 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| I approve of all methods of attacking provided they are directed at the point where the enemy's army is weakest and where the terrain favors them the least. |
| Frederick the Great |
An attack is an offensive operation that destroys or defeats enemy forces, seizes and secures terrain, or both (FM 3-0). When the commander decides to attack or the opportunity to attack occurs during combat operations, the execution of that attack must mass the effects of overwhelming combat power against selected portions of the enemy force with a tempo and intensity that cannot be matched by the enemy. The resulting combat should not be a contest between near equals. The attacker must be determined to seek decision on the ground of his choosing through the deliberate synchronization and employment of his combined arms team.
5-1. Attacks take place along a continuum defined at one end by fragmentary orders that direct the execution of rapidly executed battle drills by forces immediately available. Published, detailed orders with multiple branches and sequels; detailed knowledge of all aspects of enemy dispositions; a force that has been task organized specifically for the operation; and the conduct of extensive rehearsals define the other end of the continuum. Most attacks fall between the ends of the continuum as opposed to either extreme. (Chapter 1 discusses this continuum between hasty and deliberate operations.)
5-2. Once a commander determines his scheme of maneuver, he task organizes his force to give each unit enough combat power to accomplish its mission. He normally organizes into a security force, a main body, a reserve, and a sustainment organization. He should complete any changes in task organization in time to allow units to conduct rehearsals with their attached or supported unit. The best place and time for an attacking force to task organize is when it is in an assembly area.
5-3. Under normal circumstances, a commander resources dedicated security forces during an attack only if the attack uncovers one or more flanks or the rear of the attacking force as it advances. In this case, the commander designates a flank or rear security force and assigns it a guard or screen mission, depending on the factors of METT-TC. Normally an attacking unit does not need extensive forward security forces; most attacks are launched from positions in contact with the enemy, which reduces the usefulness of a separate forward security force. The exception occurs when the attacking unit is transitioning from the defense to an attack and had previously established a security area as part of the defense.
5-4. The commander organizes his main body into combined arms formations to conduct his decisive operation and necessary shaping operations. The commander aims his decisive operation toward the immediate and decisive destruction of the enemy force, its will to resist, seizure of a terrain objective, or the defeat of the enemy's plan. His maneuver scheme identifies the focus of the decisive operation. All of the force's available resources operate in concert to assure the success of the decisive operation. The subordinate unit or units designated to conduct the decisive operation can change during the course of the attack. The commander designates an assault, breach, and support force if he expects to conduct a breach operation during his attack.
5-5. If it is impractical to determine initially when or where the echelon's decisive operation will be, such as during a hasty attack, the commander retains flexibility by arranging his forces in depth, holding out strong reserves, and maintaining centralized control of his long-range fire support systems. As soon as the tactical situation clarifies enough to allow the commander to designate his decisive operation, he focuses his resources to support that decisive operation's achievement of its objective. Enemy actions, minor changes in the situation, or the lack of success by other elements cannot be allowed to divert either forces or their effects from the decisive operation.
5-6. The commander may need to designate a unit or units to conduct shaping operations to create windows of opportunity for executing his decisive operation. He allocates the unit or units assigned to conduct shaping operations the minimal combat power necessary to accomplish the missions since he cannot employ overwhelming combat power everywhere. Units conducting shaping operations usually have a wider area of operations (AO) than those conducting a decisive operation. If the commander has sufficient forces as part of his shaping operations, he can assign the tasks of follow and assume or follow and support to subordinate units. (Appendix B defines these two tactical mission tasks.)
5-7. The commander uses his reserve to exploit success, defeat enemy counterattacks, or restore momentum to a stalled attack. Once committed, the reserve's actions normally become or reinforce the echelon's decisive operation, and the commander makes every effort to reconstitute another reserve from units made available by the revised situation. Often a commander's most difficult and important decision concerns the time, place, and circumstances for committing the reserve. The reserve is not a committed force, it is not used as a follow and support force or a follow and assume force.
5-8. In the attack, the combat power allocated to the reserve depends primarily on the level of uncertainty about the enemy, especially the strength of any expected enemy counterattacks. The commander only needs to resource a small reserve to respond to unanticipated enemy reactions when he has detailed information about the enemy. When the situation is relatively clear and enemy capabilities are limited, the reserve may consist of a small fraction of the command. When the situation is vague, the reserve may initially contain the majority of the commander's combat power.
5-9. In addition, the strength and composition of the reserve vary with the reserve's contemplated missions, the forces available, the form of offensive maneuver selected, the terrain, and acceptable risk. For example, in a hasty attack the reserve can contain up to one-third of the force's combat power. Alternatively, in a deliberate attack the reserve is normally sized to defeat the enemy's counterattack forces. The commander should not constitute his reserve by weakening his decisive operation. A reserve must have mobility equal to or greater than the most dangerous enemy ground threat, and be able to fight that threat.
5-10. In an attack the commander generally locates his reserve to the rear of the unit making his decisive operation in a location that provides maximum protection from hostile observation and fire. However, it must be able to move quickly to areas where it is needed in different contingencies. This is most likely to occur if the enemy has strong counterattack forces. For heavy reserve forces, the key factor is cross-country mobility or road networks. For light forces, the key factor is the road network if trucks are available, or the availability of pickup zones (PZs) for air assault forces. The commander prioritizes the positioning of his reserve to reinforce the success of the decisive operation first, then to counter the worst-case enemy counterattack.
5-11. The commander resources his sustaining operations to support the attacking force. A battalion commander organizes his combat service support and other logistics assets into combat and field trains. Higher echelon commanders appoint someone to control sustaining operations within their echelon rear areas. In an attack, the commander tries to position his CSS units well forward. From these forward locations they can sustain the attacking force, providing priority of support to the units conducting the decisive operation. As the attacking force advances, CSS units displace forward as required to shorten the supply lines, using different displacement techniques to ensure uninterrupted support to maneuver units. The size of the force a commander devotes to rear area security depends on the threat in the attacking force's rear area. A significant enemy threat requires the commander to resource a tactical combat force. (Chapter 12 addresses area security operations in more detail.)
5-12. Units conducting offensive operations are assigned an AO within which to operate. Within the AO the commander normally designates the following control measures regardless of whether he operates in a contiguous or noncontiguous environment:
Areas of operations for subordinate units of battalion size or larger.
Phase line as the line of departure (LD), which may also be the line of contact (LC).
Time to initiate the operation.
Objective.
If necessary, a commander can use either an axis of advance or a direction of attack to further control his maneuver forces. (Figure 5-1 depicts the minimum control measures for an attack.)
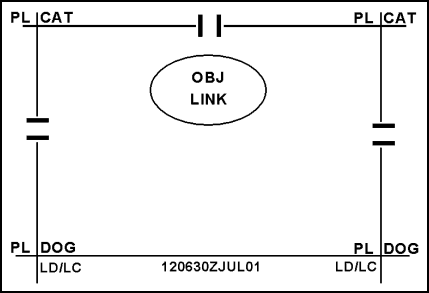
Figure 5-1. Minimum Attack Control Measures
5-13. A commander can use any other control measures necessary to control his attack. Short of the LD/LC, the commander may designate assembly areas and attack positions where the unit prepares for offensive operations or waits for the establishment of the required conditions to initiate the attack. Beyond the LD/LC he may designate checkpoints, phase lines (PLs), probable line of deployment (PLD), assault positions, and direct and indirect fire support coordinating measures. Between the PLD and the objective he can use a final coordination line (FCL), assault positions, support-by-fire and attack-by-fire positions, and time of assault to further control the final stage of the attack. Beyond the objective he can impose a limit of advance (LOA) if he does not want the unit to conduct an exploitation or a pursuit. (Chapters 2 and 3 discuss these control measures. They describe how a commander can use attack positions, axis of advance, combat formations, direction of attack, limit of advance, a LD, objectives, PLD, and a time of attack to help control the operation. Chapter 3 describes the use of AOs, assembly areas, line of contact, phase lines, and common direct and indirect fire coordinating measures.)
5-14. In an attack during limited-visibility conditions, the commander wants positive control over the movement of all attacking elements. He typically imposes additional control measures beyond those he would use in a daylight attack. These additional measures may include using a point of departure (PD) and a direction of attack.
5-15. In an attack, friendly forces seek to place the enemy in a position where he can easily be defeated or destroyed. The commander seeks to keep the enemy off-balance while continually reducing the enemy's options. In an attack the commander focuses the maneuver effects, supported by the other battlefield operating systems (BOS), on those enemy forces that prevent him from accomplishing his mission and seizing his objective. Planning helps a commander synchronize the effects of his combat power through the military decision making process outlined in FM 5-0 and troop leading procedures outlined in FM 6-0.
5-16. This section addresses those considerations unique to an attack by BOS. There are no unique air defense, mobility/countermobility/survivability, or CSS BOS planning considerations that apply only to the attack. Those BOS planning considerations discussed in Chapter 3 continue to apply.
5-17. Fire superiority is that degree of dominance in the fires of one force over another that permits that force to conduct maneuver at a given time and place without prohibitive interference by the enemy. The commander plans to focus the effects of friendly systems to achieve fire superiority and allow friendly maneuver forces to breach the enemy's defensive network. The force must gain and maintain fire superiority at critical points during the attack. Having fire superiority allows the commander to maneuver his forces without prohibitive losses. The commander gains fire superiority by using a variety of tactics, techniques, and procedures. This includes using counterfires and precision fires, suppressing enemy positions, and destroying key facilities and assets. Achieving fire superiority requires the commander to take advantage of—
The range and lethality of available weapon systems.
Offensive information operations to prevent the enemy commander from synchronizing the effects of his available combat power.
Movement to place the enemy in a position of disadvantage where his weapons can be destroyed, one or more at a time, with little risk to friendly weapon systems.
5-18. To employ the proper capabilities and tactics, the commander must have detailed knowledge of the enemy's organization, equipment, and tactics. He must understand the enemy's strengths and weaknesses. Ideally, this knowledge is available during the military decision making process. The commander and his staff develop enemy situational and weapons templates based on analysis of all available combat information and intelligence data. These templates help to determine the feasibility of available courses of action (COAs) designed to achieve a position of advantage.
5-19. Before the attack a unit conducts ISR operations to ascertain those information requirements addressed in paragraph 3-111. Other ISR requirements can include—
The location and depth of enemy reserves.
The location and extent of contaminated areas.
The location and extent of obstacles, possible breach sites, and enemy engagement areas.
The location of areas where attacking units could become disoriented, such as rough or restrictive terrain.
The most favorable routes of approach to the attack objective.
Areas that the attacker can use for flanking fire and maneuver, such as support-by-fire and attack-by-fire positions.
