporting range of the main body and possibly outside its supporting distance. Thus, the turning force must contain sufficient combat, combat support (CS), and combat service support (CSS) capabilities to operate independently of the main body for a specific period of time. This normally requires at least a division-size element.
3-45. The commander task organizes his main body to ensure the success of the turning force. The main body conducts operations, such as attacks designed to divert the enemy's attention away from the area where the turning force conducts its operations. The operations of the main body can be either the echelon's decisive or shaping operations. The commander organizes his reserve to exploit success by either the turning force or the main body. The reserve also provides the commander insurance against unexpected enemy actions.
3-46. The commander designates the AOs for each unit participating in the turning movement by establishing boundaries. He also designates additional control measures as necessary to synchronize the operations of his subordinates. These additional control measures include: phase lines (PLs), contact points, objectives, LOA, and appropriate fire coordination measures. Figure 3-18 depicts these control measures used to synchronize a turning movement that employs an airborne division as the turning force. (Appendix C discusses control measures associated with airborne and air assault operations.)
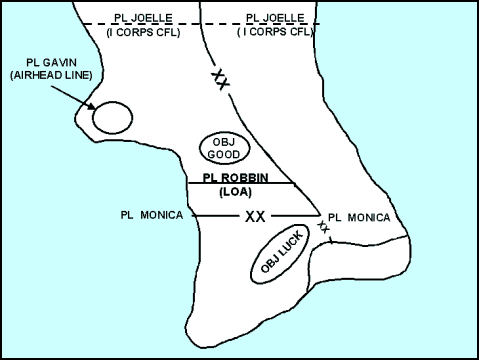
Figure 3-18. Control Measures for a Turning Movement
3-47. Selecting the geographic objective of the turning movement is of major importance to the success of the operation. The commander's scheme of maneuver in a turning movement may vary, depending on the specific situation and the factors of METT-TC. In addition to common offensive planning considerations, the commander conducting a turning movement pays special attention to planning branches and sequels to the turning movement, including—
Defensive operations by the turning force.
Link-up operations between the turning force and the main body.
Retrograde operations for the turning force.
Essential to the planning of the branches and sequels is the linkage between the branch or sequel and specific decision points supported by situation development.
3-48. After developing his tactical plan, the commander plans how the turning force maneuvers to its objective. The commander develops his movement, loading, and staging plans if outside transportation assets are required. He can plan to occupy key terrain that will threaten the enemy's survival or remain mobile and seek ways to exploit the turning force's success. Before initiating the operation, the commander plans how the turning force can exploit success.
3-49. In a turning movement that envisions an early linkup with the main body, the turning force normally plans to defend only that terrain required to protect itself. Once reinforcement or linkup with the main body occurs, the commander plans how to use the turning force to continue the attack or relieve it so it can prepare for subsequent missions.
3-50. The distances between forces and the existence of intermittent LOCs magnify the problems inherent in providing CSS to a combat force during a turning movement. Therefore, in the planning of a turning movement, the commander emphasizes resupply, equipment maintenance, casualty evacuation, graves registration, and prisoner of war handling to deal with these likely problems. Prepackaging company- and battalion-size resupply sets can ease the execution of sustaining operations during periods when CSS units must push supplies to the combat units.
3-51. Planners must consider the provision of all supplies and equipment required for mission accomplishment as an integral part of tactical planning. The commander plans and organizes his CSS operations to support a rapid tempo of highly mobile and widely dispersed operations. Traditional doctrinal supporting distances and responsibilities do not always apply to turning movements. CSS planners recognize this and adjust their plans using available resources. Only supplies required to meet the force's immediate needs are carried into the operation. Excess supplies and equipment can burden the force. Staffs establish and maintain required supply levels in the objective area by phasing supplies into the objective area on an accompanying, follow-up (automatic and on-call), and routine basis. Medical evacuation, resupply, and reinforcement airlifts may be necessary to sustain the force's combat operations. Ammunition and petroleum, oils, and lubricants (POL) normally constitute the major tonnage items. Lift restrictions affect what can be supplied using helicopters and fixed-wing aircraft.
3-52. The primary prerequisites of a successful turning movement are moving the turning force to the objective area without incurring unacceptable losses and providing the force with the required combat power and sustainment. A commander can reduce his losses by operating under conditions of friendly air and information superiority, suppressing enemy fires, and having a mobility advantage over the enemy.
3-53. Major sources of firepower to suppress enemy fires are fixed-wing aircraft, attack helicopters, jammers, and Multiple Launch Rocket Systems that cover the entire route taken by the turning force. Other sources include naval surface fire support and artillery units accompanying the turning force.
3-54. When threatened with a turning movement, the enemy commander is in a dilemma. His original defense is misplaced. He must move forces from their original position in meeting the new threat. Often he must commit his available reserves against the new threat. He exposes those forces to friendly fires as he weakens his defense and moves his forces. He must now engage friendly forces on ground he has not chosen or prepared. Whenever possible, the commander tries to reach the decisive location without encountering the enemy. Techniques to accomplish this include outflanking the enemy or using airborne, air assault, and amphibious means to avoid his prepared positions. Once friendly forces find a way deep into the enemy's rear area, the turning force moves rapidly to exploit the situation. It seeks to achieve its mission before the enemy can reposition his committed or uncommitted forces to react. Rapid movement is essential to prevent the enemy from occupying previously prepared positions in his rear. Vigorous shaping operations prevent the enemy from reconstituting reserves from other portions of the enemy front.
3-55. The enemy may counterattack in an attempt to cut off and destroy the turning force and prevent the successful completion of the turning movement. In this case, the turning force's security elements conduct an area or mobile defense or engage in delaying actions while the rest of the turning force continues its mission. Alternatively, the enemy may try to withdraw his forces to a position where his LOCs are not threatened.
3-56. An infiltration is a form of maneuver in which an attacking force conducts undetected movement through or into an area occupied by enemy forces to occupy a position of advantage in the enemy rear while exposing only small elements to enemy defensive fires (FM 3-0). Infiltration is also a march technique used within friendly territory to move forces in small groups at extended or irregular intervals. (See Chapter 14 for a discussion of infiltration as a movement technique.)
3-57. Infiltration occurs by land, water, air, or a combination of means. Moving and assembling forces covertly through enemy positions takes a considerable amount of time. To successfully infiltrate, the force must avoid detection and engagement. Since this requirement limits the size and strength of the infiltrating force—and infiltrated forces alone can rarely defeat an enemy force—infiltration is normally used in conjunction with and in support of the other forms of offensive maneuver. Historically, the scope of the mission for the infiltrating force has been limited.
3-58. The commander orders an infiltration to move all or a portion of a unit through gaps in the enemy's defenses to—
Reconnoiter known or templated enemy positions and conduct surveillance of named areas of interest and targeted areas of interest.
Attack enemy-held positions from an unexpected direction.
Occupy a support-by-fire position to support the decisive operation.
Secure key terrain.
Conduct ambushes and raids to destroy vital facilities and disrupt the enemy's defensive structure by attacking his reserves, fire support and air defense systems, communication nodes, and logistic support.
Conduct a covert breach of an obstacle or obstacle complex.
3-59. Special operations forces and light infantry units up to brigade size are best suited to conduct an infiltration. In some circumstances, heavy forces operating in small units can conduct an infiltration. However, as the proliferation of technology leads to increased situational understanding, this should increase the ability of heavy forces to avoid enemy contact and move undetected through enemy positions. In the future a commander may conduct an infiltration with heavy forces in coordination with precision fires as a prelude to an attack.
3-60. Normally, to be successful, the infiltrating force must avoid detection at least until it reaches its ORP. Thus, the infiltrating force's size, strength, and composition is usually limited. The infiltrating unit commander organizes his main body into one or more infiltrating elements. The largest size element possible, compatible with the requirement for stealth and ease of movement, conducts the infiltration. This increases the commander's control, speeds the execution of the infiltration, and provides responsive combat power. The exact size and number of infiltrating elements are situationally dependent.
3-61. The commander considers the following factors when determining how to organize his forces. Smaller infiltrating elements are not as easy to detect and can get through smaller defensive gaps. Even the detection of one or two small elements by the enemy will not prevent the unit from accomplishing its mission in most cases. Larger infiltrating elements are easier to detect and their discovery is more apt to endanger the success of the mission. Also, they require larger gaps to move through. A unit with many smaller infiltrating elements requires more time to complete the infiltration and needs more linkup points than a similar size unit with only a few infiltrating elements. Many infiltrating elements are also harder to control than fewer, larger elements.
3-62. The commander resources a security force that moves ahead of, to the flanks of, and to the rear of each infiltrating element's main body. These security forces can be given either a screen or a guard mission. (Chapter 12 discusses screen and guard missions.) The sizes and orientations of security elements are also situationally dependent. Each infiltrating element is responsible for its own reconnaissance effort.
3-63. Sustainment of an infiltrating force normally depends on the force's basic load of supplies and those medical and maintenance assets accompanying the infiltrating force. After completing the mission, the commander reopens LOCs to conduct normal sustaining operations.
3-64. Control measures for an infiltration include, as a minimum—
An AO for the infiltrating unit.
One or more infiltration lanes.
A LD or point of departure.
Movement routes with their associated start and release points, or a direction or axis of attack.
Linkup or rally points, including ORPs.
Assault positions.
One or more objectives.
A LOA.
