 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| When armies approach each other, it makes all the difference which owns only the ground on which it stands or sleeps and which one owns all the rest. |
| Winston Churchill: Their Finest Hour, 1949 |
Movement to contact is a type of offensive operation designed to develop the situation and establish or regain contact (FM 3-0). A commander conducts this type of offensive operation when the tactical situation is not clear or when the enemy has broken contact. A properly executed movement to contact develops the combat situation and maintains the commander's freedom of action after contact is gained. This flexibility is essential in maintaining the initiative. All of the tactical concepts, control measures, and planning considerations introduced in Chapters 2 and 3 apply to the conduct of a movement to contact. Many of the attack preparation consideration introduced in Chapter 5 also apply.
4-1. Purposeful and aggressive movement, decentralized control, and the hasty deployment of combined arms formations from the march to attack or defend characterize the movement to contact. The fundamentals of a movement to contact are—
Focus all efforts on finding the enemy.
Make initial contact with the smallest force possible, consistent with protecting the force.
Make initial contact with small, mobile, self-contained forces to avoid decisive engagement of the main body on ground chosen by the enemy. This allows the commander maximum flexibility to develop the situation.
Task-organize the force and use movement formations to deploy and attack rapidly in any direction.
Keep forces within supporting distances to facilitate a flexible response.
Maintain contact regardless of the course of action (COA) adopted once contact is gained.
Close air support, air interdiction, and counterair operations are essential to the success of large-scale movements to contact (MTCs). Local air superiority or, as a minimum, air parity is vital to the operation's success.
4-2. The Army's improved intelligence, surveillance, and reconnaissance (ISR) capabilities reduce the need for corps and divisions to conduct an MTC since fully modernized units normally have a general idea of the location of significant enemy forces. However, enemy use of complex terrain and offensive information operations designed to degrade the accuracy of the friendly common operational picture will continue to require small tactical units to conduct an MTC.
4-3. A meeting engagement is a combat action that occurs when a moving force engages an enemy at an unexpected time and place (JP 3-0). Conducting an MTC results in a meeting engagement. The enemy force may be either stationary or moving. Such encounters often occur in small-unit operations when reconnaissance has been ineffective. The force that reacts first to the unexpected contact generally gains an advantage over its opponent. However, a meeting engagement may also occur when the opponents are aware of each other and both decide to attack immediately to obtain a tactical advantage or seize key or decisive terrain. A meeting engagement may also occur when one force attempts to deploy into a hasty defense while the other force attacks before its opponent can organize an effective defense. Acquisition systems may discover the enemy before the security force can gain contact. No matter how the force makes contact, seizing the initiative is the overriding imperative. Prompt execution of battle drills at platoon level and below, and standard actions on contact for larger units can give that initiative to the friendly force.
4-4. The following vignette discusses the Soviet Manchurian Campaign in the closing days of World War II and illustrates the idea that tacticians can profit from the lessons learned by other armies in other times. It demonstrates the conduct of an MTC at the operational level.
|
4-5. A movement to contact is organized with an offensive covering force or an advance guard as a forward security element and a main body as a minimum. A portion of the main body composes the commander's sustaining base. Based on the factors of METT-TC, the commander may increase his security forces by having an offensive covering force and an advance guard for each column, as well as flank and rear security (normally a screen or guard). (See Figure 4-2.) Chapter 12 discusses security operations.
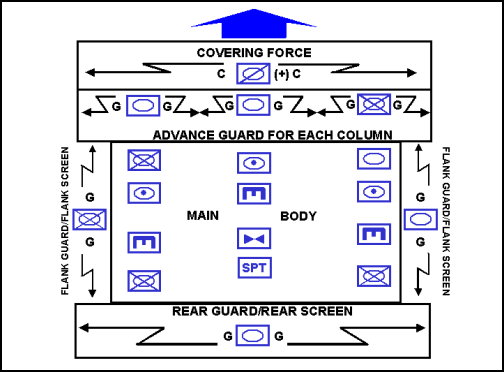
Figure 4-2. Force Organized for a Movement to Contact
4-6. A movement to contact mission requires the commander not to have contact with the enemy main body. However, the commander may still know the location of at least some enemy reserve and follow-on forces. If the corps or division commander has enough intelligence information to target enemy uncommitted forces, reserves, or sustaining operations activities, he normally designates forces, such as long-range artillery systems and attack helicopters, to engage known enemy elements regardless of their geographical location within his AO. At all times the forward security element and the main body perform reconnaissance.
4-7. A corps or division commander conducting an MTC typically organizes his security element into a covering force to protect the movement of the main body and to develop the situation before committing the main body. A covering force is task-organized to accomplish specific tasks independent of the main body in accordance with the factors of METT-TC, such as conduct mobility and breach operations. This covering force reports directly to the establishing commander.