Suitability of planned friendly assault, support, artillery, and CSS positions.
Enemy deception operations.
Commanders and leaders at all echelons personally participate in this process.
5-20. The commander takes every opportunity to gain and refine combat information regarding the enemy. He uses his available ISR assets to gather combat information and process it into intelligence. Information gathered during the planning phase of the plan, prepare, and execute cycle is especially useful in determining the viability of each COA developed. Generally, if a commander does not have good intelligence and, therefore, does not know where the overwhelming majority of the enemy's units and systems are located, he cannot conduct a deliberate attack. He must conduct a movement to contact, conduct a hasty attack, or collect more combat information.
5-21. The two fundamental employment techniques for reconnaissance in the attack are: reconnaissance-pull and reconnaissance-push. In reconnaissance-pull, the reconnaissance objective is to find weaknesses in enemy dispositions that can be exploited by the main force. Reconnaissance is launched over a broad area that allows the reconnaissance elements to identify enemy weaknesses to exploit and enemy strengths to avoid. Once these are identified, the commander exploits the situation by choosing a COA that allows his decisive operation to attack enemy weaknesses and penetrate gaps in the enemy's defense. The commander can then commit forces to widen the gap and envelop the enemy. The reconnaissance elements continue to move, seeking paths of least resistance and pulling the main body deep into the enemy's rear.
5-22. In reconnaissance-push, the reconnaissance objective is to identify the obstacles and enemy forces the attack forces must overcome to assault the objective in a previously chosen location in accordance with a COA selected prior to the reconnaissance. Once friendly reconnaissance elements gain contact with the enemy, they develop the situation within their capabilities. If the objective is an enemy force, the reconnaissance element orients on it to maintain contact and determine as much as possible about its dispositions.
5-23. The commander ensures that reconnaissance and surveillance of the enemy's defensive positions and any terrain critical to the scheme of maneuver continue throughout the attack. If the enemy attempts to modify his defenses, those actions will be detected. In turn, this allows the commander to adjust his scheme of maneuver as the enemy situation becomes clearer. The commander can use human and technological means, acting separately or in combination, to provide the required degree of reconnaissance and surveillance.
5-24. A commander's organic capability to gain information about the enemy and the AO's environment varies by echelon. At the corps echelon these assets include a military intelligence (MI) brigade, an armored cavalry regiment (ACR), and parts of almost every major subordinate command within the corps. Even a company conducts reconnaissance patrols. (For more information on reconnaissance operations, see FM 3-55.)
5-25. In his plan of attack, the commander seeks to surprise his enemy by choosing an unexpected direction, time, type, or strength for the attack and by exploiting the success of military deception operations. Surprise delays enemy reactions, overloads and confuses enemy C2, induces psychological shock in the enemy, and reduces the coherence of the enemy defense. The commander achieves tactical surprise by attacking in bad weather and over seemingly impassible terrain, conducting feints and demonstrations, maintaining a high tempo, destroying enemy forces, and employing sound operations security (OPSEC). He may plan different attack times for his decisive and shaping operations to mislead the enemy and allow the shifting of supporting fires to successive attacking echelons. However, simultaneous attacks provide a means to maximize the effects of mass in the initial assault. They also prevent the enemy from concentrating his fires against successive attacks.
5-26. In planning the commander and subordinate leaders focus on the routes, formations, and navigational aids they will use to traverse the ground from the LD or PD to the objective. Some terrain locations may require the attacking unit to change its combat formation, direction of movement, or movement technique when it reaches those locations. The unit can post guides at these critical locations to ensure maintaining control over the movement.
5-27. The commander attacks targets throughout the depth of the enemy's defense to keep him off balance and limit his freedom of action. However, at the point of the decisive operation, the commander wants to concentrate the effects of overwhelming combat power against the enemy to shatter the cohesion of his defense. The commander accomplishes this by applying combat power against the enemy at a level of violence and in a manner that he cannot match. For example, the commander could concentrate a tank-heavy battalion task force's shock action and firepower against one enemy rifle platoon's hastily prepared defensive position. (Field Manual 3-0 discusses symmetric and asymmetric attack in more detail.)
5-28. Another aspect of concentration is the ability to rapidly concentrate force effects such as fires and offensive information operations during movement. This is especially critical when crossing linear obstacles. Each subordinate element tends to move out independently when it completes passage through a choke point. This independent movement detracts from the ability of the whole force to rapidly generate combat power on the far side of the obstacle.
5-29. Daylight attacks allow friendly forces to effectively use their equipment while facilitating command and control (C2). They are the least stressful psychologically and physically on the attacking units. One major disadvantage is that the enemy can effectively use his systems to oppose the attack. Another disadvantage is that it does not take advantage of the Army's superior thermal viewer capabilities.
5-30. The factors of METT-TC normally require an attack conducted during limited visibility to be more deliberate in nature, except when it occurs as part of the follow-up to a daylight attack or as part of an exploitation or pursuit operation. The commander planning a night attack considers how limited visibility complicates controlling units, soldiers, and fires; identifying and engaging targets; navigating and moving without detection; locating, treating, and evacuating casualties; and locating and bypassing or breaching obstacles.
5-31. Commanders attack in limited-visibility conditions to take advantage of American night-vision and navigational superiority against most potential enemy ground forces. Intensively trained forces equipped for such combat have significant advantages over an enemy who is unprepared for limited-visibility combat. When the friendly force's limited-visibility operations capabilities are significantly greater than the enemy's, limited-visibility attacks may be the norm. Table 5-1 outlines the advantages and disadvantages of conducting limited-visibility attacks.
| ADVANTAGES OF LIMITED-VISIBILITY ATTACKS | DISADVANTAGES OF LIMITED-VISIBILITY ATTACKS |
|
|
5-32. Highly trained units equipped with modern night-vision devices conduct limited-visibility attacks in a manner similar to the way they conduct daylight attacks. Units without extensive night-vision devices can use the darkness to their advantage to conceal their movement, allowing them to get as close to the enemy positions as possible if the enemy also does not have extensive night-vision capabilities. Troops that are well trained for limited-visibility operations and take full advantage of the superiority of their night-vision equipment gain significant tactical and psychological advantages when attacking the enemy at night or in other conditions of reduced visibility. The commander should understand the different night-vision capabilities of all elements participating in the attack, to include the enemy's night-vision capabilities, and make any adjustments necessary to his plan based on these differences. The commander should take advantage of his superior night-fighting capabilities whenever possible.
5-33. The basic organization of forces for a limited-visibility or night attack is the same as for any other attack. However, changing an existing task organization under limited-visibility conditions requires much more time and effort than it does during daylight. Small tactical organizations, such as combat crews and infantry squads, should be resourced as close as possible to full strength even if it means reducing the total number of these small tactical groups.
5-34. The presence or lack of illumination characterizes the conduct of limited-visibility attacks. Nonilluminated attacks offer the best chance of gaining surprise. Illumination, however, is normally planned for every limited-visibility attack so that it can be readily available if required. The commander can choose to conduct a nonilluminated attack until his forces make contact with the enemy. At that point, he can illuminate the objective. The enemy can also choose to employ illumination to increase the effectiveness of his defensive efforts. Units generally conduct nonilluminated attacks although they always plan for illumination. All leaders within the attacking unit must understand the time, conditions, and authority required to employ illumination.
5-35. Illuminated, supported attacks are almost like daylight attacks. They are most effective when speed is essential, time for reconnaissance is limited, or the enemy is weak and disorganized. If the commander employs illumination, it should continue until the force secures the objective. The commander should place the illumination beyond the objective to silhouette objects on the objective. This helps the assaulting force see and fire at withdrawing or counterattacking enemy forces. The commander may also employ illumination in several locations to confuse the enemy about the exact place of attack.
5-36. The commander plans for limited-visibility operations in the same manner that he does for daylight operations, with emphasis on—
Keeping the plan simple.
Taking additional time for reconnaissance.
Taking advantage of easily identifiable terrain features, such as roads and railroad tracks, when establishing control measures.
Using intermediate objectives as necessary to control and maintain the correct movement direction during the attack.
Concealing preparations.
Scheduling initial rehearsals during daylight, with the final rehearsal at night.
5-37. To simplify control problems, the commander may weight his support element over the assault force to reduce the number of friendly soldiers moving on the objective in the darkness. Developing a plan that does not require the unit to change its movement azimuth after it crosses the LD/PD helps to simplify the plan execution.
5-38. The commander must assume that the enemy possesses, in at least limited quantities, the same limited-visibility observation capabilities as his own forces-absent positive information to the contrary-when conducting a limited-visibility attack. Using terrain to mask movement and deployment remains critical because limited visibility may create a false sense of protection from enemy observation. During movement, leaders reduce the distances between vehicles or individual soldiers as necessary to allow one system or soldier to observe the other. This decreases the time necessary to react to enemy contact. The attacking force wants to maintain its momentum; therefore, it does not preserve the alignment of units within the selected combat formation at the expense of additional time. However, it must adhere more closely to the plan of attack than under daylight conditions.
5-39. The planning process synchronizes the unit's maneuver with the provision of fire support. It must identify critical times and places where the commander needs the maximum effects from his fire-support assets. The commander combines his maneuver with fires to mass effects, achieve surprise, destroy enemy forces, and obtain decisive results. His guidance gives specified attack criteria for fire support assets, thus focusing the planning and execution efforts on those critical times and events. The specified attack criteria are a compilation of the commander's guidance, desired effects, and high-payoff targets and attack priorities. The amount of time available to plan the operation constrains the commander's ability to synchronize fire-support operations that employ well-matched effects of all available assets against high-payoff targets.
5-40. The goal of the commander's attack criteria is to focus fires on seizing the initiative. The commander emphasizes simple and rapidly integrated fire support plans. This is done using quick-fire planning techniques and good standing operating procedures (SOPs). The commander integrates his fire support assets as far forward as possible in the movement formation to facilitate early emplacement. Fires concentrate (mass) on forward enemy elements to enable maneuver efforts to close with the enemy positions. Fire support isolates forward enemy elements by using long-range fires, air support, and electronic warfare.
5-41. Fires facilitate his unit's maneuver by destroying or neutralizing strong enemy forces and positions. His fire support system must take full advantage of available preparation time to achieve these demanding effects criteria. Fire-support plans feature the following characteristics:
Targets that are confirmed or denied by ISR efforts.
Designation of target sensor-to-shooter communication links.
Possible use of preparation and deception fires to shape the enemy's defense.
Air support to destroy high-payoff targets on the objective and then shift to reinforcing enemy units, artillery assets, and C2 nodes.
Proactive suppression of enemy air-defense effort.
Preparation fires that shift just as the maneuver force arrives on the objective.