The commander can impose other measures to control the infiltration including checkpoints, PLs, and assault positions on the flank or rear of enemy positions. If it is not necessary for the entire infiltrating unit to reassemble to accomplish its mission, the objective may be broken into smaller objectives. Each infiltrating element would then move directly to its objective to conduct operations. (Most of these control measures have been previously described.) The following paragraphs describe using an infiltration lane and a linkup point.
|
3-65. An infiltration lane is a control measure that coordinates forward and lateral movement of infiltrating units and fixes fire planning responsibilities. The commander selects infiltration lanes that avoid the enemy, provide cover and concealment, and facilitate navigation. Figure 3-19 depicts the graphic for an infiltration lane. Each unit assigned an infiltration lane picks its own routes within the lane and switches routes as necessary. The left and right limits of the infiltration lane act as lateral boundaries for the unit conducting the infiltration. Attacks by rotary- or fixed-wing aircraft, indirect fires, or munitions effects that impact the lane must be coordinated with the infiltrating unit. Units leaving their assigned lane run the risk of being hit by friendly fires. Company-size units are normally assigned a single infiltration lane, although they can use more than one lane. Larger organizations, battalion and above, are always assigned more than one infiltration lane.
3-66. A linkup point is where two infiltrating elements in the same or different infiltration lanes are scheduled to meet to consolidate before proceeding on with their missions. Figure 3-20 depicts Linkup Point 8. A linkup point is normally positioned in the enemy's rear or along one of his flanks. It should be large enough for all infiltrating elements to assemble and should offer cover and concealment for these elements. It should be an easily identifiable point on the ground. The commander should position his linkup points on defensible terrain located away from normal enemy troop movement routes.
3-67. The activities and functions associated with the process of planning an infiltration are the same as with any other combat operation. That planning takes advantage of that unit's stealth capabilities to surprise the enemy. The planning process synchronizes the BOS that support the infiltrating unit, especially precise, high-resolution intelligence. Without precise, detailed intelligence, infiltration maneuvers become high-risk probing operations, that can be costly and time-consuming. Careful planning, full ISR integration, detailed analysis, and aggressive operations security can permit an infiltrating force to avoid an enemy force, minimize direct contact, and maximize surprise according to the commander's intent.
3-68. After identifying gaps or weaknesses in the enemy's defensive positions, the commander assigns infiltration lanes, contact points, and objectives to subordinate units. These objectives afford the infiltrating force positions of greatest advantage over the enemy and are not required to be to the geographic rear of the targeted enemy force. Each subordinate unit commander picks one or more routes within his assigned lane and establishes additional contact points, rally points, assault points, and other control measures as required. The commander wants each of the routes within an infiltration lane to be far enough apart to prevent an infiltrating element on one route from seeing other infiltrating elements, but close enough so that an infiltrating element could switch quickly to another route if required by the situation. The commander wants each route to provide his infiltrating elements cover and concealment while avoiding known enemy and civilian locations and movement routes to the maximum extent possible. If possible, the subordinate unit commander selects his exact routes during the preparation phase after reconnoitering each infiltration lane. He decides whether his unit will infiltrate as a unit, in smaller elements, or even as two-man buddy teams, depending on the density and strength of the enemy.
3-69. The commander may use single or multiple infiltration lanes depending on the infiltrating force's size, the amount of detailed information on enemy dispositions and terrain accessible, time allowed, and number of lanes available. A single infiltration lane—
Facilitates navigation, control, and reassembly.
Requires the existence or creation of only one gap in the enemy's position.
Reduces the area for which detailed intelligence is required.
3-70. Multiple infiltration lanes—
Require the existence or creation of more gaps in the enemy's security area.
Reduce the possibility of compromising the entire force.
Increase difficulty with maintaining control.
3-71. The sizes and numbers of infiltrating elements are major considerations for the commander when he is deciding whether to use a single lane or multiple infiltration lanes. If the infiltration takes place using multiple elements, contingency plans must address the following situations:
A lead element, possibly the advance guard, makes contact, but the trail elements have not started infiltrating.
A lead element infiltrates successfully, but compromises one or more trailing elements.
A compromised linkup point.
3-72. The commander uses available technology to assist in planning the infiltration and avoiding unintended enemy and civilian contact during the infiltration. This can be as simple as all units using the same infiltrating lane being on the same frequency to facilitate the avoidance of enemy contact. An accurate depiction of enemy systems and locations, tied to rapid terrain analysis, can graphically depict dead spots in the enemy's battlefield surveillance. The commander can then plan how to expand those existing dead spots into infiltration lanes through a precision attack of selected enemy elements and systems.
3-73. The plan also addresses the following considerations:
Availability of supporting fires, including rotary- and fixed-wing aircraft and offensive information operations—especially electronic attack, throughout the operation, during infiltration and the attack on the objective.
Linkup or extraction of the infiltrating unit after mission completion.
Sustainment of the infiltrating force during the operation, to include casualty evacuation.
Deception operations, such as actions by other units designed to divert enemy attention from the area selected for the infiltration.
Linkup of the various infiltrating elements.
Command and control (C2), to include recognition signals.
Positioning of combat vehicles to support the infiltrating elements.
Using limited visibility and rough terrain to mask movement and reduce the chance of detection.
Infiltration of the largest elements possible to maintain control.
Rehearsals.
Specially required preparations, such as modifying the unit's SOP regarding the soldier's combat load for the mission. When infiltrating on foot, units carry only required equipment. For example, in close terrain and in the absence of an armor threat, heavy antiarmor missile systems may be a liability.
Abort criteria.
Critical friendly zones.
3-74. Planned recognition signals and linkup procedures for the infiltration should be simple and quick. If there has not been any firing or any other noises, signals should not violate noise and light discipline. However, if there have already been assaults, artillery, and small-arms fire, signals, such as whistles and flares, can be used as linkup aids. A lack of time and the short distance involved in many infiltration operations may make conducting formal linkup procedures unnecessary.
3-75. Once the commander selects the objective, infiltration lanes, and linkup or rally points, he directs ISR operations to update and confirm the details on which he bases his plan. He identifies enemy sensors and surveillance systems. He then revises the plan to reflect current conditions within the AO.
3-76. Moving undetected during an infiltration requires a considerable amount of time. The infiltrating unit moves from its AA or current position through the start point and then continues moving along the infiltration route to a release point. If buddy teams or small elements are conducting the infiltration, the unit uses a series of linkup points to reassemble into a coherent unit. Units can use a variety of navigation aids, such as GPS, to remain within the planned infiltration lane, which minimizes their chances of detection by the enemy. At the same time, they report their progress and status using communication systems that provide this information automatically to all command nodes which require this information.
3-77. If the complete unit is conducting the infiltration, the forward security force begins its movement first, followed by the main body. The distance between the forward security force and the main body depends on the factors of METT-TC. The advance guard must be far enough ahead of the main body so that it can either deploy or move to another route if the forward security force discovers the enemy. The forward security force in an infiltration must have enough time to move in a stealthy and secure manner. Enemy units should not be able to move undetected in the gap between the forward security force and the main body.
3-78. As the infiltrating unit moves, the advance guard reports to the commander regarding the cover and concealment of each route, enemy activity, location of danger areas and linkup points, enemy activity on the objective, and other combat information. The unit attempts to avoid enemy and civilian contact; however, contact does not always mean the mission is compromised. The infiltrating unit engages targets first with indirect fires to avoid revealing its presence and exact location. These fires include the conduct of offensive information operations designed to blind enemy ISR assets and prevent the enemy from coordinating an effective response to the infiltration.
3-79. If necessary, the forward security force conducts actions on contact while the main body moves to another route, reconstitutes a forward security force, and continues the mission. If the main body makes contact unexpectedly, it either overruns the enemy force, if the enemy has little combat power, or bypasses him and continues the mission. During the infiltration, the unit ignores ineffective enemy fire and continues to move. The commander may use suppressive fires against the enemy to cover the sounds of the infiltration or to divert the enemy's attention to areas other than where the infiltration lanes are located.
3-80. The infiltrating unit's elements move to an AA or an ORP to consolidate its combat power, refine the plan, and conduct any last-minute coordination prior to continuing the mission. The unit then conducts those tasks needed to accomplish its assigned mission, which could be an attack, raid, ambush, seizing key terrain, capturing prisoners, or collecting specific combat information.
3-81. A commander may need to abort an infiltration operation if the factors of METT-TC change so drastically during the infiltration that the infiltrating force is no longer capable of accomplishing its mission. Examples of changes that might trigger such an action include—
Significant portions of the infiltrating force's combat power are lost through navigation errors, enemy action, accidents, or maintenance failures.
Movement or significant reinforcement of a force-oriented objective.
Detection of the infiltration by the enemy.
Changes in the tactical situation that make the mission no longer appropriate, such as the initiation of an enemy attack.
The criteria for aborting the operation are developed in the planning process. The decision to abort the infiltration is transmitted to all appropriate headquarters for their action and information.
3-82. A penetration a form of maneuver in which an attacking force seeks to rupture enemy defenses on a narrow front to disrupt the defensive system (FM 3-0). Destroying the continuity of that defense allows the enemy's subsequent isolation and defeat in detail by exploiting friendly forces. The penetration extends from the enemy's security area through his main defensive positions into his rear area. A commander employs a penetration when there is no assailable flank, enemy defenses are overextended and weak spots are detected in the enemy's positions, or time pressures do not permit an envelopment.