4-8. If a force conducting an MTC is unable to resource a covering force for independent security operations, it may use an advance guard in the place of a covering force. An advance guard is a task-organized combined arms unit or detachment that precedes a column formation to protect the main body from ground observation or surprise by the enemy. This typically occurs when a brigade or battalion conducts an MTC. In cases where the higher echelon (corps or division) creates a covering force, subordinate elements can establish an advance guard behind the covering force and ahead of the main body. This normally occurs when subordinate units are advancing in multiple parallel columns. In this case, each main body column usually organizes its own advance guard.
4-9. The advance guard operates forward of the main body to ensure its uninterrupted advance by reducing obstacles to create passage lanes, repair roads and bridges, or locate bypasses. The advance guard also protects the main body from surprise attack and fixes the enemy to protect the deployment of the main body when it is committed to action. The elements composing the advance guard should have equal or preferably superior mobility to that of the main body. For this reason, mechanized infantry, cavalry, and armored units are most suitable for use in an advance guard. Engineer mobility assets should also constitute a portion of the advance guard, but the main body can also provide other support.
4-10. The advance guard moves as quickly and as aggressively as possible, but, unlike the covering force, remains within supporting range of the main body's weapon systems. It forces the enemy to withdraw or destroys small enemy groups before they can disrupt the advance of the main body. When the advance guard encounters large enemy forces or heavily defended areas, it takes prompt and aggressive action to develop the situation and, within its capability, defeat the enemy. Its commander reports the location, strength, disposition, and composition of the enemy and tries to find the enemy's flanks and gaps or other weaknesses in his position. The main body may then join the attack. The force commander usually specifies how far in front of his force the advance guard is to operate. He reduces those distances in close terrain and under low-visibility conditions.
4-11. When the command's rear or flanks are not protected by adjacent or following units, it must provide its own flank and rear security. The command can accomplish this by establishing a screen or a guard on its flanks or to its rear. The flank columns of the main body normally provide these flank security elements; for example, the left flank brigade would provide the left flank screen for a division MTC. The rear guard normally comes from one of the subordinate elements of the corps or division and reports directly to the corps or division headquarters. A corps may conduct a flank cover if there is a clearly identified, significant threat from the flank. A flank cover requires significant resources that are unavailable to the main body. Aviation units or intelligence systems may establish a flank screen if the factors of METT-TC allow; however, this increases the risk to the main body. While aviation units can use their combat power to delay enemy forces, intelligence systems can only provide early warning, they cannot trade space for time to "buy" time for the main body to react. (For more specific information concerning reconnaissance operations see FM 3-55. See Chapter 12 for more detailed information concerning security operations.)
4-12. The main body consists of forces not detailed to security duties. The combat elements of the main body prepare to respond to enemy contact with the unit's security forces. Attack helicopter units normally remain under division and corps control until contact is made. If the situation allows, the commander can assign a follow and support mission to one of his subordinate units. This allows that subordinate unit to relieve his security forces from such tasks as observing bypassed enemy forces, handling displaced civilians, and clearing routes. This prevents his security forces from being diverted from their primary mission.
4-13. The commander designates a portion of the main body for use as his reserve. The size of the reserve is based upon the factors of METT-TC and the amount of uncertainty concerning the enemy. The more vague the enemy situation, the larger the size of the reserve. The reserve typically constitutes approximately one-fourth to one-third of the force. On contact with the enemy, the reserve provides the commander flexibility to react to unforeseen circumstances and allows the unit to quickly resume its movement.
4-14. The commander tailors his sustainment assets to the mission. He decentralizes the execution of the sustainment support, but that support must be continuously available to the main body. This includes using preplanned logistics packages (LOGPACs). A logistics package is a grouping of multiple classes of supply and supply vehicles under the control of a single convoy commander. Daily LOGPACs contain a standardized allocation of supplies. Special LOGPACs can also be dispatched as needed.
4-15. The commander frequently finds that his main supply routes become extended as the operation proceeds. Aerial resupply may also be necessary to support large-scale MTCs or to maintain the momentum of the main body. Combat trains containing fuel, ammunition, medical, and maintenance assets move with their parent battalion or company team. Fuel and ammunition stocks remain loaded on tactical vehicles in the combat trains so they can instantly move when necessary. Battalion field trains move in more depth, with the forward support battalion in the main body of each brigade. Aviation units use forward arming and refuel points (FARPs) to reduce aircraft turnaround time.
4-16. A commander uses the minimal number and type of control measures possible in an MTC because of the uncertain enemy situation. These measures include designation of an AO with left, right, front, and rear boundaries, or a separate AO bounded by a continuous boundary (noncontiguous operations). The commander further divides the AO into subordinate unit AOs to facilitate subordinate unit actions.