Suppression and obscuration fire plan to support breaching operations.
Pre-positioned ammunition backed by prepackaged munitions stocks capable of rapid delivery.
Integration of nonlethal fires, such as electronic attack and PSYOPS, into the attack guidance matrix.
Integration of primary and backup observers to engage high-priority targets.
Fire support coordinating measures, accounting for danger close and other technical constraints, to allow maneuver forces to get as close as possible to the objective before lifting fires.
Signals for lifting and shifting fires on the objective, primarily by combat net radio and by visual signals as a backup means.
These later fire support coordinating measures should also facilitate the massing of fires, including CAS, against high-payoff targets throughout the AO.
5-42. The commander states the desired effect of fires on the enemy weapon systems, such as suppression or destruction, as part of his planning process. He assigns subordinate units their missions and imposes those control measures necessary to synchronize and maintain control over the operation.
5-43. Using the enemy situational and weapons templates previously developed, the commander determines his probable line of contact and enemy trigger lines. As he arrays his subordinate elements to shape the battlefield, he matches his weapon systems against the enemy's to determine his PLD. Once he determines his PLD, he establishes how long it takes him to move from the LD to the PLD and any support-by-fire positions the attack requires. He establishes when and where his force must maneuver into enemy direct-fire range.
5-44. In addition to accomplishing the mission, every attack plan must contain provisions for exploiting success or any advantages that may arise during the operation. The commander exploits success by aggressively executing the plan, promoting subordinate leader initiative, and using units that can rapidly execute battle drills.
5-45. Even in fluid situations, attacks are best organized and coordinated in assembly areas. If the commander decides that rapid action is essential to retain a tactical advantage, he may opt not to use an assembly area. Detailed advance planning-combined with digital communications, SOP, and battle drills-may reduce negative impacts of such a decision.
5-46. Unless already in an assembly area, the attacking unit moves into one during the preparation phase. The unit moves with as much secrecy as possible, normally at night and along routes that prevent or degrade the enemy's capabilities to visually observe or otherwise detect the movement. It avoids congesting its assembly area and occupies it for the minimum possible time. While in the assembly area, each unit provides its own local ground security and air defense.
5-47. Units moving to assembly areas send out their quartering parties and link up with their guides at the designated locations. While subordinate units move to and occupy assembly areas, the commander completes the process of planning and coordinating the attack.
5-48. The attacking unit should continue its troop leading procedures and priorities of work to the extent the situation and mission allow prior to moving to attack positions. These preparations include but are not necessarily limited to—
Protecting the force.
Conducting task organization.
Performing reconnaissance.
Refining the plan.
Briefing the troops.
Conducting rehearsals, to include test firing of weapons.
Moving logistics support forward.
Promoting adequate rest for both leaders and soldiers.
Positioning the force for subsequent action.
As part of troop leading procedures, leaders at all levels should conduct a personal reconnaissance of the actual terrain. If a limited-visibility attack is planned, they should also reconnoiter the terrain at night.
5-49. A thorough reconnaissance of the objective, its foreground, and other enemy positions is a critical part of attack preparations. The commander exploits all available ISR assets to provide the necessary information. This includes requesting JSTARS feeds of enemy movements from higher echelons or imagery of enemy obstacles. Reconnaissance forces infiltrate through the enemy security area to conduct an area reconnaissance. They can employ precision munitions and conventional indirect fires to destroy detected enemy outposts while remaining undetected. They locate and attempt to infiltrate the enemy's main defensive positions to confirm his dispositions. When properly task-organized, forces conducting reconnaissance may also be given a mission to conduct covert breaches in the enemy's obstacle complexes to facilitate rapid movement of the decisive or shaping operation.
5-50. During this phase, the commander positions his artillery target-acquisition radars to provide support throughout the AO. Divisions and corps establish quick-fire channels between sensors, such as counterbattery radars and firing units, to rapidly silence enemy indirect fire systems. These channels do not change command relationships or priority of fires.
5-51. The commander exercises and refines his maneuver and fire plans during rehearsals which are an important part of ensuring the plan's coordination and synchronization. As part of the rehearsal process, the commander and his subordinates review the anticipated battle sequence to ensure all units understand the plan, the relationship between fire and movement, and the synchronization of critical events. These critical events include:
Moving from the assembly area to the line of departure.
Maneuvering from the line of departure to the probable line of deployment.
Occupying support-by-fire positions.
Conducting the breach.
Assaulting the objective.
Consolidating on the objective.
Exploiting success or pursuing a withdrawing enemy.
Actions of echelon reserves.
The unit should conduct rehearsals under as many types of adverse conditions as possible with time and other restraints to identify and prepare the unit to cope with problems. At lower tactical echelons, the rehearsal includes battle drills, such as creating lanes through minefields.
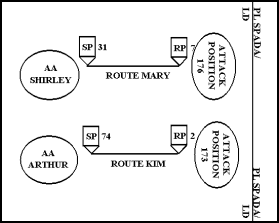 |
5-52. From their assembly areas, attacking units move to their respective LDs. (See Figure 5-2.) Units move from assembly areas to the LD in the same way as for any other tactical movement. (Chapter 13 details troop movements.) The number of columns a unit employs in its movement depends on the availability of suitable routes and the friendly and enemy situation. Primarily the tactical situation and the order in which the commander wants his subordinate units to arrive at their attack positions govern the march formation. Using an LD facilitates the simultaneous initiation of the attack at the prescribed time by all attacking units.
5-53. Light infantry units should move by tactical vehicles to the maximum extent possible to avoid prematurely exhausting their soldiers. However, light infantry forces should not travel too far forward in tactical vehicles. The enemy can detect the noise and other battlefield signatures associated with using tactical vehicles at a greater distance than he can detect dismounted infantry soldiers, and will probably respond to the presence of tactical vehicles with direct- and indirect-fire systems. The commander must weigh the need for security against the time required to conduct a foot march and its resulting effects on soldiers.
5-54. Units move rapidly through their attack positions and across the LD, which should be controlled by friendly forces. A unit uses its designated attack position only by exception, such as when it must refuel prior to crossing the LD to ensure sufficient fuel to reach the objective or the conditions required to ensure the success of the planned maneuver are not yet established. A unit does not occupy its attack positions for more than 10 to 15 minutes without initiating actions to protect itself and increase its survivability, such as deploying local security and camouflage nets and starting the construction of fighting and survivability positions. If necessary, a unit can use guides to assist in occupying the attack position. These guides may come from organic resources or from another unit.
5-55. For units attacking on foot using infiltration and stealth, a commander may designate a point of departure for the attacking units instead of an LD. Armor and mechanized infantry units normally use gaps or lanes through the friendly positions to allow them to deploy into combat formations before they cross the LD.
5-56. Preliminary operations for an attack may include using preparatory fires and the relief of units in contact by executing a relief in place or a forward passage of lines. The relief of units may be desirable to continue the momentum of the attack with fresh troops, change the direction of the attack, exploit a weakness in the enemy position with reserve forces, or initiate an offensive on a stabilized front. (Chapter 14 details a relief in place. Chapter 15 details a forward passage of lines.)
5-57. The commander uses available artillery, mortar, CAS, and offensive information operations to conduct preparatory fires. Preparatory fires are developed from the top down, with bottom-up refinement. The subordinate commander most affected by the effects of these preparatory fires must strongly emphasize the bottom-up refinement process. Preparatory fires can accomplish the following functions:
Destroy the enemy.
Suppress, neutralize, or disrupt high-value or high-priority targets.
Gain fire superiority.
Suppress the enemy in his defensive positions.
Facilitate the attacking force's maneuver.
Deceive the enemy.
5-58. If the attacking forces are in contact with the enemy's security zone, preparatory fires may initially destroy or disrupt only the enemy's reconnaissance and security forces and positions. In either case, counterfires and counterbattery fires conducted as part of preparatory fires serve to degrade the enemy's fire-support systems and assist in achieving fire superiority.
5-59. The commander ensures that his maneuver forces have the CS and CSS assets necessary to conduct the operation and continue the momentum of the attack as part of the preparation process. That support effort must anticipate future maneuvers to ensure the uninterrupted sustainment of the maneuver force.
5-60. A series of advances and assaults by attacking units until they secure the final objective characterizes the attack. Commanders at all levels must use their initiative to rapidly shift their main effort between units as necessary to take advantage of opportunities and momentum to ensure the enemy's rapid destruction. Attacking units move as quickly as possible, following reconnaissance elements or successful probes through gaps in the enemy's defenses. They shift their strength to reinforce success and carry the battle deep into the enemy's rear. A commander does not delay his attack to preserve the alignment of subordinate units or to adhere closely to the preconceived plan of attack. This manual discusses executing the attack in a five-step sequence:
Gain and maintain enemy contact.
Disrupt the enemy.
Fix the enemy.
Maneuver.
Follow through.
This sequence is for discussion purposes only and is not the only way of conducting an attack. The reader should understand that these sequences overlap during the conduct of an attack.
5-61. The commander must avoid becoming so committed to the initial plan that he neglects opportunities. He is prepared to abandon failed attacks and to exploit any unanticipated successes or enemy errors by designating another unit to conduct his decisive operation in response to the changing situation.
5-62. When maneuvering his force, the commander strives to retain freedom of action while protecting his force. Although he may have a detailed plan to defeat the enemy, the commander continually seeks any opportunity to attack to defeat, destroy, or reduce the enemy's combat power or shatter his cohesion and will to fight. The commander avoids dogged adherence to a plan no longer appropriate to current battlefield conditions. The difference between success and failure in combat often depends on the commander's ability to make the plan fit existing circumstances rather than trying to make circumstances fit the plan.
5-63. Gaining and maintaining contact with the enemy when he is deter-mined to break that contact is vital to the success of offensive operations. A defending enemy generally establishes a security area around his forces to make early contact with the attacking forces to determine their capabilities, intent, and chosen COA and to delay their approach. The enemy commander wants to use his security area to strip away friendly reconnaissance forces and hide his dispositions, capabilities, and intent. His goal is to compel the attacking force to conduct a movement to contact against his forces that know the exact location of the attacking forces.
5-64. A commander employs his combat power to overwhelm enemy forces in accordance with his situational understanding. However echelons below division do not normally have the detection, tracking, and weapon systems necessary to conduct decisive or shaping operations directed against enemy forces not currently committed to close combat. The manner in which a unit gains and maintains contact depends on whether the unit is in contact with the enemy's security area or the enemy's main line of resistance and the echelon of the unit in the nested layers of reconnaissance and security. For example, the intent of the corps' reconnaissance effort is to determine the dispositions, composition, direction of movement, and rate of movement of the enemy's significant forces. The corps' armored cavalry regiment, acting as a covering force or advance guard, can fight through a security area, develop the situation, confirm information provided by technical means, and force the enemy to reveal more information than could be acquired solely through using intelligence sensors. This additional information includes locating the enemy's reserve. At a lower level, a battalion constituting the advance guard of the main body can use its scout platoon to conduct a zone reconnaissance that focuses on acquiring updates of enemy positions and obstacles.