3-83. Penetrating a well-organized position requires overwhelming combat power in the area of penetration and combat superiority to continue the momentum of the attack. (See Figure 3-21.) The commander designates a breach, support, and assault force. He can designate these elements for each defensive position that he is required to penetrate. He should not withhold combat power from the initial penetration to conduct additional penetration unless he has so much combat power that the success of the initial penetration is assured.
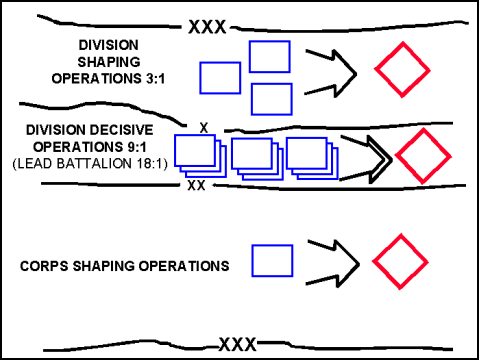
Figure 3-21. Penetration: Relative Combat Power
3-84. The commander resources a reserve to deal with expected or unexpected contingencies, such as an enemy counterattack, to avoid diverting the assault element from attacking the final objective of the penetration. He designates additional units follow-and-support or follow-and-assume missions to ensure rapid exploitation of initial success. He designates forces to fix enemy reserves in their current locations and isolate enemy forces within the area selected for penetration.
3-85. A commander assigns, as a minimum, an AO to every maneuver unit, a LD or LC; time of the attack or time of assault; phase lines; objective; and a LOA to control and synchronize the attack. (A commander can use a battle handover line instead of a LOA if he knows where he would like to commit a follow-and-assume force.) The lateral boundaries of the unit making the decisive operation are narrowly drawn to help establish the overwhelming combat power necessary at the area of penetration. The commander locates the LOA beyond the enemy's main defensive position to ensure completing the breach. If the operation results in opportunities to exploit success and pursue a beaten enemy, the commander adjusts existing boundaries to accommodate the new situation. (See Figure 3-22.)
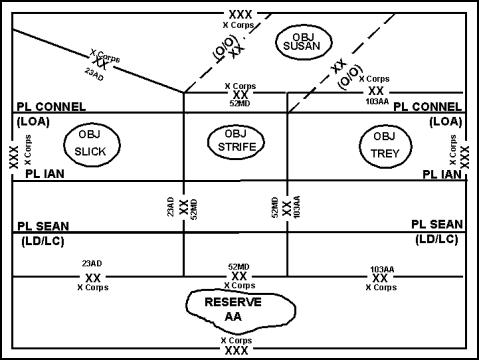
Figure 3-22. Penetration Graphic Control Measures
3-86. A commander uses the graphics associated with a breach site, such as gaps and lanes, on the small-scale maps used to control the maneuver of his forces at each point where he penetrates the enemy's defenses. FM 3-34.2 defines the graphics.
3-87. Other control measures available to the commander include checkpoints, support-by-fire and attack-by-fire positions, probable line of deployment, fire support coordinating measures, attack position, assault position, and time of assault. Within the unit's AO, a commander can use either an axis of advance or a direction of attack to further control maneuver.
3-88. The success of the penetration depends primarily on a coordinated and synchronized plan—violently executed at a high tempo to achieve surprise—against comparatively weak enemy defenses. However, the terrain behind the area selected to penetrate must allow the penetration to proceed from the breach to a decisive objective.
3-89. The depth of the enemy position and the relative strength of attacking echelons determine the width of the penetration. The availability of artillery, air support, and other combat multipliers for the attacking force helps the commander determine relative combat power. A wider gap allows friendly forces to drive deeper, making it more difficult for the enemy to close the gap. The deeper the penetration, the easier it is for a unit to seize its objective and roll up the enemy's flanks exposed by the breach and the less likely it is that the enemy will be in a position to restore his front by falling back.
3-90. Plans for penetrating a defensive position include isolating, suppressing, and destroying by fire—to include offensive information operations—enemy forces in the area selected for the penetration. These plans should also address how to isolate the area of penetration from support or reinforcement by enemy forces located outside the area. This consideration includes how to fix enemy reserves and long-range weapons in their current locations. Positioning friendly assets so that the commander can mass the effects of their combat power to accomplish these results without giving away the location of the penetration is also a critical part of the plan.
3-91. The commander plans to place the majority of his forces and assets in positions where the effects of their combat power can be felt in the area selected for penetration. The commander's plan for the penetration normally has three phases:
Breaching the enemy's main defensive positions.
Widening the gap created to secure the flanks by enveloping one or both of the newly exposed flanks.
Seizing the objective with its associated subsequent exploitation.
3-92. Planning the sequence of these phases depends on the specific situation. In some situations, if there are weaknesses or gaps in the enemy's front, it is possible for heavy forces to breach the enemy's defenses and proceed straight to the objective. Simultaneously, light units could conduct local envelopment and exploitation operations. In other situations, the commander uses his light forces to create the breach, holding his heavy forces initially in reserve to exploit gaps in the enemy's defenses created by light forces.
3-93. The commander plans shaping operations outside the area of penetration to contain the enemy on the flanks of the penetration and fix his reserves in their current locations. Synchronizing the effects of rotary- and fixed-wing aircraft, artillery fires, and obscuration smoke to delay or disrupt repositioning forces is an example of such shaping operations. These shaping operations will involve the maintenance of operations security and the conduct of deception operations. The commander usually attempts to penetrate the enemy's defensive positions along unit boundaries because defenses tend to be less effective along a boundary.
3-94. The commander plans for the penetration to break through the enemy's defenses so he is unable to reestablish his defense on more rearward positions. Until this event takes place, the commander does not want to divert the strength of his attacking units to widening the gap to secure the flanks of the penetration. However, he must develop plans that address contingencies, such as hostile counterattacks against the flanks of the penetration. The plan should provide assistance to attacking elements as they close with the enemy and support the attack until the enemy's power of resistance is broken.
3-95. After the initial breach of the enemy's main line of resistance, the sequence of the remaining two phases is determined by the factors of METT-TC. If the enemy is in a weak defensive position, it may be possible for the lead attacking force to seize the penetration's final objective while simultaneously widening the initial breach. In other situations, the commander must wait to seize the final objective until the breach is wide enough for other forces, such as reserves and follow-and-assume forces, to be committed. Commanders at all levels must take advantage of success within the commander's intent throughout the penetration.
3-96. Breaching the Enemy's Main Defensive Positions. The commander launches the actual penetration on a relatively narrow front. (See Figure 3-23.) He narrows the AO of the unit or units conducting his decisive operation—the penetration—by adjusting unit lateral boundaries to the exact point or points where he wants to penetrate the enemy's defenses. This allows the force conducting the penetration to focus overwhelming combat power. The commander assigns his assault force a close-in objective. His support force locates where it can support by fire both the breach and the assault forces. Local reserves are held in readiness to conduct a forward passage through or around units whose attacks have slowed or stopped.
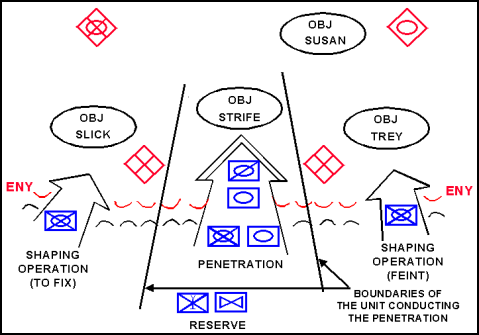
Figure 3-23. Penetration: The Breach
3-97. Shaping operations on the remainder of the hostile front fix the enemy in his current positions and prevent him from disengaging to reinforce enemy units opposing the decisive operation. The commander tracks the battle's progress to ensure that his forces penetrate entirely through the enemy's main defensive positions and not just the enemy's security area.
3-98. The enemy normally tries to slow down or stop the breach to gain time to react to the changing situation. Therefore, the attacking commander rapidly exploits and reinforces success. He piles on resources and additional units as necessary to ensure completing the penetration through the enemy's defensive positions. He also conducts offensive information operations to desynchronize the enemy's reaction.
3-99. Widening the Breach to Secure the Flanks. Once the attacking force penetrates the main defenses, it begins to widen the penetration of the enemy's defensive positions by conducting a series of shallow envelopments to roll back its shoulders. (See Figure 3-24.) The task of widening the initial gap of the penetration is normally assigned to a follow-and-support force. That task can also be assigned to the reserve as a contingency mission. If the commander commits his reserve to accomplish that task, he must reconstitute his reserve from another part of his force. Alternatively, he may assume the risk of not having a reserve for the time necessary to accomplish this task. The commander makes plans to meet enemy counterattacks by shifting fires or committing his reserves or follow-and-assume forces. Units can use obstacles on the flanks of the penetration as a combat multiplier to assist in defeating any local enemy counterattack and to provide additional security for the force.
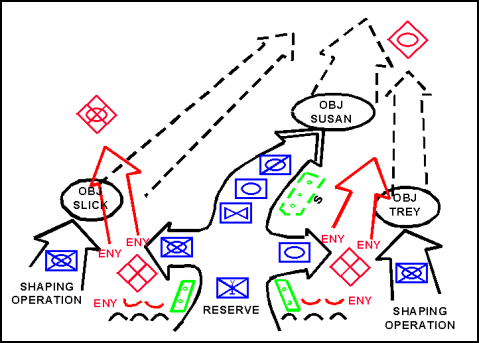
Figure 3-24. Expanding the Penetration
3-100. Seizing the Objective and Subsequent Exploitation. The mission of seizing the objective—which may be a specific enemy force—to destroy the continuity of the enemy's defensive position is normally the decisive operation after completing the penetration. Frequently that objective is so far from the area of penetration that the unit or units initially conducting the penetration cannot seize it without a pause. In that case, the commander plans to pass his reserve or follow and assume forces through the initial attacking force early, leaving exploitation beyond the objective to higher echelons. While the exact force mix is METT-TC-dependent, armored, mechanized, and aviation forces are generally suited for subsequent exploitation.