4-17. The operation usually starts from a line of departure (LD) at the time specified in the operations order (OPORD). The commander controls the MTC by using phase lines, contact points, and checkpoints as required. (See Figure 4-3.) He controls the depth of the movement to contact by using a limit of advance (LOA) or a forward boundary. Figure 4-3 shows an LOA and not a forward boundary. The commander could designate one or more objectives to limit the extent of the MTC and orient the force. However, these are often terrain-oriented and used only to guide movement. Although an MTC may result in taking a terrain objective, the primary focus should be on the enemy force. If the commander has enough information to locate significant enemy forces, then he should plan some other type of offensive action.
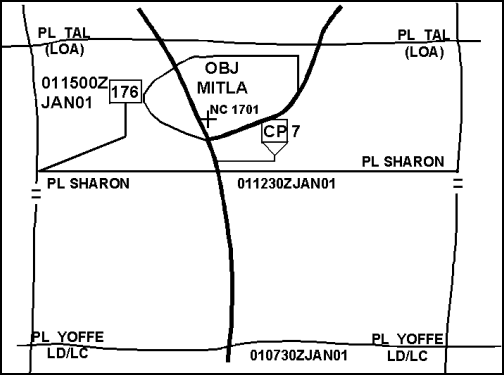
Figure 4-3. Movement to Contact Control Measures
4-18. Corps, division, or brigade commanders use boundaries to separate the various organizational elements of a movement to contact and clearly establish responsibilities between different organizations. Battalion task force commanders use positive control over maneuver units, coupled with battle drills and formation discipline. Company teams are not normally assigned their own areas of operation during the conduct of a movement to contact.
4-19. The commander can designate a series of phase lines that can successively become the new rear boundary of the forward security elements as that force advances. Each rear boundary becomes the forward boundary of the main body and shifts as the security force moves forward. The rear boundary of the main body designates the limit of responsibility of the rear security element. This line also shifts as the main body moves forward. (See Chapter 12 for a discussion of boundaries for a security force.)
4-20. Commanders may use an axis of advance in limited visibility. However, there is the risk of enemy forces outside the axis not being detected, and thus being inadvertently bypassed.
4-21. The commander conducts intelligence, surveillance, and reconnaissance operations to determine the enemy's location and intent while conducting security operations to protect the main body. This includes the use of available fixed-wing aircraft. This allows the main body to focus its planning and preparation, to include rehearsals, on the conduct of hasty attacks, bypass maneuvers, and hasty defenses. The plan addresses not only actions anticipated by the commander based on available intelligence information but also the conduct of meeting engagements at anticipated times and locations where they might occur.
4-22. The commander wants to gain contact by using the smallest elements possible. These elements are normally ground scouts or aeroscouts performing reconnaissance, but may also be unmanned aerial vehicles (UAVs) or other intelligence systems. He may task organize his scouts to provide them with additional combat power to allow them to develop the situation. The unit's planned movement formation should contribute to the goal of making initial contact with the smallest force possible. It should also provide for efficient movement of the force and adequate reserves. The commander can choose to have all or part of his force conduct an approach march as part of the movement to contact to provide that efficient movement. An approach march can facilitate the commander's decisions by allowing freedom of action and movement of the main body. (See Chapter 14 for a discussion of an approach march.)
4-23. The frontage assigned to a unit in a movement to contact must allow it to generate sufficient combat power to maintain the momentum of the operation. Reducing the frontage covered normally gives the unit adequate combat power to develop the situation on contact while maintaining the required momentum. Both the covering force and advance guard commanders should have uncommitted forces available to develop the situation without requiring the deployment of the main body. The commander relies primarily on fire support assets to weight the lead element's combat power but provides it with the additional combat multipliers it needs to accomplish the mission. The fire support system helps develop fire superiority when organized correctly to fire immediate suppression missions to help maneuver forces get within direct-fire range of the enemy.
4-24. The reconnaissance effort may proceed faster in a movement to contact than in a zone reconnaissance because the emphasis is on making contact with the enemy. However, the commander must recognize that by increasing the speed of the reconnaissance effort, he increases the risk associated with the operation.
4-25. Bypass criteria should be clearly stated and depend on the factors of METT-TC. For example, a brigade commander in an open desert environment could declare that no mounted enemy force larger than a platoon can be bypassed. All other forces will be cleared from the brigade's axis of advance. Any force that bypasses an enemy unit must maintain contact with it until handing it off to another friendly element, usually a force assigned a follow and support mission. The commander tasks his forward security force with conducting route reconnaissance of routes the main body will traverse.