5-65. The commander's ability to sense the enemy's actions by gaining and maintaining contact with all significant parts of the enemy force, to include tracking enemy reserves, fire support, and follow-on forces, increases the security of the attacking force. The enemy's attempts to shift major elements of his forces or launch a counterattack will be detected. Additionally, by sending out a force to conduct area reconnaissance with an on-order mission to be prepared to conduct a security mission, the commander can prevent enemy reconnaissance assets from detecting the friendly force's major movements and increase the enemy's risk. The risks to the enemy force increase to the extent friendly forces impede or deny success to enemy ISR assets. Combining these factors results in providing the attacking commander with additional time to take advantage of the changing situation. Moving within the enemy's decision cycle allows the commander to take advantage of his successes by transitioning to the exploitation and pursuit to complete the destruction of the enemy.
5-66. The capabilities of digital C2 systems offer additional techniques a commander can use to gain and maintain enemy contact. The improved common operational picture provided by those systems enhances his situational understanding and ensures rapid, clear communication of orders and intent, thereby reducing the confusion, fog, and friction of battle. Advanced Army and joint intelligence systems feeding those C2 systems enable him to detect and track enemy forces throughout a given AO without having his forces make physical contact with the enemy. The commander's ability to see and understand the situation before the enemy can allows him to act first and maneuver out of contact with the enemy at a high tempo. This allows him to position his forces where they can overwhelm selected elements of the enemy force to disrupt and destroy the enemy's combined arms team. Such attacks-delivered simultaneously with precision by air, ground, and naval systems throughout the width, height, and depth of the battlefield-stun the enemy and rapidly lead to his defeat.
5-67. Disrupting one or more parts of the enemy's combined arms team weakens his entire force and allows the friendly commander to attack the remaining enemy force in an asymmetrical manner. The assessment and decisions regarding what to disrupt, when to disrupt, and to what end are critical. For example, the goal of disrupting the enemy's fire-support system is to allow friendly forces to maneuver and mass the effects of their weapon systems against the enemy without being engaged by the enemy's indirect-fire weapons. Attacking forces can accomplish this by attacking enemy forward observers, fire-direction centers, command posts, artillery and rocket systems, or their ammunition supply. Each set of targets requires a different amount of resources. The probability of success, the effectiveness of the attack, and the time necessary to achieve the desired target effects varies with each set of targets.
5-68. Once any type of contact-even sensor contact-is made with the enemy, the commander wants to use the element of surprise to conduct shaping operations that strike at the enemy and disrupt both the enemy's combined arms team and his ability to plan and control his forces. Once this disruption process begins, it continues throughout the attack. The commander uses any existing technological advantage over the enemy in the following areas to aid the disruption process:
Offensive information operations.
Lethal firepower effects.
Range of direct-fire weapons.
Protection.
Battlefield mobility.
Information management.
C2 systems.
5-69. Whatever form of disruption takes place helps the commander seize, retain, and exploit the initiative; maintain his freedom of action; impose his will on the enemy; set the terms, and select the place for battle. That disruption also allows the commander to exploit enemy vulnerabilities and react to changing situations and unexpected developments more rapidly than the enemy. This disruption effort usually occurs at division level and above because lower echelons lack the necessary reconnaissance, target acquisition, intelligence analysis, and target attack assets to engage forces not committed to close combat.
5-70. The commander plans his shaping operations to occur at the place and time necessary to establish the conditions for his decisive operation. Targets of a shaping operation may include: enemy C2 facilities, ISR assets, fire-support systems, reserves, and logistics support. If a commander executes a shaping operation too early, the enemy has time to recover and respond before friendly forces conducting the decisive operation can complete their maneuver.
5-71. The commander plans to use harassment, suppressive, or interdiction fires against positions likely to contain high-payoff targets to disrupt enemy reactions to the attacking unit's advance. These fires deny the enemy unrestricted use of the terrain and can prevent his reserves from entering the fight before the unit seizes the objective. Additional benefits may result from these fires over time, including increased psychological pressure on enemy forces and a reduction in their mental and physical capabilities by disrupting their sleep and rest patterns.
5-72. Surprise denies the enemy the opportunity to focus and synchronize his combat power against the attacking force. It prevents the enemy from massing his forces or fires at a critical, possibly decisive, place and time. In place of cohesive resistance, surprise can produce confusion, fear, and piecemeal resistance. Factors that contribute to surprise include: the tempo and intensity in executing the attack plan and employing unexpected factors, such as selecting a less than optimal COA, varying operational tactics and methods, conducting deception operations, and ensuring OPSEC.
5-73. A primary purpose in fixing the enemy is to isolate the objective of the force conducting the echelon's decisive operation to prevent the enemy from maneuvering to reinforce the unit targeted for destruction. Since war is a contest between thinking opponents, the enemy will oppose the friendly commander's attempts to fix his forces. Every friendly move causes the enemy to attempt to counter that move. The commander does everything in his power to limit the options available to his opponent. Fixing an enemy into a given position or a COA and controlling his movements limit his options and reduce the amount of uncertainty on the battlefield.
5-74. Reducing uncertainty allows the friendly force to use maneuver to mass the effects of overwhelming combat power against a portion of the enemy. It gives the commander more time to modify his plan as necessary and orchestrate the employment of his forces. It allows him to mass forces in one place by using economy of force measures in other areas. The commander may also try to fix an enemy unit, such as the enemy reserve or follow-on force, to prevent it from repositioning or maneuvering against the force conducting his decisive operation.
5-75. Fixing the enemy must be done with the minimum amount of force. The commander normally allocates the bulk of his combat power to the force conducting his decisive operation, so fixing operations are, by necessity, shaping operations that illustrate economy of force as a principle of war. Therefore, the commander must carefully consider which enemy elements to fix and target only those that can significantly affect the outcome of the fight. The longer the requirement to fix these forces, the more resources the commander needs to accomplish the mission. Generally, an enemy force only needs to be fixed until it cannot respond to the actions of the unit conducting the decisive operation in time to affect the outcome. This may require a commander to slow down the rate of march of an enemy unit to prevent it from influencing the outcome of the engagement or battle.
5-76. One method of isolating the objective is to conduct a shaping operation using lethal and nonlethal fires. Lethal fires may range from sniper fire to a joint fire plan designed to totally destroy a selected portion of the enemy force. Nonlethal fires, such as electronic jamming, can prevent the enemy from receiving orders or vital intelligence and combat information.
5-77. Severing enemy lines of communication over prolonged periods of time by using interdiction measures is another way to fix the enemy. These measures can range from air interdiction that destroys bridges and rail switching yards to ambushes conducted by infiltrating combat patrols.
5-78. Another method of fixing the enemy is to tie obstacles into the existing terrain to canalize and slow the movement of enemy reserves. At lower tactical echelons, scatterable minefields employed in accordance with the rules of engagement can seal the objectives from possible enemy reinforcement or counterattacks and neutralize enemy actions to the flanks. Deception operations and activities, such as demonstrations and false preparatory fires, can fix the enemy. Using extensive smoke screens and vehicle mock-ups in a deception effort can also assist in fixing an enemy force.
5-79. The commander maneuvers his forces to gain positional advantage so he can seize, retain, and exploit the initiative. He avoids the enemy's defensive strength. He employs tactics that defeat the enemy by attacking through a point of relative weakness, such as a flank or the rear.
5-80. Offensive maneuver seeks to achieve a decisive massing of effects at the decisive point, or at several decisive points if adequate combat power is available. The commander exploits maneuver by—
Taking maximum advantage of dead space and covered and concealed routes to close with the enemy.
Using his advantages in the effective ranges of weapon systems.
Repositioning friendly forces rapidly.
Navigating accurately cross-country.
Obtaining situational understanding of friendly and enemy locations.
Taking effective security measures.
Synchronizing the application of all BOS at a time and place on the battlefield to maximize their effects.
5-81. The key to success is to strike hard and fast, overwhelm a portion of the enemy force, and then quickly transition to the next objective or phase, thus maintaining the momentum of the attack without reducing the pressure. The commander must retain freedom of maneuver with multiple COAs throughout the operation and responsive CSS. Additionally, he must make every effort to locate and track enemy reserve and follow-on forces, which prevents friendly forces from being attacked unexpectedly by significant enemy forces. This allows the commander time to delay, disrupt, or destroy these enemy forces before they can interfere with the attack.
5-82. Depending on the conditions of METT-TC, artillery and mortars may advance with the attacking formation or move forward by bounds. The echelon fire support coordinators (FSCOORDs) position direct support and reinforcing artillery in coordination with their maneuver commanders. The force field artillery headquarters, normally a division or corps artillery headquarters, coordinates position areas for general support and general support-reinforcing artillery units through the fire support officers at corps, division, and brigade. The commander considers the maneuver of fire support assets along with maneuver forces to ensure that proper fire support is available at all times.
5-83. The maneuver process normally follows this sequence:
Movement from the LD to the PLD.
Actions at the PLD, assault position, or FCL.
Breaching operations (discussed in FM 3-34.2).
Actions on the objective.
The movement from the assembly area to the LD that precedes many attacks is troop movement and is discussed in Chapter 13.
5-84. The unit transitions from troop movement to maneuver once it crosses the LD. It moves aggressively and as quickly as the terrain and enemy situation allow. It moves forward using appropriate movement techniques assisted by the fires of supporting units. Fire and movement are closely integrated and coordinated. Effective suppressive fires facilitate movement, and movement facilitates more effective fires. Whenever possible, the attacking unit uses avenues of approach that avoid strong enemy defensive positions, takes advantage of all available cover and concealment, and places the unit on the flanks and rear of the defending enemy. Where cover and concealment are not available, the unit uses obscurants to conceal its movement. Any delays in establishing obscuration and suppressive fires prior to crossing the PLD may require the attacking unit to occupy its assault positions.
5-85. Artillery and other fire-support assets move as necessary to ensure that the attacking unit remains within supporting range. Previously conducted analysis of the time it takes the maneuver unit to move from the LD to the PLD and the distances involved ensures that their fire support systems are prepared to provide fire support before maneuver units move inside the effective range of enemy direct-fire weapon systems. The existence of enemy artillery systems that have a longer range than fielded US artillery systems complicates this process. The commander uses fires delivered from fixed- and rotary-wing systems and the autonomous operation capabilities of modernized artillery systems to help counter any enemy range advantage.