3-101. In large commands, forces may initiate an attack by simultaneously launching two or more convergent penetrations against weak localities on the hostile front. Often this method of attack helps isolate an extremely strong, hostile defense. The commander assigns shaping operations to initially contain any strong localities. When the multiple attacks have advanced sufficiently, the force reduces bypassed enemy forces and unites the penetrating attacks into a single decisive operation.
3-102. A frontal attack is a form of maneuver in which an attacking force seeks to destroy a weaker enemy force or fix a larger enemy force in place over a broad front (FM 3-0). At the tactical level, an attacking force can use a frontal attack to rapidly overrun a weak enemy force. A commander commonly uses a frontal attack as a shaping operation in conjunction with other forms of maneuver. He normally employs a frontal attack to—
Clear enemy security forces.
Overwhelm a shattered enemy during an exploitation or pursuit.
Fix enemy forces in place as part of a shaping operation.
Conduct a reconnaissance in force.
Figure 3-25 depicts a frontal attack.
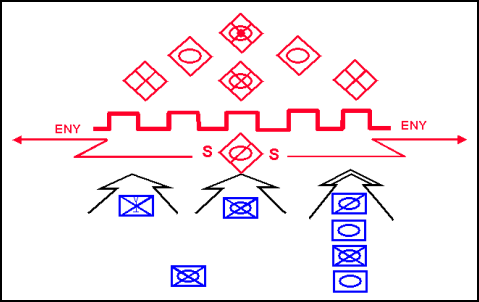
Figure 3-25. Frontal Attack
3-103. It is also necessary to conduct a frontal attack when assailable flanks do not exist. Where a penetration is a sharp attack designed to rupture the enemy position, the commander designs a frontal attack to maintain continuous pressure along the entire front until either a breach occurs or the attacking forces succeed in pushing the enemy back. Frontal attacks conducted without overwhelming combat power are seldom decisive. Consequently, the commander's choice to conduct a frontal attack in situations where he does not have overwhelming combat power is rarely justified unless the time gained is vital to the operation's success.
3-104. There is no unique organization of forces associated with this form of maneuver. A commander conducting a frontal attack organizes his unit into an element to conduct reconnaissance and security operations, a main body, and a reserve. The factors of METT-TC dictate the specific task organization of the unit.
3-105. A commander conducting a frontal attack may not require any additional control measures beyond those established to control the overall mission. This includes an AO, defined by unit boundaries, and an objective at a minimum. The commander can also use any other control measure he feels is necessary to control the attack, including—
Attack positions.
Line of departure.
Phase lines.
Assault positions.
Limit of advance.
Direction of attack or axis of advance for every maneuver unit.
A unit conducting a frontal attack normally has a wider AO than a unit conducting a penetration.
3-106. It is seldom possible for a commander to exert sufficient pressure to overwhelm an enemy using a frontal attack, since it strikes the enemy along a significant portion of his front. The force's primary objective is to maintain pressure and help fix the enemy force. The commander's planning effort should reflect these two considerations. When considering employing a frontal attack in a shaping operation, the commander should also consider other means for holding the enemy in position, such as feints and demonstrations employing indirect fires to preclude excessive losses.
3-107. The unit conducting a frontal attack advances on a broad front, normally with its subordinate ground maneuver elements abreast (except for the reserve). This clears the enemy's security area of his security forces and reconnaissance, intelligence, surveillance, and target acquisition assets while advancing the friendly force into the enemy's main defenses. Once the unit makes contact with the enemy, the attacking force's subordinate elements rapidly develop the situation and report enemy dispositions immediately to the commander so he can exploit enemy weaknesses. The attacking force fixes enemy forces in their current locations and seeks to gain a position of advantage to destroy them using fire and movement.
3-108. If the attacking unit discovers a gap in the enemy's defenses, the commander seeks to exploit that weakness and disrupt the integrity of the enemy's defense. After assessing the situation to make sure that it is not a trap, the commander can employ his reserve to exploit the opportunity. He synchronizes the exploitation with the actions of his other combat, CS, and CSS units to prevent counterattacking enemy forces from isolating and destroying successful subordinate elements of his force.
3-109. When the unit conducting the frontal attack can no longer advance, it adopts a defensive posture. The commander may require it to assist the forward passage of lines of other units. It continues to perform reconnaissance of enemy positions to locate gaps or assailable flanks.
3-110. Visualizing, describing, and directing are aspects of leadership common to all commanders. The tactical commander begins with a designated AO, identified mission, and assigned forces. The commander develops and issues planning guidance based on his visualization in terms of the physical means to accomplish the mission.
3-111. The offense is basic to combat operations. Only by a resolute offense, conducted at a high tempo and to great depth, is total destruction of the enemy attained. The offense has a number of indisputable advantages. The principal advantage enjoyed is its possession of the initiative. Having the initiative allows a commander to select the time, place, and specific tactics, techniques, and procedures used by the attacking force. The attacker has the time and opportunity to develop a plan and to concentrate the effects of his forces and thoroughly prepare conditions for success when he has the initiative. The commander strikes the enemy in unexpected ways at unexpected times and places. He focuses on attacking the right combination of targets, not necessarily the biggest or the closest. These attacks are rapidly executed, violently executed, unpredictable in nature, and disorient the enemy. They enhance the commander's capability to impose his will on his enemy and thus to achieve decisive victory.
3-112. The commander maintains momentum by rapidly following up his attacks to prevent enemy recovery. He denies his enemy any opportunity to adjust to his action in spite of the enemy's desperate attempts to do so. He changes his means and methods before the enemy can adapt to those in current use. The tempo of his operations must be fast enough to prevent effective counteraction. He orchestrates unrelenting pressure by adjusting combinations to meet the offensive's ever-changing demands. He maintains relentless pressure and exploits his gains to make permanent any temporary battlefield success.
3-113. Each battle or engagement, even those occurring simultaneously as a part of the same campaign, has its own unique peculiarities, determined by the actual conditions of the situation. The widespread application of highly accurate and lethal weapons, high degree of tactical mobility, dynamic nature, rapid situational changes, and the noncontiguous and large spatial scope of unit AOs all characterize contemporary combined arms warfare. The commander first able to see the battlefield, understand the implications of existing friendly and enemy operational picture, and take effective action to impose his will on the situation will enjoy tactical success.
3-114. The following discussion uses those physical means—soldiers, organizations, and equipment—that constitute the seven BOS defined in FM 7-15 as the framework for discussing planning considerations that apply to all types and forms of tactical offensive operations. The commander synchronizes the effects of all BOS as part of the visualize, describe, direct, and assess process.
3-115. A commander uses the products of the intelligence preparation of the battlefield (IPB) process to identify any aspect within his AO or area of interest that will affect how he accomplishes his mission. An area of interest is that area of concern to the commander, including the area of influence, areas adjacent thereto, and extending into enemy territory to the objectives of current or planned operations. This area also includes areas occupied by enemy forces who could jeopardize the accomplishment of the mission (JP 2-03).
3-116. The entire staff, led by the echelon intelligence staff, uses the IPB process to identify any aspects of the area of operations or area of interest that will affect enemy, friendly, and third party operations. The IPB process is collaborative in nature and requires information from all staff elements and some subordinate units. All staff and subordinate elements use the results and products of the IPB process for planning. FM 2-01.3 describes the IPB process.
3-117. The commander uses his ISR assets to study the terrain and confirm or deny the enemy's strengths, dispositions, and likely intentions, especially where and in what strength the enemy will defend. These assets also gather information concerning the civilian population within the AO to confirm or deny their numbers, locations, and likely intentions, especially with regard to staying put in shelters or fleeing from combat operations.
3-118. By studying the terrain, the commander tries to determine the principal heavy and light avenues of approach to his objective. He also tries to determine the most advantageous area for the enemy's main defense to occupy, routes that the enemy may use to conduct counterattacks, and other factors, such as observation and fields of fire, avenues of approach, key terrain, obstacles, and cover and concealment (OAKOC). (See FM 6-0 for a discussion of the components of OAKOC.) It is unlikely that the commander has complete knowledge of the enemy's intentions; therefore, he must conduct ISR collection continuously during the battle.
3-119. The echelon intelligence and operations officers, in coordination with the rest of the staff, develop an integrated ISR plan that satisfies the commander's maneuver, targeting, and information requirements. A commander's information requirements are dictated by the factors of METT-TC, but commonly include—
Locations, composition, equipment, strengths, and weaknesses of the defending enemy force, to include high-priority targets and enemy ISR capabilities.
Locations of possible enemy assembly areas.
Location of enemy indirect-fire weapon systems and units.
Location of gaps and assailable flanks.
Location of areas for friendly and enemy air assaults.
Location of enemy air defense gun and missile units.
Location of enemy electronic warfare units.
Effects of weather and terrain on current and projected operations.
Numbers, routes, and direction of movement of dislocated civilians.
Withdrawal routes for enemy forces.
Anticipated timetable schedules for the enemy's most likely COA and other probable COAs.
Locations of enemy C2 and ISR systems and the frequencies used by the information systems linking these systems.