4-26. The echelon intelligence officer (G2 or S2), assisted by the engineer and air defense staff representatives, must carefully analyze the terrain to include air avenues of approach. He identifies the enemy's most dangerous COA in the war gaming portion of the military decision making process. Because of the force's vulnerability, the G2 must not underestimate the enemy during a movement to contact. A thorough intelligence preparation of the battlefield (IPB)—by developing the modified combined obstacle overlay to include intervisibility overlays and other products, such as the event templates—enhances the force's security by indicating danger areas where the force is most likely to make contact with the enemy. It also helps to determine movement times between phase lines and other locations. Potential danger areas are likely enemy defensive locations, engagement areas, observation posts (OPs), and obstacles. The fire support system targets these areas and they become on-order priority targets placed into effect and cancelled as the lead element can confirm or deny enemy presence. The reconnaissance and surveillance plan supporting the movement to contact must provide coverage of these danger areas. If reconnaissance and surveillance forces cannot clear these areas, more deliberate movement techniques are required.
4-27. The commander develops decision points to support changes in the force's movement formation or change from an approach march to a combat formation. Uses both human and technical means to validate his decision points, the commander must determine the degree of risk he is willing to accept based on his mission. The commander's confidence in the products of the IPB process and the risk he is willing to accept determine his combat formation and maneuver scheme. In a high-risk environment, it is usually better to increase the distance between forward elements and the main body than to slow the speed of advance.
4-28. Corps and divisions can execute shaping operations as part of a movement to contact although, by definition, a force conducts a movement to contact when the enemy situation is vague or totally unknown. This occurs when the necessary information regarding enemy reserves and follow-on forces is available, but information regarding those enemy forces in close proximity to the friendly force is not available. As in any other type of operation, the commander plans to focus his operations on finding the enemy and then delaying, disrupting, and destroying each enemy force element as much as possible before it arrives onto the direct-fire battlefield. This allows close combat forces to prepare to engage enemy units on their arrival.
4-29. In a movement to contact, the commander can opt not to designate his decisive operation until his forces make contact with the enemy, unless there is a specific reason to designate it. In this case, he retains resources under his direct control to reinforce his decisive operation. He may designate his decisive operation during the initial stages of a movement to contact because of the presence of a key piece of terrain or avenue of approach.
4-30. Each element of the force synchronizes its actions with adjacent and supporting units, maintaining contact and coordination as prescribed in orders and unit standing operating procedures (SOP). The advance guard maintains contact with the covering force. The lead elements of the main body maintain contact with the advance guard. The rear guard and flank security elements maintain contact with and orient on the main body's movement. These security forces prevent unnecessary delay of the main body and defer the deployment of the main body as long as possible. Reconnaissance elements operate to the front and flanks of each column's advance guard and maintain contact with the covering force. The commander may instruct each column's advance guard to eliminate small pockets of resistance bypassed by forward security force. (See Figure 4-4.)
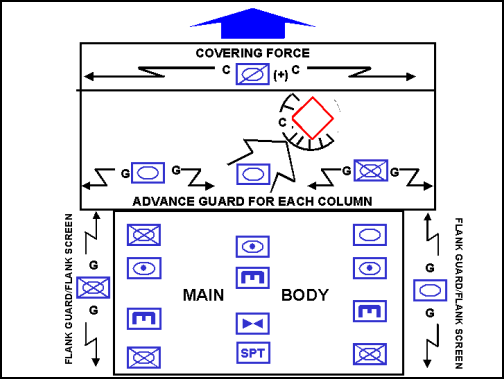
Figure 4-4. A Column Advance Guard Attacking to Destroy a Contained Enemy Force
4-31. The commander of the advance guard chooses a combat formation, based on the factors of METT-TC, to make contact with the smallest possible force while providing flexibility for maneuver. Whatever combat formation is chosen, it must be able to deploy appropriately once the commander becomes aware of the enemy's location. He ensures that the route or axis of advance traveled by the main body is free of enemy forces. It may move continuously (traveling and traveling overwatch) or by bounds (bounding overwatch). It moves by bounds when contact with the enemy is imminent and the terrain is favorable. Some indirect-fire assets, such as a mortar platoon or artillery battery and combat observation and lasing teams (COLTs), may be positioned with the formation. The COLTs can help overwatch the advance guard movement, and indirect fires focus on suppressing enemy weapons, obscuring enemy observation posts, and screening friendly movement.
4-32. The main body keeps enough distance between itself and its forward security elements to maintain flexibility for maneuver. This distance varies with the level of command, the terrain, and the availability of information about the enemy. The main body may execute an approach march for all or part of the movement to contact to efficiently use the available road network or reduce the time needed to move from one location to another. Command posts and trains travel along high-mobility routes within the AO and occupy hasty positions as necessary.