5-86. If the commander expects to make enemy contact at or shortly beyond the LD, he deploys his unit so that he can maintain maximum firepower against the enemy's known positions. He chooses the combat formation that best balances firepower, tempo, security, and control in the specific situation. The commander has the option of deploying a security force in front of his attacking unit. He may also employ a flank or rear security force if required by the enemy situation. The commander may not want to change formations during his attack because of the potential loss of momentum resulting from such changes. If the commander finds it necessary to transition from one combat formation to another, he should base the transition on thoroughly trained drills. Once enemy contact is expected, he transitions to the bounding overwatch technique of movement. (Chapter 13 addresses movement techniques.)
5-87. Between the LD and the PLD, the attacking unit secures intermediate objectives only to eliminate enemy positions or bring additional suppressive fires to bear. Fire-support assets engage targets of opportunity. The commander uses CAS and artillery to destroy enemy security forces. As the unit approaches suspected enemy positions or danger areas, the commander directs his forces to occupy predesignated support-by-fire positions. Fire support, suppression, and obscuration are key enablers that allow a force to occupy these positions. Commanders use fires from these positions to suppress enemy forces while the unit continues its advance toward the objective.
5-88. The commander engages known enemy forces with the maximum possible combat power to overwhelm them as quickly as possible. The attacking unit that encounters small enemy units on the way to the objective either quickly overruns or bypasses them if they meet the bypass criteria. The attacking unit then reports the location of bypassed enemy elements to its higher headquarters and maintains contact until they can be handed off to follow and support forces. The commander uses minimal force to maintain that contact to avoid significantly weakening the force conducting his decisive operation.
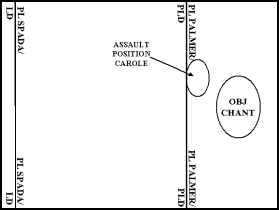 |
5-89. The attacking unit maintains the pace of its advance as it approaches its PLD. (See Figure 5-3.) The attacking unit splits into one or more assault and support forces once it reaches the PLD if not previously completed. At the PLD infantry soldiers dismount from their infantry fighting vehicles as required by the situation. All forces supporting the assault force should be set in their support-by-fire positions before the assault force crosses the PLD. The commander synchronizes the occupation of these support-by-fire positions with the maneuver of the supported attacking unit to limit the vulnerability of the forces occupying these positions. The commander uses his unit's tactical SOP, prearranged signals, engagement areas (EAs), and target reference points (TRPs) to control the direct fires from these supporting positions. He employs restricted fire lines between converging forces.
5-90. The PLD can be co-located with the assault position. (See Figure 5-3.) The commander ensures that the final preparations of his breach force in an assault position do not delay its maneuver to the point of breach as soon as the conditions are set. Whenever possible, the assault force rapidly passes through the assault position. It may have to halt in the assault position while fires are lifted and shifted. In this case, if the enemy anticipates the assault, the assault force deploys into covered positions, screens its positions with smoke, and waits for the order to assault. As long as the assault force remains in the assault position, support forces continue their suppressive fires on the objective.
5-91. Once the support force sets the conditions, the breach force reduces, proofs, and marks the required number of lanes through the enemy's tactical obstacles to support the maneuver of the assault force. The commander must clearly identify the conditions that allow the breach force to proceed to avoid confusion. From the PLD, the assault force maneuvers against or around the enemy to take advantage of the support force's efforts to suppress the targeted enemy positions. The support force employs direct and indirect fires against the selected enemy positions to destroy, suppress, obscure, or neutralize enemy weapons and cover the assault force's movement. The assault force must closely follow these supporting fires to gain ground that offers positional advantage. This COA normally results in the fewest casualties.
5-92. The key to forward movement when the assault force is under enemy direct fire is to return effective fire, which prevents the enemy from firing effectively at the moving assault force. Destructive or suppressive fires are most effective when fired by the stationary support force. These fires prevent the enemy from firing effectively at the moving assault force. Once the support force is in position and the assault force is prepared to move, the support force places a heavy volume of fires on the enemy to destroy, neutralize, or suppress him. The ability of the support force to move to advantageous terrain is critical to accomplishing its purpose of ensuring the assault force's success. Once it suppresses the enemy position, it reduces its rate of fire to sustainable levels to conserve ammunition as the assault force closes on the objective to ensure that it has enough to support the assault. When the assault force nears its objective, the support force increases its rate of fire to ensure the continued suppression of the enemy. This allows the assault force to assault the position before the enemy can react. Either on signal or when the assault begins, the support force ceases fire, shifts its fire to another target area, or walks its fire across the objective in front of the assault force.
5-93. The commander uses smoke to help conceal units and individual weapons. It degrades enemy laser designators, range finders, and directed energy weapons. When planning to employ smoke, the commander remembers that smoke can have the same effects on friendly and enemy forces. If possible during the assault, the commander uses obscuration to blind the enemy and screen friendly movement onto the objective. Obscuration is placed in front of enemy positions, on the far side of obstacles, and in areas that restrict maneuver. The commander may use a smoke haze over rear areas to limit enemy observation. The defeat of enemy thermal viewers requires the use of multispectral smoke.
5-94. The effects of the overwhelming and simultaneous application of fire, movement, and shock action characterize the final assault. This violent assault destroys or drives the enemy from the objective area. Small units conduct the final assault while operating under the control of the appropriate echelon command post. Heavy forces have the option of conducting this final assault in either a mounted or dismounted configuration.
5-95. The commander employs all fire support means to destroy and suppress the enemy and sustain the momentum of the attack. By carefully synchronizing the effects of his indirect-fire systems and available CAS, the commander improves the likelihood of success. He plans fires in series or groups to support maneuver against enemy forces on or near the geographical objective. As the commander shifts artillery fires and obscurants from the objective to other targets, the assault element moves rapidly across the objective. The support element must not allow its suppressive fires to lapse. These fires isolate the objective and prevent the enemy from reinforcing or counterattacking. They also destroy escaping enemy forces and systems. The commander employs offensive information operations, such as electronic warfare, to attack enemy C2 nodes as part of this effort.
5-96. Supporting artillery may need to displace forward during the attack to ensure maximum support is available for the assault. However, changes in position are held to a minimum because they reduce the volume of available fires. The commander balances the need to maintain that amount of fire support against the enemy's counterbattery capabilities with the need to provide continued coverage as the attacking unit continues to move forward. Fire support assets supporting the unit move into their new positions one subordinate unit at a time, by echelon, to maintain fire support to the attack. The commander can use his available CAS to provide supporting fires while his artillery batteries displace.
5-97. Small enemy units moving toward the penetrated area can disrupt the synchronization of this final assault. As small units and weapon systems crews become engaged, they tend to focus on their immediate opponent rather than the overall situation. Loss of situational understanding, combined with the enemy's more detailed knowledge of the terrain, allows small enemy forces to inflict a great deal of damage on the attacking force. The attacking unit's leaders must understand the flow of combat and retain the capability to engage these enemy forces before they can alter the outcome of the assault. The commander can commit his reserve to maintain the attack momentum and keep relentless pressure on the enemy. This action also hinders enemy attempts to stabilize the situation.
5-98. Against a well-prepared, integrated enemy defense, the commander must isolate and destroy portions of the enemy defense in sequence. (See Figures 5-4 and 5-5.) His forces must isolate, suppress, obscure, and bypass selected enemy positions. For example, smoke delivered by field artillery and mortars in front of the objective-between the force and the enemy-screens friendly movement and obscures the enemy's weapon systems. Fires placed on and beyond the flanks of the objective serve to isolate the enemy's position. These fires include: smoke, high explosives, improved conventional munitions, and precision-guided munitions delivered by a mix of field artillery, fixed-wing aviation assets, and attack helicopters. In addition, the commander may employ short-duration scatterable mines in accordance with the rules of engagement in conjunction with terminally guided munitions to help isolate and impair the enemy's ability to counterattack. (Their use must not impede the commander's conduct of exploitation and pursuit operations.) Jamming can be used to cut C2 links between the enemy's maneuver force and its supporting artillery. The commander can also use any available CAS to accomplish the desired effects.
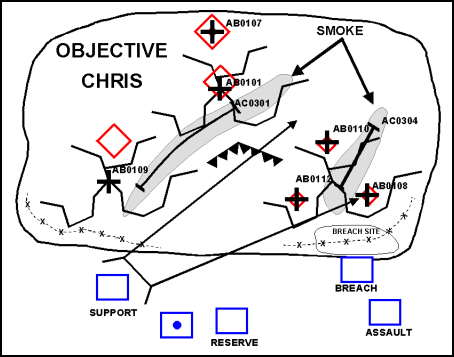
Figure 5-4. Attack of an Objective: The Breach
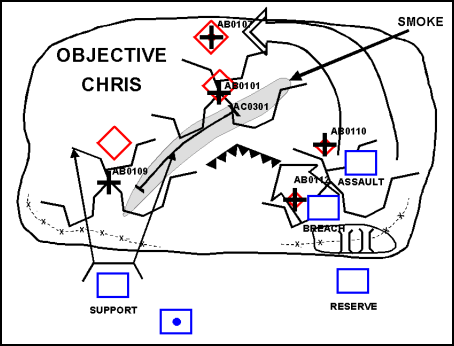
Figure 5-5. Attack of an Objective: The Assault
5-99. The commander generates overwhelming combat power in sequence against isolated centers of resistance. The assault element can task organize itself to assault one portion of the objective at a time. For example, within the assault company of a task force attack, two platoons may suppress while one platoon seizes a portion of the company objective. This initial platoon, having seized a foothold, then suppresses to allow a second platoon to continue the assault. The third platoon may have a third portion of the objective assigned to it to seize in turn. The enemy may attempt to reinforce its defending forces or counterattack during the friendly force's attack. Once the attacking force reaches the far side of the objective, selected elements clear remaining pockets of resistance while the bulk of the assault force prepares for a possible enemy counterattack. After the assault force reaches the objective, the support force leaves its support-by-fire position and rejoins the assault force or moves to a blocking position to counter possible enemy counterattacks.
5-100. Mounted Assault. In determining whether to conduct a mounted or dismounted attack, the commander considers the primary factors of the terrain, obstacles, and the strength of enemy antiarmor defenses. Mounted assaults accelerate the execution of the operation by allowing the greatest speed and shock action and providing the best protection against small arms and indirect fires while conserving the strength of the infantry soldiers conducting the assault.