If friendly ISR systems cannot answer the commander's information requirements, his intelligence staff can send a request for information to higher and adjacent units, he can commit additional resources, or he can decide to execute his offensive operation with the current information.
3-120. The commander conducts maneuver to avoid enemy strengths and to create opportunities to increase the effects his fires. He secures surprise by making unexpected maneuvers, rapidly changing the tempo of ongoing operations, avoiding observation, and using deceptive techniques and procedures. He seeks to overwhelm the enemy with one or more unexpected blows before the enemy has time to react in an organized fashion. This occurs when he is able to engage the defending enemy force from positions that place the attacking force in a position of advantage with respect to the defending enemy force, such as engaging the enemy from a flanking position. His security forces prevent the enemy from discovering friendly dispositions, capabilities, and intentions, or interfering with the preparations for the attack. Finally, he maneuvers to close with and destroy the enemy by close combat and shock effect. Close combat is combat carried out with direct fire weapons, supported by indirect fire, air-delivered fires, and nonlethal engagement means. Close combat defeats or destroys enemy forces, or seizes and retains ground (FM 3-0). Close combat encompasses all actions that place friendly forces in immediate contact with the enemy where the commander uses direct fire and movement in combination to defeat or destroy enemy forces or seize and retain ground.
3-121. A commander can overwhelm an enemy by the early seizing and retaining of key and decisive terrain that provides dominating observation, cover and concealment, and better fields of fire to facilitate the maneuver of his forces. If decisive terrain is present, the commander designates it to communicate its importance in his concept of operations, first to his staff and later to subordinate commanders. The friendly force must control decisive terrain to successfully accomplish its mission.
3-122. A combat formation is an ordered arrangement of forces for a specific purpose and describes the general configuration of a unit on the ground. A commander can use seven different combat formations depending on the factors of METT-TC:
Column.
Line.
Echelon (left or right).
Box.
Diamond.
Wedge.
Vee.
Terrain characteristics and visibility determine the actual arrangement and location of the unit's personnel and vehicles within a given formation.
3-123. Combat formations allow a unit to move on the battlefield in a posture suited to the senior commander's intent and mission. A unit may employ a series of combat formations during the course of an attack; each has its advantages and disadvantages. Subordinate units within a combat formation can also employ their own combat formations, consistent with their particular situation. The commander considers the advantages and disadvantages of each formation in the areas of C2 maintenance, firepower orientation, ability to mass fires, and flexibility when determining the appropriate formation for a given situation. All combat formations use one or more of the three movement techniques: traveling, traveling overwatch, and bounding overwatch. (Chapter 13 describes these three movement techniques.)
3-124. The commander's use of standard formations allows him to rapidly shift his unit from one formation to another, giving him additional flexibility when adjusting to changes in the factors of METT-TC. (This results from a commander rehearsing his unit so that it can change formations using standard responses to changing situations, such as actions on contact.) By designating the combat formation he plans to use, the commander—
Establishes the geographic relationship between units.
Indicates how he plans to react once the enemy makes contact with the formation.
Indicates the level of security desired.
Establishes the preponderant orientation of his weapon systems.
Postures his forces for the attack.
The number of maneuver units available makes some formations, such as the box and the diamond, impractical for modernized organizations, including the initial brigade combat team and the limited conversion division, which only have three subordinate maneuver units at the brigade and battalion echelons unless task organization occurs.
|
3-125. Column Formation. The unit moves in column formation when the commander does not anticipate early contact, the objective is distant, and speed and control are critical. (See Figure 3-26.) The location of fire support units within the column reflects the column's length and the range fans of those fire support systems. Normally, the lead element uses a traveling overwatch technique while the following units are in traveling formation. Employing a column formation—
Provides the best formation to move large forces quickly, especially with limited routes and limited visibility.
Makes enemy contact with a small part of the total force while facilitating control and allowing the commander to quickly generate mass.
Provides a base for easy transition to other formations.
Works in restricted terrain.
3-126. A disadvantage of using the column formation is that the majority of the column's firepower can only be immediately applied on the column's flanks. The length of the column impacts movement and terrain management. Additionally, there are the possibilities of inadvertently bypassing enemy units or positions and exposing the unit's flanks or running head on into an enemy deployed perpendicular to the column's direction of movement.
3-127. Line Formation. In a line formation, the unit's subordinate ground maneuver elements move abreast of each other. (See Figure 3-27.) A commander employs this formation when he assaults an objective because it concentrates firepower to the front in the direction of movement. A line formation also—
Facilitates speed and shock in closing with an enemy.
Allows the coverage of wide frontages.
Facilitates the occupation of attack-by-fire or support-by-fire positions.
3-128. There are also disadvantages of a line formation:
Provides less flexibility of maneuver than other formations since it does not distribute units in depth.
Linear deployment allows a unit deployed on line to bring only limited firepower to bear on either flank.
Provides limited or no reserve.
Limits overwatch forces.
Limits control of a unit using a line formation in restricted terrain or under conditions of limited visibility.
3-129. Echelon Formation. A commander who has knowledge of potential enemy locations can use an echelon formation to deploy his subordinate ground maneuver units diagonally left or right. (See Figures 3-28 and 3-29.) Units operating on the flank of a larger formation commonly use this formation. Using an echelon formation—
Facilitates control in open terrain.
Allows the concentration of the unit's firepower forward and to the flank in the direction of echelon.
Allows forces not in contact to maneuver against a known enemy, because all elements probably will not come into contact at the same time.
3-130. The primary disadvantages of the echelon formation are that it is more difficult to maintain control over the unit in restricted terrain than a column formation and the lack of security or firepower available on the opposite side of the echelon.
3-131. Box Formation. The box formation arranges the unit with two forward and two trail maneuver elements. (See Figure 3-30.) A unit with only three maneuver elements cannot adopt the box formation. The subordinate elements of the box usually move in a column formation with flank security. It is often used when executing an approach march, an exploitation, or a pursuit when the commander has only general knowledge about the enemy. Employing a box formation—
Allows the unit to change quickly and easily to any other formation.
Facilitates rapid movement, yet still provides all-around security.
Provides firepower to the front and flanks.
Maintains control more easily when compared to a line formation.
The primary disadvantages of a box formation are that it requires sufficient maneuver space for dispersion and the availability of multiple routes.
3-132. Diamond Formation. The diamond formation arranges the unit with one forward and one trail unit and a unit on each flank. (See Figure 3-31.) The subordinate elements of the diamond usually move in a column formation with flank security. It is most effective during approach marches, exploitations, or pursuits when the commander has only general knowledge about the enemy. Employing a diamond formation—
Allows the commander to maneuver either left or right immediately, without first repositioning, regardless of which subordinate element makes contact with the enemy. (This is the chief advantage of and the difference between a diamond and a box formation.)
Facilitates making enemy contact with the smallest possible force, yet provides all-around security.
Provides firepower to the front and flanks.
Changes easily and quickly to another formation.
Facilitates speed of movement while remaining easy to control.
Provides an uncommitted force for use as a reserve.
3-133. The primary disadvantages of this formation are that it—
Requires sufficient space for dispersion laterally and in depth.
Requires four subordinate maneuver elements.
Requires the availability of multiple routes.
3-134. Wedge Formation. The wedge formation arranges forces to attack an enemy appearing to the front and flanks. (See Figure 3-32.) A unit with only three subordinate maneuver elements can adopt the wedge formation. The commander uses the wedge when contact with the enemy is possible or expected, but his location and dispositions are vague. It is the preferred formation for a movement to contact in an organization with three subordinate maneuver units because it initiates contact with one unit while retaining two other subordinate uncommitted units positioned to maneuver and further develop the situation. Within the wedge, subordinate units employ the formation best suited to the terrain, visibility, and likelihood of contact. Employing a wedge formation—
Provides maximum firepower forward and allows a large portion of the unit's firepower to be used on the flanks.
Allows rapid crossing of open terrain when enemy contact is not expected.
Facilitates control.
Allows for rapid changes in the orientation of the force.
Facilitates the rapid change to a line, vee, echelon, or column formation.
3-135. The primary disadvantages to the wedge formation are that it—
Requires sufficient space for dispersion laterally and in depth.
Requires the availability of multiple routes.
Lacks ease of control in restricted terrain or poor visibility.
3-136. Vee Formation. The vee formation disposes the unit with two maneuver elements abreast and one or more units trailing. (See Figure 3-33.) This arrangement is well suited for an advance against a known threat to the front. The commander may use this formation when he expects enemy contact and knows the location and disposition of the enemy. Employing a vee formation—
Provides maximum firepower forward and good firepower to the flanks, but the firepower on the flanks is less than that provided by the wedge.
Facilitates a continued maneuver after contact is made and a rapid transition to the assault.
Allows the unit to change quickly to a line, wedge, or column formation.
3-137. The primary disadvantages to this formation are that it—
Makes reorientation of the direction of movement, such as a 90-degree turn, more difficult than using a wedge.
Makes control in restricted terrain and under limited-visibility conditions difficult.
Requires sufficient space for dispersion laterally and in depth.
3-138. The capability to fight at night and under limited-visibility conditions is an important aspect of conducting maneuver. The commander conducts field training exercises under limited-visibility conditions to ensure that his unit has this capability as part of his standard training program. A commander conducts offensive operations at night or under limited-visibility conditions when a daylight operation continues into the night or when an operation could result in heavy losses if conducted in daylight. Offensive operations conducted in these conditions can achieve surprise, gain terrain required for further operations, and negate enemy visual target acquisition capabilities while taking advantage of the friendly force's night-fighting capabilities.