4-33. Behind these forward security elements, the main body advances over multiple parallel routes with numerous lateral branches to remain flexible and reduce the time needed to initiate maneuver. (While it is preferred for a battalion to use multiple routes, battalions and smaller units can move on just one route.) In a movement to contact, the main body's march dispositions must allow maximum flexibility for maneuvering during movement and when establishing contact with the enemy force.
4-34. The commander's fire support systems tend to focus on suppression missions to disrupt enemy forces as they are encountered and smoke missions to obscure or screen exposed friendly forces when conducting a movement to contact. The commander schedules the movements of fire support systems in synchronization with the movement of the rest of the force. Fire support systems that cannot match the cross-country mobility of the combat units cause them to slow their rate of advance. If these units do not slow down, they run the risk of outrunning their fire support. The commander synchronizes the employment of close air support to prevent the enemy from regaining his balance while his ground fire support assets are repositioning. The main body updates its priority target list during a movement to contact operation.
4-35. The same considerations apply to air defense when the enemy possesses aerial capabilities. The commander ensures that his force stays within the air defense umbrella provided by corps and division assets.
4-36. The enemy has a difficult time detecting and targeting the main body when executing a movement to contact until contact is made because of its tempo, momentum, and dispersal; and the attention the commander pays to electromagnetic emission control. Once the force makes contact and concentrates its effects against detected enemy forces, it becomes vulnerable to strikes by enemy conventional weapons and weapons of mass destruction. It must concentrate its combat effects rapidly and disperse again as soon as it overcomes resistance to avoid enemy counteractions.
4-37. Movement should be as rapid as the terrain, the mobility of the force, and the enemy situation permit. Open terrain provides maneuver space on either side of the line of march and facilitates high-speed movement. It also allows for greater dispersal and usually permits more separation between forward security elements and the main body than restricted terrain allows. The commander should never commit his main body to canalizing terrain before these forward security elements have advanced far enough to ensure that the main body will not become fixed within that terrain. The enemy may have also established fire support control measures that allow him to employ nonobserved harassing and interdiction fires to interdict friendly forces traversing these choke points. As the enemy situation becomes known, the commander may shorten the distance between elements of the force to decrease reaction time or he may deploy to prepare for contact.
4-38. At the battalion and company levels, a moving force should move along covered or concealed routes from one covered or concealed position to another, using terrain to minimize its vulnerability to enemy weapons. Further, an overwatching force should cover the moving force. (Chapter 14 describes movement techniques, such as traveling overwatch.) Regardless of the specific movement technique employed, both forces need to provide mutual support and be knowledgeable about their counterpart's sectors of fire.
4-39. The force must attempt to cross any obstacles it encounters without loss of momentum by conducting in-stride breaches. The commander uses his forward security forces in an attempt to seize intact bridges whenever possible. Lead security elements bypass or breach obstacles as quickly as possible to maintain the momentum of the movement. If these lead elements cannot overcome obstacles, the commander directs subsequent elements of the main body to bypass the obstacle site and take the lead. Following forces can also reduce obstacles that hinder the unit's sustainment flow.
4-40. The commander locates himself well forward in the movement formation. Once the formation makes contact with the enemy, he can move quickly to the area of contact, analyze the situation, and direct aggressively. The commander's security elements conduct actions on contact to develop the situation once they find the enemy. Once they make contact with the enemy, a number of actions occur that have been divided into the following sequence. (Units equipped with a full set of digital command and control systems may be able to combine or skip one or more of the steps in that sequence. Those units will conduct maneuver and remain within supporting distance of each other with a significantly larger AOs than units equipped with analog systems.)
4-41. All ISR assets focus on determining the enemy's dispositions and providing the commander with current intelligence and relevant combat information; this ensures that he can commit friendly forces under optimal conditions. The commander uses all available sources of combat information to find the enemy's location and dispositions in addition to his intelligence systems. Corps and divisions employ long-range surveillance units and detachments in conjunction with data provided by available special operating forces, joint, and multinational assets, in addition to their organic ISR assets. The commander may use his surveillance systems to cue the conduct of aerial and ground reconnaissance.
4-42. The enemy situation becomes clearer as the unit's forward security elements conduct actions on contact to rapidly develop the situation in accordance with the commander's plan and intent. By determining the strength, location, and disposition of enemy forces, these security elements allow the commander to focus the effects of the main body's combat power against the enemy main body. The overall force must remain flexible to exploit both intelligence and combat information. The security force should not allow the enemy force to break contact unless it receives an order from the commander. When a strong covering force has not preceded the advance guard, it should seize terrain that offers essential observation.
4-43. Actions on contact are a series of combat actions often conducted simultaneously taken on contact with the enemy to develop the situation. Actions on contact are:
Deploy and report.
Evaluate and develop the situation.
Choose a course of action.