5-101. When facing weak, hastily prepared, disorganized resistance, or when attacking with overwhelming combat power in relation to enemy forces on the objective, a heavy force commander can conduct a mounted assault. The commander conducting a mounted assault concentrates all of his supporting fires to destroy and neutralize the enemy and fix local reserves. Tanks and infantry fighting vehicles use cannon and machineguns to engage targets for as long as possible, taking advantage of their accuracy, destructiveness, and small bursting radius of their munitions. As the fires from one type of weapon are lifted or shifted, other weapons increase their rate of fire. The assault force advances close to its objective under the cover of these supporting fires.
5-102. The assault force attacks using shock action aided by the firepower of organic systems to rapidly overrun the enemy position as soon as the commander shifts his supporting fires beyond the objective. Mechanized infantry elements move as close as possible to the objective while remaining mounted in their infantry fighting vehicles. When the danger to the mounted infantry elements exceeds the protection offered by their combat vehicle, the commander gives the order for his infantry elements to dismount from their carriers.
5-103. The following technique applies to a heavy force assigned the mission of rapidly clearing an objective against an enemy that does not have a robust antiarmor capability. The heavy force overruns the objective. The accompanying mechanized infantry soldiers dismount from their vehicles on the far side of the objective and sweep the objective from the far side back to the near side to clear any remaining pockets of resistance. The ability of heavy forces to closely follow friendly mortar and artillery fires as they shift across the objective is a major advantage. Any delay in launching the assault after the commander shifts the supporting fires allows the enemy time to move from his protective positions to his firing positions.
5-104. Dismounted Assault. A heavy force commander usually conducts a dismounted assault when any of the following conditions apply:
Terrain favors dismounted operations.
The enemy is in prepared positions.
The enemy has a strong antiarmor capability.
Tanks are not available to lead the assault even though the factors of METT-TC favor their employment.
Obstacles prevent maneuver across the objective.
Stealth is required to close on the objective.
A mounted assault stalls on or short of the objective.
Based on his analysis of the factors of METT-TC and the degree of risk he is willing to accept, the commander determines if, when, and where any mechanized infantry forces in the assault force will dismount from their infantry fighting vehicles.
5-105. Consolidation. Consolidation is the process of organizing and strengthening a newly captured position so that it can be defended. Normally, the attacking unit tries to exploit its success regardless of the type of the assault. In some situations, however, the unit may have to consolidate its gains. Consolidation may vary from a rapid repositioning of forces and security elements on the objective, to a reorganization of the attacking force, to the organization and detailed improvement of the position for defense. Actions taken to consolidate gains include—
Conducting reconnaissance.
Establishing security.
Eliminating enemy pockets of resistance.
Positioning forces to enable them to conduct a hasty defense by blocking possible enemy counterattacks.
Adjusting the fire planning.
Preparing for potential additional missions.
5-106. Immediately after the assault, the commander must maintain contact with those enemy forces that have abandoned the objective. If he has destroyed all enemy forces on the objective, he takes those actions necessary to regain contact with the enemy. The commander sends out patrols in any direction required to maintain or regain contact with the enemy within his AO. Higher echelons reposition their ISR collection assets and adjust their assigned missions as necessary to maintain that contact.
5-107. The commander also dispatches patrols to ensure contact with any adjacent friendly units. A unit is normally responsible for establishing contact with the units to its front and right as defined by the direction to the enemy. Unless a commander knows that units to his left and rear are preparing to make contact, he takes actions to initiate that contact. Otherwise, a dangerous gap could occur, which the enemy could exploit during a counterattack.
5-108. The task of establishing security is accomplished as soon as the force occupies the objective. Each subordinate element establishes observation posts (OPs) that monitor likely enemy avenues of approach and conduct other security operations. Units must remain aware that the enemy will have defensive fires planned on his former positions, including headquarters bunkers and supply caches.
5-109. Once subordinate units seize the objective, they clear it of enemy forces. They then occupy firing positions to prepare for an enemy counterattack. Normally, an attacking unit does not occupy vacated enemy positions because the enemy is familiar with and normally targets them. Therefore, the attacking unit should position itself away from established enemy positions usually on the next defensible piece of terrain. This positioning is also important because the unit needs to orient on different avenues of approach and in a different direction. The commander positions his armored and antitank systems to cover likely enemy mounted avenues of approach. Mechanized infantry forces normally dismount and orient along likely dismounted and mounted infantry avenues of approach. Overwatching forces, such as antitank systems, orient along likely mounted avenues of approach. Mortars, command posts, and CSS assets move forward to assist in the consolidation.
5-110. The commander should preplan the location and future missions of each element. Artillery and other fire support systems mass fires on enemy assembly areas and troops forming for counterattacks. The commander may alert his reserve to protect the flanks of the attacking units, hold ground seized by them, or counter an enemy counterattack. The commander may use antitank minefields or other obstacles to cover likely enemy avenues of approach. As the unit has time and resources, it improves these obstacles and defensive positions.
5-111. The commander normally designates TRPs, final protective fires, engagement areas, and other direct- and indirect-fire control measures as part of the consolidation process. Once in position, subordinate elements modify preplanned measures and improve the its defensive capabilities as required. As local security is being established, the commander directs subordinate elements to conduct mounted or dismounted patrols along likely enemy avenues of approach. The echelon scout or cavalry unit deploys beyond these local security patrols to conduct its assigned reconnaissance or security mission.
5-112. Reorganization. Reorganization includes all measures taken by the commander to maintain the combat effectiveness of his unit or return it to a specified level of combat capability. Commanders of all types of units at each echelon conduct reorganization. Any reorganization actions not completed when conducting the attack are accomplished during consolidation. These actions include—
Redistributing or cross-leveling supplies, ammunition, and equipment as necessary.
Matching operational weapon systems with crews.
Forming composite units by joining two or more attrited units to form a single, mission-capable unit.
Replacing key personnel lost before or during the battle.
Reporting unit location and status to keep the next higher commander informed; digitized units can do this automatically.
Recovering, treating, and evacuating casualties, prisoners of war, and damaged equipment in accordance with its SOP.
Resupply of its basic loads of ammunition, fuel, and repair parts as time permits.
Integrating replacement soldiers and systems into the unit.
Revising communication plans as required. The unit places its C2 facilities in position to conduct further operations and control the consolidation.
Reestablishing unit cohesion.
Conducting essential training, such as training replacements on the unit's SOP.
5-113. After seizing the objective, the commander has two alternatives: exploit success and continue the attack or terminate the offensive operation. At brigade echelon and below, the unit maintains contact and attempts to exploit its success. Normally, a division or corps commander makes the decision regarding whether to initiate a general-as opposed to local-exploitation or pursuit or terminate offensive actions.
5-114. After seizing an objective, the most likely on-order mission is to continue the attack. During consolidation, the commander and his staff continue troop leading procedures in preparation for any on-order missions assigned by a higher headquarters. They use available combat information and intelligence products to adjust contingency plans. The commander redirects his ISR collection effort to support his next mission.
5-115. Fire support assets move quickly to take advantage of the natural reduction in support requirements that occur when a position is taken and when the enemy can organize a counterattack to provide depth to a defense. Field artillery units reposition to where they can support a renewed attack when ammunition supply and enemy action permit. Attacks by rotary- and fixed-wing aircraft can provide support while artillery systems reposition. Road conditions, such as destroyed bridges or dislocated civilians, and the unit's existing cross-country mobility abilities given the current environment conditions will also impact on the exact time of the decision to reposition.
5-116. The commander attempts to exploit the deterioration of the enemy position by administering quick and powerful blows before the enemy can reconstitute his defense. Using mass quantities of precision-guided munitions, combined with the action of large, heavy formations and air support, may prove decisive.
5-117. Ordinarily, the enemy attempts to hold his position until nightfall and complete his withdrawal under cover of darkness. The attacking unit maintains relentless pressure, continuing the attack at night. Through these attacks, the unit maintains contact with the enemy, keeps him off balance, and makes his withdrawal from action extremely difficult. If the enemy tries to delay, the unit continues its attack, concentrating its efforts on enveloping or encircling the retrograding enemy force if the enemy is too strong to overrun. An attack aggressively pushed through the hostile front may isolate major elements and force the enemy to evacuate the entire defensive position before he can construct a viable fall-back position.
5-118. When conducting a successful penetration, attacking units penetrate deeper into the hostile position to attack enemy reserves, artillery, C2 centers, and lines of communication. Either the assault or a support unit attacks the enemy's newly exposed flanks to widen the gap. The commander sends forces through the gap that have a high degree of tactical mobility to exploit the advantages gained, attack the enemy from the rear, and prevent his escape. At this time, the commander's force multipliers-such as fixed-wing aviation-concentrate on supporting the ground force exploiting the penetration.
5-119. As part of the follow through to the attack, the commander plans logical sequels to his attack. Attacking forces plan for exploitation. Exploiting forces plan for the pursuit of a defeated enemy. Furthermore, the commander must use his force without overextending its logistics capabilities. The commander must plan to have fresh units pass around or through forward units to sustain the momentum of the attack. He may assign these fresh units the task of follow and support or follow and assume in an effort to maintain the tempo of the attack. (Appendix B discusses both tactical mission tasks in greater detail.) A commander conducting either type of offensive operation envisions how, under what conditions, where, and when he will need to transition to the defense based on possible enemy countermoves and other events.
5-120. If the attacking unit is transitioning to a pursuit or exploitation, it may have to bypass enemy units to maintain the operational tempo. Units bypass enemy forces according to the previously established bypass criteria. As a minimum, the bypassed force is left under observation or fixed in place by other units.
5-121. If the enemy succeeds in withdrawing his major forces from action, the commander intensifies reconnaissance to obtain the information necessary to decide on a COA. Aggressive action may prevent the enemy from reconstituting his defense in a rearward position. The commander may have to delay the renewal of his attack until completing additional reconnaissance so he can formulate a tactically sound plan if the enemy succeeds in occupying new defensive positions.
5-122. The commander can launch an attack to achieve various results or for special purposes. These subordinate forms of an attack are—
Ambush.
Counterattack.
Demonstration.
Feint.
Raid.
Spoiling attack.
The commander's intent and the factors of METT-TC determine the specific form of attack. As attack forms, they share many of the planning, preparation, and execution considerations of the offense. This section discusses the unique considerations of each form of attack. Demonstrations and feints, while forms of attack, are also associated with military deception operations. (See FM 3-13.)
5-123 An ambush is a form of attack by fire or other destructive means from concealed positions on a moving or temporarily halted enemy (FM 3-0). It may include an assault to close with and destroy the engaged enemy force. In an ambush, ground objectives do not have to be seized and held.