3-139. All operations conducted in limited visibility or adverse weather require more planning and preparation time than normal. They require designating reference points and establishing navigation aids, such as GPS waypoints. The commander ensures that the night-vision and navigation systems required to maneuver under these conditions are available and functional. The commander rehearses these operations before execution to ensure complete integration and synchronization of the plan. Rehearsals also ensure that his soldiers have the necessary skills to accomplish the mission. Any problem areas require resolution before beginning the operation.
3-140. Night operations degrade the capabilities of soldiers and units. Cognitive abilities degrade more rapidly than physical strength and endurance. Night-vision devices degrade the user's depth perception. This degradation in performance occurs after as little as 18 hours of sustained work. (Additional information concerning the impact of extended operations on soldiers and unit can be found in FM 6-22.5.) The plan should allow time for both soldiers and units to recuperate after conducting a night attack before being committed to other operations. The weight that soldiers must carry also directly affects their endurance. The commander carefully determines the fighting load of his soldiers, taking into account the factors of METT-TC and limits the fighting load of his soldiers conducting night operations. The equipment carried by a soldier for an extended period should never exceed one-third of his body weight.
3-141. Fire superiority must be gained and maintained throughout all offensive operations. Fire support uses a variety of methods and assets that attrit, delay, and disrupt enemy forces and enable friendly maneuver. Using preparatory, counterfire, suppression, and nonlethal fires provides the commander with numerous options for gaining and maintaining fire superiority. The commander uses his long-range artillery systems and air support to engage the enemy throughout the depth of his positions.
3-142. Along with the reserve, attacks by indirect-fire systems and close air support are some of the commander's principal means for influencing ongoing actions. Such support helps establish the conditions required for successful mission accomplishment and is key to the commander's ability to react to unexpected situations. Decentralized execution characterizes the employment of fires when conducting offensive operations. Subordinates must have direct access to sufficient firepower to adequately support their maneuvering elements. Simultaneously, the commander retains control over sufficient fire support assets to enable him to mass their effects at critical times and places to support his decisive operation or to respond to the enemy's counteraction.
3-143. Fire support planning is the continuing process of analyzing, allocating, and scheduling fires. It determines how fires are used, what types of targets to attack, what collection assets are used to acquire and track those targets, what assets are used to attack the target, and what assets verify effects on the target. This planning does not stop at the objective or LOA. The commander gives attention to flanks and potential enemy hide positions. Coordination among echelon fire support elements (FSEs) and the proper use of fire support coordinating measures are critical to prevent fratricide.
3-144. The fire support coordinator (FSCOORD) integrates fire support into the unit's maneuver scheme for the commander. The FSCOORD supports the unit's maneuver by planning preparatory fires, harassing fires, interdiction fires, suppressive fires, and deception fires. These fires can be time- or event-driven. The FSCOORD plans fires on known and likely enemy positions, which may include templated enemy positions. Successful massing of indirect fires and fixed-wing attacks requires a FSE that is proficient in the tracking of all battery positions and movements and knows the maximum ordinate requirements. It also requires a tactical air control party proficient in the timely execution of close air support. Fire planning reconciles top-down planning and bottom-up refinement.
3-145. As the attacking force moves forward, preparatory fires sequentially neutralize, suppress, or destroy enemy positions. The commander must weigh its probable effects against achieving a greater degree of surprise against the enemy, especially under conditions of limited visibility, in determining whether to fire an artillery preparation. He may decide to employ smart or brilliant munitions to destroy select high-payoff targets or use these munitions in mass against part of the enemy defense to facilitate a breach and negate the requirement for long-duration preparation fires using conventional munitions.
3-146. The commander may choose to make his initial assault without using preparatory fires to achieve tactical surprise. However, fires are always planned to support each unit's operations so that they are available if needed. Preparatory fires are normally high-volume fires delivered over a short period of time to maximize surprise and shock effect. These preparatory fires also include the conduct of offensive information operations. They can continue while ground combat elements are maneuvering. This consideration applies to all types and forms of offensive operations.
3-147. Artillery and mortars must occupy positions that are well forward and still within supporting range of the flanks or maneuver forces to provide responsive indirect fires. The commander considers the effect that movement by echelon or battery has on the amount of fire support provided. The commander should support his unit's decisive operation with priority of fires. His main effort prior to the initiation of the decisive operation will have priority of fires if the operation contains phases. He places coordinated fire lines (CFLs) as close as possible to friendly maneuver forces and plans on-order CFLs on phase lines so that they can be quickly shifted as the force moves. This allows the expeditious engagement of targets beyond the CFL by the maximum number of available systems.
3-148. The effective assignment of forward observers and target acquisition assets to quick-fire or exclusive nets also provides responsive fires. Quick-fire nets allow the lead observers to associate directly with specific field artillery or mortar fire units. These kinds of communication arrangements enhance fire support responsiveness through streamlined net structures and focused priorities. Communications planning should also include the need for communication nets for the clearing of targets for rotary- and fixed-wing attacks.
3-149. Offensive information operations perform several functions to support the offense. As the friendly force moves through the enemy's security area and closes into his main defensive positions, jamming resources concentrate on neutralizing enemy fire control, target acquisition, and intelligence-gathering systems. The commander uses deception to prevent the enemy from determining the location and objective of his decisive operation. In addition, electronic warfare resources continue to provide intelligence and guidance to both friendly jammers and lethal indirect fire weapon systems so attacking units can destroy enemy C2, ISR, fire support, and other high-value targets. The commander synchronizes the timing and conduct of his offensive operations so they achieve maximum effectiveness.
3-150. Air defense operations are performed by all members of the combined arms team; however, ground-based air defense artillery units execute the bulk of the Army's air defense tasks. Allocation of air defense artillery assets within a unit depends on the factors of METT-TC. The commander at each echelon establishes his air defense priorities based on his concept of operations, scheme of maneuver, air situation, and the air defense priorities established by higher headquarters. He generally will weight his air defense coverage toward his decisive operation and establish a protective corridor over the terrain traversed by the unit conducting that decisive operation. The commander has the option of retaining all assets under his direct control or allocating assets to subordinate units. Command and control of all air defense assets requires complete and timely communications to ensure proper weapon status for the protection of friendly air support assets.
3-151. Passive air defense measures are an essential part of air and missile defense planning at all levels. All units conduct passive actions in conjunction with their assigned missions. Passive actions reduce the effectiveness of the enemy air threat.
3-152. Targets selected to support echelon tactical air defense efforts include the following—
Unmanned aerial vehicles with their launchers and control nodes.
Rotary- and fixed-wing aircraft.
Facilities supporting enemy air operations, such as airfields, launch sites, logistics support facilities, technical support facilities, forward arming and refueling points, navigation aids, and C2 sites.
These facilities are normally engaged by maneuver and fire support elements and not air defense artillery units. (See FM 3-01 for additional information on using active and passive air defense measures in the offense.)
3-153. This BOS has three basic purposes. It preserves the freedom of maneuver of friendly forces. It obstructs the maneuver of the enemy in areas where fire and movement can destroy him. Finally, it enhances the survivability of friendly forces. Time, equipment, and materials may restrict the amount of work accomplished before, during, and after conducting an offensive operation. The commander's plan must realistically reflect these limitations. The plan must provide the desired balance among these three basic purposes and assign support priorities among subordinate units. Normally, priority of support should be concentrated on the unit or units conducting the decisive operation rather than distributed evenly throughout the force. That support will focus on maintaining the mobility of the force conducting the decisive operation while ensuring the survivability of the C2 system.
3-154. Mobility is key to successful offensive operations. Its major focus is to enable friendly forces to maneuver freely on the battlefield. The commander wants the capability to move, exploit, and pursue the enemy across a wide front. When attacking, he wants to concentrate the effects of combat power at selected locations. This may require him to improve or construct combat trails through areas where routes do not exist. The surprise achieved by attacking through an area believed to be impassable may justify the effort expended in constructing these trails. The force bypasses existing obstacles and minefields identified before starting the offensive operation instead of breaching them whenever possible. Units mark bypassed minefields whenever the factors of METT-TC allow.
3-155. Maintaining the momentum of an offensive operation requires the force to quickly pass through obstacles as it encounters them. This translates to a deliberate effort to capture bridges and other enemy reserved obstacles intact. Using air assault and airborne forces is an effective technique to accomplish this goal. The preferred method of fighting through a defended obstacle is employing an in-stride breach, because it avoids the loss of time and momentum associated with conducting a deliberate breach. The commander plans how and where his forces conduct breaching operations. He plans his breaching operations using a reverse planning sequence from the objective back to the assembly area. FM 3-34.2 addresses breaching operations in more detail.
3-156. Rivers remain major obstacles despite advances in high-mobility weapon systems and extensive aviation support. River crossings are among the most critical, complex, and vulnerable combined arms operations. Rivers are crossed in-stride as a continuation of the attack whenever possible. The size of the river, as well as the enemy and friendly situations, will dictate the specific tactics, techniques, and procedures used in conducting the crossing. Corps engineer brigades contain the majority of tactical bridging assets. (See FM 3-97.13 for additional information on conducting hasty and deliberate river crossings.)