Execute selected course of action
Recommend a course of action to the higher commander.
4-44. Once the lead elements of a force conducting a movement to contact encounter the enemy, they conduct actions on contact. The unit treats obstacles like enemy contact, since it assumes that the obstacles are covered by fire. The unit carries out these actions on contact regardless of whether the enemy has detected its presence. The unit's security force often gains a tactical advantage over an enemy force by using tempo and initiative to conduct these actions on contact, allowing it to gain and maintain contact without becoming decisively engaged. How quickly the unit develops the situation is directly related to its security. This tempo is directly related to the unit's use of well-rehearsed SOP and drills.
4-45. When a unit's security element encounters an enemy unit or obstacle, it deploys to a covered position that provides observation and fields of fire. If the security element is under enemy fire, it uses direct and indirect fire to suppress the enemy and restore freedom of maneuver. Simultaneously, the commander of the security element reports the contact using a spot report format to provide all available information on the situation to his higher headquarters. This alerts the commander and allows him to begin necessary actions. (FM 6-99.2 provides the format for a spot report.)
4-46. The unit's security force develops the situation rapidly within mission constraints by employing techniques ranging from stealthy, foot-mobile reconnaissance to reconnaissance by fire, which uses both direct and indirect weapons. If possible the commander continues the security mission with other elements not currently in contact with the enemy after evaluating the situation. This helps to develop the situation across the front and provides more maneuver space to execute further actions. As the situation develops, the security force submits additional reports.
4-47. After the security force makes contact, its commander gathers information, makes an assessment, and chooses a course of action (COA) consistent with his higher commander's intent and within the unit's capability. The unit initiates direct and indirect fires to gain the initiative if it is appropriate to engage the enemy. This allows the security force to resume its mission as soon as possible. The commander cannot allow small enemy forces to delay the movement of the security force. Usually, available intelligence and the concept of the operation indicate the COA to follow. For obstacles not covered by fire, the unit can either seek a bypass or create the required number of lanes to support its maneuver or the maneuver of a supported unit. Once enemy contact is made, these COAs are normally to conduct an attack, bypass, defend, delay, or withdrawal. For obstacles covered by fire, the unit can either seek a bypass or conduct breaching operations as part of a hasty attack.
4-48. The security force commander should determine quickly whether to bypass the enemy or attack. The security force attacks (see Chapter 5) if it has sufficient, immediately available combat power to overwhelm the enemy and the attack will not detract from mission accomplishment. Such attacks are usually necessary to overcome enemy attempts to slow the movement of the security force. If this initial attack fails to defeat enemy defenses, the security force commander must consider other options, such as making a more deliberate attack or assuming the defense while continuing to find out as much as possible about the enemy's positions.
4-49. The security force may bypass the enemy if it does not have sufficient combat power or an attack would jeopardize mission accomplishment. It must request permission to bypass an enemy force unless the operations order provides bypass criteria. The security force commander must report bypassed enemy forces to the next higher headquarters, which then assumes responsibility for their destruction or containment. Alternatively, the security force could keep a minimum force in contact with the bypassed enemy so that he cannot move freely around the battlefield. (See Appendix B for a discussion of bypass as a tactical task.)
4-50. If the security force cannot conduct either a hasty attack or a bypass, it attempts to establish a defense (see Chapter 8). In the defense, the security force maintains enemy contact, continues to perform reconnaissance, and prepares to support other forces. When the security force commander decides to defend, responsibility for further action rests with his higher commander. In the event other COAs would lead to decisive engagements or destruction, the security force conducts those activities necessary to assure self-preservation, such as delay or withdrawal (see Chapter 11), but maintains enemy contact unless the higher commander orders otherwise.
4-51. Once the security force commander selects a COA keeping in mind his commander's intent, he reports it to his higher commander, who has the option of disapproving it based on its impact on his mission. To avoid delay, unit SOP may provide automatic approval of certain actions. If the higher commander assumes responsibility for continuing to develop the situation, the security force supports his actions as ordered. The higher commander must be careful to avoid becoming overly focused on initial security fights to the determent of operations directed against the enemy main body.
4-52. Once contact is made, the main body commander brings overwhelming fires onto the enemy to prevent him from conducting either a spoiling attack or organizing a coherent defense. The security force commander maneuvers as quickly as possible to find gaps in the enemy's defenses. The commander uses his ISR assets to gain as much information as possible about the enemy's dispositions, strengths, capabilities, and intentions. As more intelligence becomes available, the main body commander attacks to destroy or disrupt enemy command and control (C2) centers, fire control nodes, and communication nets. The main body commander conducts operations to prevent enemy reserves from moving to counter his actions.