5-124. The two types of ambush are point ambush and area ambush. In a point ambush, a unit deploys to attack a single kill zone. In an area ambush, a unit deploys into two or more related point ambushes. A unit smaller than a platoon does not normally conduct an area ambush.
 |
5-125. Ambushes are categorized as either hasty or deliberate but take place along a continuum. A hasty ambush is an immediate reaction to an unexpected opportunity conducted using SOPs and battle drill. A deliberate ambush is planned as a specific action against a specific target. Detailed information about the target, such as size, organization, and weapons and equipment carried; route and direction of movement; and times the target will reach or pass certain points on its route may be available. Heavy or light forces may conduct an ambush. (Figure 5-6 shows the tactical mission graphic for an ambush.) Doctrine categorizes ambushes as near or far ambushes, based on the proximity of the friendly force to the enemy.
5-126. The typical goal of the ambush force is the death or capture of all enemy personnel located within the kill zone. Another goal could be to destroy certain designated vehicles, such as all missile transporter-erector launchers. Ideally, the ambush force can destroy the ambushed enemy so quickly that he is unable to report the engagement while the ambush force accomplishes its mission.
5-127. A typical ambush is organized into three elements: assault, support, and security. The assault element fires into the kill zone. Its goal is to destroy the enemy force. When used, the assault force attacks into and clears the kill zone and may be assigned additional tasks, to include searching for items of intelligence value, capturing prisoners, and completing the destruction of enemy equipment to preclude its immediate reuse. The support element supports the assault element by firing into and around the kill zone, and it provides the ambush's primary killing power. The support element attempts to destroy the majority of enemy combat power before the assault element moves into the objective or kill zone. The security element isolates the kill zone, provides early warning of the arrival of any enemy relief force, and provides security for the remaining ambush force. It secures the objective rally point and blocks enemy avenues of approach into and out of the ambush site, which prevents the enemy from entering or leaving.
5-128. Planning considerations for an ambush include—
A "no-later-than" time to establish the ambush.
A tentative ambush formation or, for an area ambush, element locations.
Insertion and exit routes.
A forward passage of lines and movement to the ambush site in tactical formation.
Location of a rally point where the ambush force can reassemble and reorganize if required.
Actions if the ambush is prematurely detected.
A scheme of maneuver that maximizes engagement of the enemy's flank or rear, provides early warning of target approach, includes assault element actions in the kill zone, and details how the ambush element displaces from the ambush site.
Actions at the objective,
Obstacles to augment the effects of the friendly fire.
A fire support plan that integrates the direct fire and obstacle plans, which results in the enemy's isolation, inflicts maximum damage, and also supports forces in the rally point.
The criteria for initiating the ambush; for example, only engage enemy formations of the same or smaller size and withhold fire until the target moves into the kill zone.
Any required changes to the ambushing unit's fire distribution SOP, based on the factors of METT-TC.
Rear security measures.
5-129. A point ambush usually employs a line or an L-shaped formation. The names of these formations describe deployment of the support element around the kill zone. The kill zone is that part of an ambush site where fires are concentrated to isolate, fix, and destroy the enemy. The ambush formation is important because it determines whether a point ambush can deliver the heavy volume of fire necessary to isolate and destroy the target. The commander determines the formation to use based on the advantages and disadvantages of each formation in relation to the factors of METT-TC.
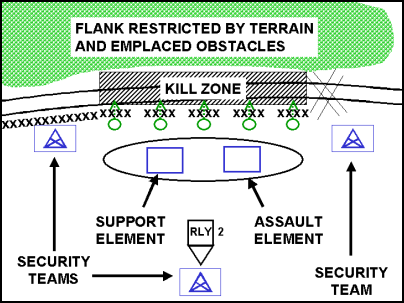 |
5-130. The assault and support elements generally deploy parallel to the target's route of movement-the long axis of the kill zone-which subjects the target to flanking fire in the line formation. (See Figure 5-7.) The size of the target that can be trapped in the kill zone is limited by the size of the area that can be covered by the support element's weapons. Natural, manmade, and military obstacles-reinforced with tactical obstacles integrated with direct and indirect fires-traps the target in the kill zone. A disadvantage of the line formation is that the target may be so dispersed that it is larger than the kill zone.
5-131. The line formation is effective in close terrain, which restricts the target's movement, and in open terrain where one flank is blocked by existing or reinforcing obstacles. The commander may place similar obstacles between the assault and support elements and the kill zone to protect the ambush force from the target's counterambush drills. When the ambush force deploys in a line formation, it leaves access lanes through these protective obstacles so that it can assault the target. An advantage of the line formation is that it is relatively easy to control under all conditions of visibility.
5-132. The L-shaped formation is a variation of the line formation. (See Figure 5-8.) The long leg of the "L" (assault element) is parallel to the kill zone and provides flanking fire. An advantage of the "L" formation is that the short leg (support element) is at the end of the kill zone and at a right angle to it and blocks the enemy's forward movement. It also provides enfilading fire that interlocks with fire from the other leg. The commander can employ an L-shaped formation on a straight stretch of trail, road, stream, or at a sharp bend.
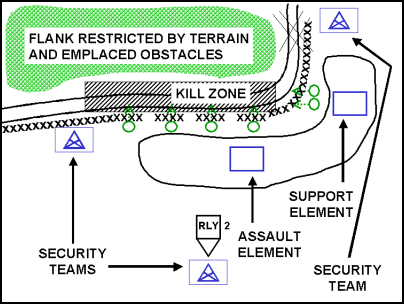
Figure 5-8. L-Shaped Ambush
5-133. An area ambush is most effective when enemy movement is largely restricted to trails or roads. The area should offer several suitable point ambush sites. The commander selects a central ambush site around which he can organize outlying ambushes. Once he selects his site, he must determine the enemy's possible avenues of approach and escape routes. He assigns outlying point ambush sites to his subordinates to cover these avenues. Once they occupy these sites, they report all enemy traffic going toward or away from the central ambush site to the commander. These outlying ambushes allow the enemy to pass through their kill zone until the commander initiates the central ambush. Once the central ambush begins, the outlying ambushes prevent enemy troops from escaping or entering the area. (See Figure 5-9.)
Figure 5-9. Area Ambush
5-134. The ambush unit commander normally specifies the signals required to control the ambush. He changes the meaning of audible and visual signals frequently to avoid setting patterns that the enemy can recognize. Otherwise, the enemy might recognize a signal and react in time to avoid the full effects of the ambush. For example, if a white star cluster is always used to signal withdrawal in a night ambush, an alert enemy might fire one and cause the ambush force to withdraw prematurely. The subordinate elements of the ambush unit must receive communications-in the form of signals-that relay the following information:
Target approaching, normally given by a member of the security team to warn the ambush commander and the ambush elements of the target's progress.
Initiate the ambush, given by the ambush unit commander. (This signal should be a mass casualty-producing signal, such as a main gun round from a tank, machine gun fire, the detonation of mines or explosives, or other direct fire crew-served weapons.)
Lift or shift fire, given when the target is to be assaulted; all fires must stop or be shifted at once so that the assault element can attack before the target can react.
Assault, given when the assault force is to move into the kill zone and complete its activities.
Cease fire, given to cease all fires.
Withdraw from the kill zone or ambush site, given when the ambush is completed or an enemy relief force is approaching.
5-135. The commander uses a variety of signals to communicate this information, such as radio transmissions, voice commands, vehicle horns, whistles, or pyrotechnics. All signals must have at least one backup. For example, if the signal to shift fire fails, the assault element should not attack the target unless it receives the backup signal. Signals sent out before initiation of the ambush should not expose the ambush to detection by the enemy. The commander reviews SOP signals to see if they need to be revised or augmented to meet specific situational requirements.
5-136. Surprise, coordinated fires, and control are the keys to a successful ambush. Surprise allows the ambush force to seize control of the situation. If total surprise is not possible, it must be so nearly complete that the target does not expect the ambush until it is too late to react effectively. Thorough planning, preparation, and execution help achieve surprise.
5-137. The commander conducts a leader's reconnaissance with key personnel to confirm or modify his plan. This reconnaissance should be undetected by the enemy to preclude alerting him. If necessary, the commander modifies the ambush plan and immediately disseminates those changes to subordinate leaders and other affected organizations. The commander must maintain close control during movement to, occupation of, and withdrawal from the ambush site. Control is most critical when the ambush unit is approaching the target. Leaders enforce camouflage, noise, and light discipline.
5-138. The ambush unit's security element remains at full alert and uses all available observation devices to detect the enemy's approach to the ambush site. Each soldier's duties within each element are rotated as necessary to maintain alertness.
5-139. All elements of the ambush force reconnoiter their routes of withdrawal to the selected rally point. When possible, soldiers or crews reconnoiter the route they will use.
5-140. The commander positions all his weapons, including mines and demolitions authorized by his rules of engagement, to obtain the maximum effectiveness against the target in the kill zone. He coordinates all fires, including those of supporting artillery and mortars. The goals of the support element are to isolate the kill zone, prevent the target's escape or reinforcement, and deliver a large volume of highly concentrated surprise fire into the kill zone. This fire must inflict maximum damage so the assault element can quickly assault and destroy the target.
5-141. Fire discipline is a key part of any ambush. Fire must be withheld until the ambush commander gives the signal to initiate the ambush. That signal should be fire from the most deadly weapon in the ambush. Once initiated, the ambush unit delivers its fires at the maximum rate possible given the need for accuracy. Otherwise, the assault could be delayed, giving the target time to react and increasing the possibility of fratricide. Accurate fires help achieve surprise as well as destroy the target. When it is necessary to assault the target, the lifting or shifting of fires must be precise. The assault element does not conduct its assault until enemy fires or resistance has been negated or eliminated.
5-142. If the ambush fails and the enemy pursues the ambush force, it may have to withdraw by bounds. It should use smoke to help conceal its withdrawal. Activating limited-duration minefields along the withdrawal routes after the passage of the withdrawing ambush force can help stop or delay enemy pursuit. The commander positions the support element to assist in the withdrawal of the assault element.
5-143. On the commander's order, the ambush force withdraws to the rally point, reorganizes, and starts its return march. At a previously established location, it halts and disseminates any combat information obtained as a result of the ambush to all elements of the ambush force. However, future information systems should be able to disseminate this information without the need to halt a heavy force.
5-144. The commander or his representative debriefs the ambush force to help identify enemy patterns of response, activities, and procedures, both inside and outside the ambush area once the force returns from conducting the ambush. Patterns should be analyzed and reported to all appropriate organizations through intelligence channels. The commander adjusts his tactics, techniques, and procedures to account for these patterns.