3-157. Countermobility operations are vital to help isolate the battlefield and protect the attacking force from enemy counterattack, even though force mobility in offensive operations normally has first priority. Obstacles provide security for friendly forces as the fight progresses into the depth of the enemy's defenses. They provide flank protection and deny the enemy counterattack routes. They assist friendly forces in defeating the enemy in detail and can be vital in reducing the amount of forces required to secure a given area. Further, they can permit the concentration of forces for offensive operations in the first place by allowing a relatively small force to defend a large AO. The commander ensures the use of obstacles is fully synchronized with his concept of operations and does not hinder the mobility of the attacking force.
3-158. During visualization, the commander identifies avenues of approach that offer natural flank protection to an attacking force, such as rivers or ridgelines. Staff estimates support this process. Flanks are protected by destroying bridges, emplacing minefields, and by using scatterable mines to interdict roads and trails. Swamps, canals, lakes, forests, and escarpments are natural terrain features that can be quickly reinforced for flank security.
3-159. Offensive countermobility plans must stress rapid emplacement and flexibility. Engineer support must keep pace with advancing maneuver forces and be prepared to emplace obstacles alongside them. Time and resources will not permit developing the terrain's full defensive potential. The commander first considers likely enemy reactions, then plans how to block enemy avenues of approach or withdrawal with obstacles. He also plans the use of obstacles to contain bypassed enemy elements and prevent the enemy from withdrawing. The plan includes obstacles to use on identification of the enemy's counterattack. Speed and interdiction capabilities are vital characteristics of the obstacles employed. The commander directs the planning for aircraft- and artillery-delivered mines on enemy counterattack routes. The fire support system delivers these munitions in front of or on top of enemy lead elements once they commit to one of the routes. Rapid cratering devices and surface minefields provide other excellent capabilities.
3-160. Control of mines and obstacles, and accurate reporting to all units are vital. Obstacles will hinder both friendly and enemy maneuver. Positive C2 is necessary to prevent the premature activation of minefields and obstacles. (See FM 3-34.1 for additional information on using countermobility obstacles in the offense.)
3-161. Denying the enemy a chance to plan, prepare, and execute an effective response to friendly offensive operations through maintaining a high operational tempo is a key means a commander employs to ensure the survivability of his force. Using multiple routes, dispersion, highly mobile forces, piecemeal destruction of isolated enemy forces, scheduled rotation and relief of forces before they culminate, and wise use of terrain are techniques for maintaining a high tempo of offensive operations. The exact techniques employed in a specific situation must reflect the factors of METT-TC.
3-162. The commander protects his force to deny the enemy the capability to interfere with ongoing operations. That protection also meets his legal and moral obligations to his soldiers. To protect his force, the commander—
Maintains a high tempo of operations.
Conducts area security operations.
Employs operations security (OPSEC) procedures.
Executes deception operations.
Conducts defensive information operations.
Employs camouflage, cover, and concealment.
Constructs survivability positions for nondisplacing systems and supplies.
Conducts operations to defend against enemy use of nuclear, biological, and chemical weapons.
Although this list is not all-inclusive, it typifies the measures a commander takes to secure his force during offensive operations.
3-163. The echelon's OPSEC program and any deception or survivability efforts should conceal from the enemy or mislead him regarding the location of the friendly objective, decisive operation, the disposition of forces, and the timing of the offensive operation. This tends to prevent the enemy from launching effective spoiling attacks. (See FM 3-13 for additional information on OPSEC, deception, and defensive information operations.)
3-164. The commander normally considers the impact of directing the construction of protective emplacements for artillery, air defense units, and logistics concentrations as part of his planning process. This occurs although units do not employ protective positions in the offense as extensively as they do in the defense. The commander may require the hardening of key C2 facilities, especially those with detectable electronic signatures. Maneuver units construct as many fighting positions as possible whenever they halt or pause during offensive operations. They improve existing terrain by cutting reverse-slope firing shelves or slots when possible. (See FM 3-34.112 for more information on constructing protective positions.) Forces conducting offensive operations will continue to use camouflage, cover, and concealment. (See FM 3-24.3 for additional information on those topics.)
3-165. The IPB process contributes to survivability by developing products that help the commander protect his forces, including intervisibility overlays and situation templates. Intervisibility overlays help protect the force. If an enemy cannot observe the friendly force, he cannot engage the friendly force with direct-fire weapons. Situation templates also help protect the force. If a commander knows how fast an enemy force can respond to his offensive operations, he can sequence his operations at times and places where the enemy can respond least effectively. This occurs through determining enemy artillery range fans, movement times between enemy reserve assembly area locations and advancing friendly forces, and other related intelligence items.
3-166. The commander integrates NBC defensive considerations into his offensive plans. Implementing many NBC defensive measures slows the tempo, degrades combat power, and may also increase logistics requirements. NBC reconnaissance consumes resources, especially time. Personnel in protective gear find it more difficult to work or fight. The key fundamental of all NBC defense activities is to avoid NBC attacks and their effect whenever possible. Avoidance includes passive and active avoidance measures. The other fundamentals of NBC defense are protection and decontamination. Avoidance and protection are closely linked. (See FM 3-11 for additional information on NBC defensive considerations.)
3-167. The objective of CSS in offensive operations is to assist the tactical commander in maintaining the momentum. The commander wants to take advantage of windows of opportunity and launch offensive operations with minimum advance warning time. Therefore, logistics and personnel planners and operators must anticipate these events and maintain the flexibility to support the offensive plan accordingly. A key to successful offensive operations is the ability to anticipate the requirement to push support forward, specifically in regard to ammunition, fuel, and water. Combat service support commanders must act, rather than react, to support requirements. The existence of habitual support relationships facilitates the ability to anticipate.
3-168. Combat service support maintains momentum of the attack by delivering supplies as far forward as possible. The commander can use throughput distribution and preplanned and preconfigured packages of essential items to help maintain his momentum and tempo. The commander examines his unit's basic load to determine its adequacy to support the operation. He determines his combat load, the supplies carried by his individual soldiers and combat vehicles. His sustainment load consists of what remains of his basic load once his combat load is subtracted. His tactical vehicles carry the sustainment load. The commander also determines the supplies required for likely contingencies. He determines the amount of cross-loading of supplies required by the situation to prevent all of one type of supply from being destroyed by the loss of a single system.
3-169. CSS units and material remain close to the maneuver force to ensure short turnaround time for supplies and services. This includes uploading as much critical materiel—such as POL and ammunition—as possible and coordinating to preclude attempted occupation of a piece of terrain by more than one unit. The commander makes a decision regarding the possibility that CSS preparation for the attack will be detected by enemy forces and give away his tactical plans.
3-170. The availability of adequate supplies and transportation to sustain the operation becomes more critical as it progresses. Supply LOCs are strained, and requirements for repair and replacement of weapon systems mount. Requirements for POL increase because of the distance the combat vehicles of the maneuver force are likely to travel. CSS units in direct support of maneuver units must be as mobile as the forces they support. One way to provide continuous support is to task organize elements of CSS units or complete CSS units with their supported maneuver formations as required by the factors of METT-TC.
3-171. The variety and complexity of offensive operations requires the Army to establish a flexible and tailorable transportation system. There may be a wide dispersion of forces and lengthening of LOCs. Required capabilities include movement control, in-transit visibility of supplies being carried, terminal operations, and mode operations.
3-172. Maintenance assets move as far forward as consistent with the tactical situation to repair inoperable and damaged equipment and to return it to battle as quickly as possible. Crews continue to perform their preventive maintenance checks and services as modified for the climate and terrain in which they find themselves. Battle damage assessment and repair (BDAR) may be critical to sustaining offensive operations. Crews as well as maintenance and recovery teams conduct BDAR to rapidly return disabled equipment for battlefield service by expediently fixing, bypassing, or jury-rigging components. It restores the minimum essential combat capabilities necessary to support a specific combat mission or to enable the equipment to self-recover.
3-173. The burden on medical resources increases due to the intensity of operations and the increased distances over which support is required as the force advances. The commander reallocates medical resources as the tactical situation changes. Medical units can anticipate large numbers of casualties in a short period of time due to the capabilities of modern conventional weapons and the employment of weapons of mass destruction. These mass casualty situations will probably exceed the capabilities of local medical units and require them to alter their normal scope of operations to provide the greatest good for the greatest number. Key factors for effective mass casualty management are on-site triage, emergency resuscitative care, early surgical intervention, reliable communications, and skillful evacuation by air and ground resources.
3-174. Establishing aerial resupply and forward logistics bases may be necessary to sustain maneuver operations such as exploitation and pursuit conducted at great distance from the unit's sustaining base. The unit or support activity at the airlift's point of origin is responsible for obtaining the required packing, shipping, and sling-load equipment. It prepares the load for aerial transport, prepares the pickup zone, and conducts air-loading operations. The unit located at the airlift destination is responsible for preparing the landing zone to accommodate aerial resupply and for receiving the load.
3-175. Raids conducted by ground maneuver forces within the depths of the enemy's rear area tend to be audacious, high-speed, and of short duration. Logistics support is minimal; units carry as much POL and ammunition as possible, taking advantage of any captured enemy supplies. Once the raiding force crosses its LD, only limited, emergency aerial resupply of critical supplies and medical evacuation are feasible because of the absence of a secure LOC. The commander must thoroughly plan for aerial resupply of the raiding force since it entails greater risk than normal operations. Under these conditions, units destroy damaged equipment that is unable to maintain the pace of the operation.
3-176. The commander's mission and intent determine the scheme of maneuver and the allocation of available resources. The commander reduces the scope of the initial mission if only a few resources are available. For example, a commander could tell his subordinates to clear their AOs of all enemy platoon-size and larger forces instead of clearing their areas of operation of all enemy forces if he lacks the time or forces needed to accomplish the latter task.