4-53. The commander tries to initiate maneuver at a tempo the enemy cannot match, since success in a meeting engagement depends on effective actions on contact. The security force commander does not allow the enemy to maneuver against the main body. The organization, size, and combat power of the security force are the major factors that determine the size of the enemy force it can defeat without deploying the main body.
4-54. The commander uses his aerial maneuver and fire support assets—including offensive information operations—to fix the enemy in his current positions by directly attacking his combat and command systems and emplacing situational obstacles. The priorities are typically to attack enemy forces in contact, C2 and fire control facilities, fire support assets, and moving enemy forces not yet in contact, such as follow-on forces and reserves. These priorities vary with the factors of METT-TC. Attack helicopters and close air support fixed-wing aircraft working in joint air attack teams (JAAT) are ideally suited to engage the enemy throughout the depth of his area of operations.
4-55. The techniques a commander employs to fix the enemy when both forces are moving are different than those employed when the enemy force is stationary during the meeting engagement. In both situations, when the security force cannot overrun the enemy by conducting a hasty frontal attack, he must deploy a portion of the main body. When this occurs the unit is no longer conducting a movement to contact but an attack.
4-56. If the security force cannot overrun the enemy with a frontal attack, the commander quickly maneuvers his main body to conduct a penetration or an envelopment. (See Chapter 5 for a discussion of attack.) He does this to overwhelm the enemy force before it can react effectively or reinforce. The commander attempts to defeat the enemy in detail while still maintaining the momentum of his advance. After a successful attack, the main body commander resumes the movement to contact. If he did not defeat the enemy he has three main options: bypass, transition to a more deliberate attack, or conduct some type of defense. In all cases, he makes every effort to retain the initiative and prevent the enemy from stabilizing the situation by conducting violent and resolute attacks. Simultaneously he must maintain his momentum by synchronizing the actions of his combat, combat support, and combat service support elements.
4-57. Main body elements deploy rapidly to the vicinity of the contact if the commander initiates a frontal attack. Commanders of maneuvering units coordinate forward passage through friendly forces in contact as required. The intent is to deliver the assault before the enemy can deploy or reinforce his engaged forces. The commander may order an attack from a march column for one of the main body's columns, while the rest of the main body deploys. The commander can also wait to attack until he can bring the bulk of the main body forward. He avoids piecemeal commitment except when rapidity of action is essential and combat superiority at the vital point is present and can be maintained throughout the attack, or when compartmentalized terrain forces such a COA.
4-58. When trying to conduct an envelopment, the commander focuses on attacking the enemy's flanks and rear before he can prepare to counter these actions. The commander uses the security force to fix the enemy while the main body maneuvers to look for an assailable flank or he uses the main body to fix the enemy while the security force finds the assailable flank.
4-59. If the enemy is defeated, the unit transitions back into an MTC and continues to advance. The movement to contact terminates when the unit reaches the final objective or limit of advance, or it must transition to a more deliberate attack, a defense, or retrograde. (For more discussion of these types of operations, see the respective chapters in this manual.)
4-60. Search and attack is a technique for conducting a movement to contact that shares many of the characteristics of an area security mission (FM 3-0). A commander employs this form of a movement to contact, conducted primarily by light forces and often supported by heavy forces, when the enemy is operating as small, dispersed elements, or when the task is to deny the enemy the ability to move within a given area. The battalion is the echelon that normally conducts a search and attack. A brigade will assist its subordinate battalions by ensuring the availability of indirect fires and other support.
4-61. The commander task organizes his unit into reconnaissance, fixing, and finishing forces, each with a specific purpose and task. The size of the reconnaissance force is based on the available intelligence about the size of enemy forces in the AO. The less known about the situation, the larger the reconnaissance force. The reconnaissance force typically consists of scout, infantry, aviation, and electronic warfare assets. The fixing force must have enough combat power to isolate the enemy once the reconnaissance force finds him. The finishing force must have enough combat power to defeat those enemy forces expected to be located within the AO. The commander can direct each subordinate unit to retain a finishing force, or he can retain the finishing force at his echelon. The commander may rotate his subordinate elements through the reconnaissance, fixing, and finishing roles. However, rotating roles may require a change in task organization and additional time for training and rehearsal.
4-62. The commander establishes control measures that allow for decentralized actions and small-unit initiative to the greatest extent possible. The minimum control measures for a search and attack are an AO, target reference points (TRPs), objectives, checkpoints, and contact points. (See Figure 4-5.) The use of TRPs facilitates responsive fire support once the reconnaissance force makes contact with the enemy. The commander uses objectives and checkpoints to guide the movement of subordinate elements. Coordination points indicate a specific location for coordinating fires and movement between adjacent units. The commander uses other control measures, such as phase lines, as necessary. (See Chapters 2 and 3 for definitions of available control measures.)