5-145. A counterattack is a form of attack by part or all of a defending force against an enemy attacking force, with the general objective of denying the enemy his goal in attacking (FM 3-0). The commander directs a counterattack-normally conducted from a defensive posture-to defeat or destroy enemy forces, exploit an enemy weakness, such as an exposed flank, or to regain control of terrain and facilities after an enemy success. A unit conducts a counterattack to seize the initiative from the enemy through offensive action. A counterattacking force maneuvers to isolate and destroy a designated enemy force. It can attack by fire into an engagement area to defeat or destroy an enemy force, restore the original position, or block an enemy penetration. Once launched, the counterattack normally becomes a decisive operation for the commander conducting the counterattack.
5-146. The commander plans and conducts a counterattack to attack the enemy when and where he is most vulnerable, while he is attempting to overcome friendly defensive positions. Normally, the commander attempts to retain his reserve or striking force to conduct a decisive counterattack once the enemy commits his main force to the attack. The commander assigns objectives to counterattacking forces when he intends for them to assault the enemy. He normally assigns attack-by-fire positions when he intends to counterattack using primarily direct and indirect fires.
 |
5-147. The two levels of counterattacks are major and local counterattacks. In both cases, waiting for the enemy to act first may reveal the enemy's main effort and create an assailable flank to exploit. A defending unit conducts a major counterattack to seize the initiative from the enemy through offensive action after an enemy launches his attack. A commander also conducts major counterattacks to defeat or block an enemy penetration that endangers the integrity of the entire defense, or to attrit the enemy by the defeat or destruction of an isolated portion of the attacking enemy. (See Figure 5-10.)
5-148. The commander of a major counterattack force typically organizes his combined arms assets into security, reconnaissance, main body, and reserve forces. He uses those defending forces already in contact with the enemy to fix or contain those same enemy forces. The commander may use a force committed to the counterattack, such as the striking force in a mobile defense, his reserve, another echelon's reserve, or designate any other force he deems appropriate to be the counterattack force. Any changes in task organization should be completed in time to allow units to conduct rehearsals with their attached or supported unit.
5-149. A commander conducts a local counterattack with whatever forces are immediately available to retake positions that have been lost to enemy action or to exploit a target of opportunity. The forces often consist of the reserves of subordinates and defending forces that survive after completing their withdrawal from lost positions. While it is unlikely that the commander changes the task organization of the forces conducting a local counterattack, he organizes the force into a security force and a main body. He may be able to designate an element to conduct reconnaissance.
5-150. The counterattack force is a committed force from the beginning of the defensive operation if the commander's defensive scheme hinges on a counterattack as the defeat mechanism, such as the strike force in a mobile defense. In this case, the commander should designate another force as his reserve.
5-151. The commander plans the counterattack to strike the enemy when the enemy force is vulnerable. As the enemy force advances, the defense may create gaps between enemy units, exposing the flanks and rear of elements of the attacking force. Immediately after an enemy force occupies a defended position, it is often disorganized and ill prepared to meet a sudden counterattack. Opportunity for effective counterattacks are usually brief; the commander must assess the situation rapidly, and the force must execute the counterattack swiftly. The commander assigns objectives or attack-by-fire positions to counterattacking forces, depending on whether he intends for the counterattacking force to close with and assault the enemy.
5-152. Major counterattack plans are normally developed as a branch or sequel to the main defensive plan. A major counterattack may achieve surprise when it strikes the enemy from an unanticipated direction. For that reason the force directed to conduct a major counterattack, such as the strike force in a mobile defense, should be involved in developing those plans as well as any plans to exploit potential success. Local counterattacks may or may not be the result of previous deliberate planning.
5-153. Surprise, coordinated fires, and control are the keys to a successful counterattack. Surprise allows the counterattacking force to seize control of the situation. If total surprise is not possible, it must be so nearly complete that the targeted enemy force does not expect the attack until it is too late to react effectively. Thorough planning and preparation help achieve surprise. The commander adjusts the positioning of his ISR assets and the taskings he gives those assets so he can determine the location and targets for his counterattack.
5-154. The commander conducts a leader's reconnaissance with key personnel to confirm or modify his counterattack plan. If necessary, the commander modifies the plan and disseminates those changes to subordinate leaders and other affected organizations. Each element of the counterattack force reconnoiters its planned axis of advance and routes it will take if possible. The commander maintains close control during movement to and occupation of hide positions and this reconnaissance process so the enemy does not detect the counterattack force prior to initiating the counterattack. Leaders enforce camouflage, noise, and light discipline.
5-155. The commander adjusts the planned positions of his weapon systems to obtain the maximum effectiveness against targets in the planned engagement area. He coordinates all fires, including those of supporting artillery and mortars. He wants his fires to isolate the targeted enemy force in the planned engagement area while preventing the target's escape or reinforcement. These fires must inflict maximum damage quickly before the enemy can respond to the counterattack.
5-156. A commander should not counterattack unless he has a reasonable chance of success. The commander attempts to retain his reserve for his decisive operation, conducted after the enemy reveals his main effort by committing the majority of his combat power. If the commander orders his reserve to conduct a planned counterattack, the reserve becomes a committed force and the commander should take measures to designate or reconstitute a new reserve.
5-157. The commander conducts the counterattack in the same manner in which he conducts any other attack. He shifts support and priorities of fire, designates targets to be engaged by offensive information operations. The counterattack force also performs those activities discussed in paragraphs 5-61 to 5-122.
5-158. Subordinate commanders initiate local counterattack with the forces on hand when it fits within the higher commander's intent. The conduct of a local counterattack should be swift and violent. It should exploit any disorganization on the part of the enemy, such as the confusion that temporarily exists in an attacking force after it seizes a defended position. A rapidly mounted local counterattack may yield better results than a more deliberate counterattack executed by a higher echelon because of the speed at which it can be launched.
5-159. In the face of a strong enemy penetration, a commander may conduct local counterattacks to retain or seize positions on the shoulders of the enemy's penetration. This prevents the enemy from widening the penetration while forces from other defending units engage the penetrating enemy forces. Holding the shoulders can also prevent the sacrifice of positional depth because the limited gap in the defensive position prevents an attacking enemy from fully exploiting his success.
5-160. A demonstration is a form of attack designed to deceive the enemy as to the location or time of the decisive operation by a display of force. Forces conducting a demonstration do not seek contact with the enemy (FM 3-0). A feint is a form of attack used to deceive the enemy as to the location or time of the actual decisive operation. Forces conducting a feint seek direct fire contact with the enemy but avoid decisive engagement (FM 3-0). A commander uses them in conjunction with other military deception activities. They generally attempt to deceive the enemy and induce him to move reserves and shift his fire support to locations where they cannot immediately impact the friendly decisive operation or take other actions not conducive to the enemy's best interests during the defense. Both forms are always shaping operations. The commander must synchronize the conduct of these forms of attack with higher and lower echelon plans and operations to prevent inadvertently placing another unit at risk.
5-161. The principal difference between these forms of attack is that in a feint the commander assigns the force an objective limited in size, scope, or some other measure. Forces conducting a feint make direct fire contact with the enemy but avoid decisive engagement. Forces conducting a demonstration do not seek contact with the enemy. The planning, preparing, and executing considerations for demonstrations and feints are the same as for the other forms of attack.
5-162. A raid is a form of attack, usually small scale, involving a swift entry into hostile territory to secure information, confuse the enemy, or destroy installations. It ends with a planned withdrawal from the objective area on mission completion (FM 3-0). A raid can also be used to support operations designed to rescue and recover individuals and equipment in danger of capture.
5-163. A simplified chain of command is an essential organizational requirement. A raid usually requires a force carefully tailored to neutralize specific enemy forces operating in the vicinity of the objective and to perform whatever additional functions are required to accomplish the objective of the raid. These additional functions can consist of the demolition of bridges over major water obstacles or the recovery of an attack helicopter pilot shot down forward of the forward line of own troops (FLOT). The commander incorporates any necessary support specialists during the initial planning stage of the operation.
5-164. When a commander and his staff plan a raid, they develop COAs that meet ethical, legal, political, and technical feasibility criteria. Planners require precise, time-sensitive, all-source intelligence. The planning process determines how C2, sustainment, target acquisition and target servicing will occur during the raid. Techniques and procedures for conducting operations across the FLOT, given the specific factors of METT-TC expected to exist during the conduct of the raid, are also developed. The commander and his staff develop as many alternative COAs as time and the situation permit. They carefully weigh each alternative. In addition to those planning considerations associated with other offensive operations, they must determine the risks associated with conducting the mission and possible repercussions.
5-165. Time permitting, all elements involved in a raid should be fully rehearsed in their functions. The key elements in determining the level of detail and the opportunities for rehearsal prior to mission execution are time, OPSEC, and deception requirements.
|
5-166. A spoiling attack is a form of attack that preempts or seriously impairs an enemy attack while the enemy is in the process of planning or preparing to attack (FM 3-0). The objective of a spoiling attack is to disrupt the enemy's offensive capabilities and timelines while destroying his personnel and equipment, not to secure terrain and other physical objectives. (See Figure 5-11.) A commander conducts a spoiling attack whenever possible during friendly defensive operations to strike the enemy while he is in assembly areas or attack positions preparing for his own offensive operation or is temporarily stopped. It usually employs heavy, attack helicopter, or fire support elements to attack enemy assembly positions in front of the friendly commander's main line of resistance or battle positions.
Figure 5-11. Spoiling Attack
5-167. The commander's reasons for conducting a spoiling attack include—
Disrupt the enemy's offensive preparations.
Destroy key assets that the enemy requires to attack, such as his fire support systems, fuel and ammunition stocks, and bridging equipment.
Gain additional time for the defending force to prepare its positions.
Reduce the enemy's current advantage in the correlation of forces.
The commander synchronizes the conduct of the spoiling attack with his other defensive operations.
5-168. The commander can employ his reserves in a spoiling attack to throw the enemy's offensive preparations off stride. He assumes the risk of not having a reserve or designates another force as his reserve in this case. The following basic considerations affect the spoiling attack:
The commander may want to limit the size of the force used in executing the spoiling attack.
Spoiling attacks are not conducted if the loss or destruction of the friendly attacking force would jeopardize the commander's ability to accomplish his defensive mission.
The mobility of the force available for the spoiling attack should be equal to or greater than that of the targeted enemy force.
Operations by artillery or aviation systems to prevent enemy elements not in contact from interfering with the spoiling attack are necessary to ensure the success of the operation.
5-169. There are two conditions that must be met to conduct a successful and survivable spoiling attack:
The spoiling attack's objective must be obtainable prior to the enemy being able to respond to the attack in a synchronized and coordinated manner.
The commander must prevent the force conducting the spoiling attack from becoming overextended.
If the spoiling attack fails to meet both conditions, it will likely fail, with grave consequences to the defense.