3-177. All planning for offensive operations address the factors of METT-TC, with special emphasis on—
Enemy positions, strengths, and capabilities.
Missions and objectives for each subordinate element and task and purpose for each BOS manager.
Commander's intent.
AOs for the use of each subordinate element with associated control graphics.
Time the operation is to begin.
Scheme of maneuver.
Special tasks required to accomplish the mission.
Risk.
Options for accomplishing the mission.
The commander and his staff translate the unit's assigned mission into specific objectives for all subordinates, to include the reserve. These objectives can involve any type or form of operations. If the type of operation assigned has associated forms, the commander may specify which form to use, but should minimize restrictions on his subordinates' freedom of action. FM 5-0 addresses the military decision making process and the format for plans and orders.
3-178. Prior planning and preparations that result in synchronizing the seven BOS increase a unit's effectiveness when executing operations. However, the fluid nature of combat requires the commander to guide the actions of his subordinates during the execution phase. The commander locates himself where he can best sense the flow of the operation and influence its critical points by redirecting the effects of committed forces or employing his reserve. This normally means that he is well forward in the combat formation, usually with the force designated to conduct the decisive operation. Once he makes contact with the enemy, he quickly moves to the area of contact, assesses the situation, and takes appropriate aggressive actions to direct the continuation of the offensive operation.
3-179. In addition to assigning objectives, commanders at all echelons consider how to exploit advantages that arise during operations and the seizure of intermediate and final objectives. The commander exploits success by aggressively executing the plan, taking advantage of junior leader initiative, and employing trained units capable of rapidly executing standard drills. His reserve also provides a flexible capability to exploit unforeseen advantages.
3-180. The commander always seeks to surprise his opponent throughout the operation. Information operations, such as deception, and the choice of an unexpected direction or time for conducting an offensive operation can result in the enemy being surprised. Surprise delays enemy reactions, overloads and confuses enemy C2, induces psychological shock, and reduces the coherence of his defenses. Tactical surprise is more difficult to achieve once hostilities begin, but it is still possible. The commander achieves tactical surprise by attacking in bad weather and over seemingly impassible terrain, conducting feints and demonstrations, making rapid changes in tempo, and employing sound OPSEC measures.
3-181. The commander should anticipate any requirements to shift his main effort during the offensive to press the fight and keep the enemy off balance. The commander develops decision points to support these changes using both human and technical means to validate his decision points.
3-182. The commander retains the capability to rapidly concentrate force effects, such as fires, throughout the extent of his AO during offensive operations. This capability is also critical to the commander when his force crosses linear obstacles. Lanes and gaps resulting from combined arms breaching operations or occurring naturally typically are choke points. There is a tendency for each subordinate element to move out independently as it completes its passage through the choke point. This independent movement detracts from the ability of the whole force to rapidly generate combat power on the far side of an obstacle.
3-183. The commander briefs his plan and the plans of adjacent units and higher echelons to his unit's leaders and soldiers. This helps units and soldiers moving into unexpected locations to direct their efforts toward accomplishing the mission. This exchange of information occurs in all operations.
3-184. The free flow of information between all force elements must be maintained throughout the offensive operation. This requires the commander to maintain communications with all elements of his unit. He plans how to position and reposition his information systems to maintain his common operational picture throughout the operation. The commander plans how to expand his communications coverage to accommodate increased distances as his force advances. Accordingly, he provides for redundant communication means—including wire, radio, visible and ultraviolet light, heat, smoke, audible sound, messengers, and event-oriented communications, such as the casualty-producing device that initiates an ambush.
3-185. A unit with advanced information systems and automated decision aids enjoys reduced engagement times and an enhanced planning process. This assists the unit commander's ability to control the operational tempo of the battle and stay within the enemy's decision making cycle. Greatly improved knowledge of the enemy and friendly situations facilitates the tactical employment of precision fires and decisive maneuver at extended ranges. These digital systems also enhance the commander's freedom to move to those battlefield locations where he can best influence the battle at the critical time and place.
3-186. A transition occurs when the commander makes the assessment that he must change his focus from one type of military operation to another. The following paragraphs explain why a commander primarily conducting offensive operations would transition to the defense and describe techniques that a commander can use to ease the transition.
3-187. A commander halts an offensive operation only when it results in complete victory and the end of hostilities, reaches a culminating point, or the commander receives a change in mission from his higher commander. This change in mission may be a result of the interrelationship of the other elements of national power, such as a political decision.
3-188. All offensive operations that do not achieve complete victory reach a culminating point when the balance of strength shifts from the attacking force to its opponent. Usually, offensive operations lose momentum when friendly forces encounter heavily defended areas that cannot be bypassed. They also reach a culminating point when the resupply of fuel, ammunition, and other supplies fails to keep up with expenditures, soldiers become physically exhausted, casualties and equipment losses mount, and repairs and replacements do not keep pace. Because of enemy surprise movements, offensive operations also stall when reserves are not available to continue the advance, the defender receives reinforcements, or he counterattacks with fresh troops. Several of these causes may combine to halt an offense. In some cases, the unit can regain its momentum, but this only happens after difficult fighting or after an operational pause.
3-189. If the attacker cannot anticipate securing decisive objectives before his force reaches its culminating point, he plans a pause to replenish his combat power and phases his operation accordingly. Simultaneously, he prevents the enemy from knowing when the friendly forces become overextended.
3-190. Once offensive operations begin, the attacking commander tries to sense when he reaches, or is about to reach, his culminating point. Before reaching this point, he must transition to some other type of military operation. The commander has more freedom to choose where and when he wants to halt the attack if he can sense that his forces are approaching culmination. He can plan his future activities to aid the defense, minimize vulnerability to attack, and facilitate renewal of the offense as he transitions to branches or sequels of the operation. For example, to prevent overburdening the extended LOCs resulting from the advances away from his sustaining base, some of the commander's subordinate units may move into assembly areas before he terminates the offense to start preparing for the ensuing defensive operation.
3-191. A lull in combat operations often accompanies transition. Civilians may present themselves to friendly forces during this period. The commander must consider how he will minimize the interference of these civilians with his military operations while protecting the civilians from future hostile actions. He must also consider the threat they pose to his force and its operations if enemy intelligence agents or saboteurs constitute a portion of the civilian population encountered.
3-192. A commander anticipating the termination of his offensive operation prepares orders that include the time or circumstances under which the offense transitions to another type of military operation, such as the defense, the missions and locations of subordinate units, and C2 measures. As he transitions from the offense to the defense, a commander takes the following actions:
Maintains contact and surveillance of the enemy, using a combination of reconnaissance units and surveillance assets to develop the information required to plan future actions.
Establishes a security area and local security measures.
Redeploys fire support assets to ensure the support of security forces.
Redeploys forces based on probable future employment.
Maintains or regains contact with adjacent units in a contiguous AO and ensures that his units remain capable of mutual support in a noncontiguous AO.
Transitions the engineer effort by shifting the emphasis from mobility to countermobility and survivability.
Consolidates and reorganizes.
Explains the rationale for transitioning from the offense to his soldiers.
3-193. The commander redeploys his air defense assets to cover the force's defensive position. A transition to the defense may require the commander to change his air defense priorities. For example, his top priority may have been coverage of maneuver units in the offense. This may shift to coverage of his long-range sensors and weapons in the defense.
3-194. The commander conducts any required reorganization and resupply concurrently with the above activities. This requires a transition in the logistics effort, with a shift in emphasis from ensuring the force's ability to move forward (POL and forward repair of maintenance and combat losses) to ensuring the force's ability to defend on its chosen location (forward stockage construction, barrier, and obstacle material, and ammunition). Transition is often a time in which equipment maintenance can be performed. Additional assets may also be available for casualty evacuation and medical treatment because of a reduction in the tempo.
3-195. The commander should not wait too long to transition from the offense to the defense as his forces approach their culminating point. Without prior planning, transitioning to defensive actions after reaching a culminating point is extremely difficult for several reasons. Defensive preparations are hasty, and forces are not adequately disposed for defense. Defensive reorganization requires more time than the enemy will probably allow. Usually, attacking forces are dispersed, extended in depth, and weakened in condition. Moreover, the shift to defense requires a psychological adjustment. Soldiers who have become accustomed to advancing must now halt and fight defensively—sometimes desperately—on new and often unfavorable terms.
3-196. A commander can use two basic techniques when he transitions to the defense. The first technique is for the leading elements to commit forces and push forward to claim enough ground to establish a security area anchored on defensible terrain. The main force moves forward or rearward as necessary to occupy key terrain and institutes a hasty defense that progresses into a deliberate defense as time and resources allow. The second technique is to establish a security area generally along the unit's final positions, moving the main body rearward to defensible terrain. The security force thins out and the remaining force deploys to organize the defense. In both methods, the security area should be deep enough to keep the main force out of the range of enemy medium artillery and rocket systems.
3-197. In the first technique, the security area often lacks depth because the force lacks sufficient combat power to seize required terrain. In the second technique, the enemy force will probably accurately template the forward trace of friendly units and engage with artillery and other fire support systems. These actions often result in the loss of additional friendly soldiers and equipment and the expenditure of more resources.
3-198. If a commander determines that it is necessary to break off an offensive operation and conduct a retrograde, he typically has his units conduct an area defense from their current locations until he can synchronize the retrograde operation. The amount of effort expended in establishing the area defense depends on the specific factors of METT-TC currently prevailing.