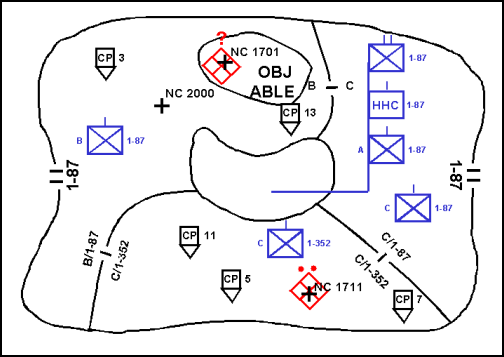
Figure 4-5. Search and Attack Control Measures
4-63. A commander conducts a search and attack for one or more of the following purposes:
Destroy the enemy: render enemy units in the AO combat-ineffective.
Deny the area: prevent the enemy from operating unhindered in a given area; for example, in any area he is using for a base camp or for logistics support.
Protect the force: prevent the enemy from massing to disrupt or destroy friendly military or civilian operations, equipment, property, and key facilities.
Collect information: gain information about the enemy and the terrain to confirm the enemy COA predicted as a result of the IPB process.
4-64. The products of the IPB process are critical to conducting a search and attack. They focus the force's reconnaissance efforts on likely enemy locations.
4-65. The search and attack plan places the finishing force, as the decisive operation, where it can best maneuver to destroy enemy forces or essential facilities once located by reconnaissance assets. Typically, the finishing force occupies a central location in the AO. However, the factors of METT-TC may allow the commander to position the finishing force outside the search and attack area. The commander weights this decisive operation by using priority of fires and assigning priorities of support to his other available combat multipliers, such as engineer elements and helicopter lift support. The commander establishes control measures as necessary to consolidate units and concentrate the combat power of the force before the attack. Once the reconnaissance force locates the enemy, the fixing and finishing forces can fix and destroy him. The commander also develops a contingency plan in the event that the reconnaissance force is compromised.
4-66. Fire support plans must provide for flexible and rapidly delivered fires to achieve the commander's desired effects throughout the AO. The commander positions his fire support assets so they can support subordinate elements throughout the AO. The commander must establish procedures for rapidly clearing fires. To clear fires rapidly, command posts and small-unit commanders must track and report the locations of all subordinate elements. Because of the uncertain enemy situation, the commander is careful to assign clear fire-support relationships.
4-67. Each subordinate element operating in its own AO is tasked to destroy the enemy within its capability. The commander should have in place previously established control measures and communications means between any closing elements to prevent fratricide. The reconnaissance force conducts a zone reconnaissance to reconnoiter identified named areas of interest (NAIs).
4-68. Once the reconnaissance force finds the enemy force, the fixing force develops the situation, then executes one of two options based on the commander's guidance and the factors of METT-TC. The first option is to block identified routes that the detected enemy can use to escape or rush reinforcement over. The fixing force maintains contact with the enemy and positions its forces to isolate and fix him before the finishing force attacks. The second option is to conduct an attack to fix the enemy in his current positions until the finishing force arrives. The fixing force attacks if that action meets the commander's intent and it can generate sufficient combat power against the detected enemy. Depending on the enemy's mobility and the likelihood of the reconnaissance force being compromised, the commander may need to position his fixing force before his reconnaissance force enters the AO.
4-69. Brigades (and possibly battalions) may establish fire-support bases as part of the operations of their fixing force to provide fire-support coverage throughout the area of operations during search and attack operations conducted in restricted terrain. These positions should be mutually supporting and prepared for all-around defense. They are located in positions that facilitate aerial resupply. The development of these positions depends on the factors of METT-TC because their establishment requires diverting combat power to ensure protecting fire support and other assets located within such bases.
4-70. If conditions are not right to use the finishing force to attack the detected enemy, the reconnaissance or the fixing force can continue to conduct reconnaissance and surveillance activities to further develop the situation. Whenever this occurs, the force maintaining surveillance must be careful to avoid detection and possible enemy ambushes.
4-71. The finishing force may move behind the reconnaissance and fixing forces, or it may locate at a pickup zone and air assault into a landing zone near the enemy once he is located. The finishing force must be responsive enough to engage the enemy before he can break contact with the reconnaissance force or the fixing force. The echelon intelligence officer provides the commander with an estimate of the time it will take the enemy to displace from his detected location. The commander provides additional mobility assets so the finishing force can respond within that timeframe.
4-72. The commander uses his finishing force to destroy the detected and fixed enemy during a search and attack by conducting hasty or deliberate attacks, maneuvering to block enemy escape routes while another unit conducts the attack, or employing indirect fire or close air support to destroy the enemy. The commander may have his finishing force establish an area ambush and use his reconnaissance and fixing forces to drive the enemy into the ambushes.