 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| The officers and men who permit themselves to be surprised deserve to die, and the commanding general will spare no efforts to secure them their desserts. |
| D. H. Hill, 1863 |
Security operations are those operations undertaken by a commander to provide early and accurate warning of enemy operations, to provide the force being protected with time and maneuver space within which to react to the enemy, and to develop the situation to allow the commander to effectively use the protected force. The ultimate goal of security operations is to protect the force from surprise and reduce the unknowns in any situation. A commander may conduct security operations to the front, flanks, or rear of his force. The main difference between security operations and reconnaissance operations is that security operations orient on the force or facility being protected, while reconnaissance is enemy and terrain oriented. Security operations are shaping operations.
12-1. There are five forms of security operations-screen, guard, cover, area security, and local security.
Screen is a form of security operations that primarily provides early warning to the protected force.
Guard is a form of security operations whose primary task is to protect the main body by fighting to gain time while also observing and reporting information and preventing enemy ground observation of and direct fire against the main body. Units conducting a guard mission cannot operate independently because they rely upon fires and combat support assets of the main body.
Cover is a form of security operations whose primary task is to protect the main body by fighting to gain time while also observing and reporting information and preventing enemy ground observation of and direct fire against the main body.
Area security is a form of security operations conducted to protect friendly forces, installations, routes, and actions within a specific area.
Local security consists of low-level security operations conducted near a unit to prevent surprise by the enemy.
The screen, guard, and cover, respectively, contain increasing levels of combat power and provide increasing levels of security for the main body. However, more combat power in the security force means less for the main body. Area security preserves the commander's freedom to move his reserves, position fire support means, provide for command and control, and conduct sustaining operations. Local security provides immediate protection to his force.
12-2. All maneuver forces are capable of conducting security operations. Ground and air cavalry units and scout platoons are specially trained, equipped, and organized to conduct security missions; however, there are rarely enough of them to meet all the security needs of a force. A commander should ensure that subordinate maneuver units train to perform specific security missions. This allows subordinate units to add these missions to their mission-essential task list (METL) and train for them. Habitual relationships with attachments are required to obtain proficiency in these missions.
12-3. A maneuver force commander normally designates the security area within which his security force operates. In this chapter, the force (or facility) being secured is called the main body. When discussing the forms of security operations, the terms stationary and moving describe the actions of the main body, not the security force.
12-4. All forces, regardless of whether they are combat, combat support (CS), or combat service support (CSS), have an inherent responsibility to provide for their own local security. Local security consists of observation posts (OPs), local security patrols, perimeter security, and other measures to provide close-in security of a force. This chapter focuses on security operations conducted by one force or a subordinate element of a force that provides security for the larger force. Echelon-specific manuals discuss local security.
12-5. Successful security operations depend on properly applying five fundamentals:
Provide early and accurate warning.
Provide reaction time and maneuver space.
Orient on the force or facility to be secured.
Perform continuous reconnaissance.
Maintain enemy contact.
12-6. The security force provides early warning by detecting the enemy force quickly and reporting information accurately to the main body commander. The security force operates at varying distances from the main body based on the factors of METT-TC. As a minimum, it should operate far enough from the main body to prevent enemy ground forces from observing or engaging the main body with direct fires. The earlier the security force detects the enemy, the more time the main body has to assess the changing situation and react. The commander positions ground security and aeroscouts to provide long-range observation of expected enemy avenues of approach, and he reinforces and integrates them with available intelligence collection systems to maximize warning time.
12-7. The security force provides the main body with enough reaction time and maneuver space to effectively respond to likely enemy actions by operating at a distance from the main body and by offering resistance to enemy forces. The commander determines the amount of time and space required to effectively respond from information provided by the intelligence preparation of the battlefield (IPB) process and the main body commander's guidance regarding time to react to enemy courses of action (COA) based on the factors of METT-TC. The security force that operates farthest from the main body and offers more resistance provides more time and space to the main body. It attempts to hinder the enemy's advance by acting within its capabilities and mission constraints.
12-8. The security force focuses all its actions on protecting and providing early warning to the secured force or facility. It operates between the main body and known or suspected enemy units. The security force must move as the main body moves and orient on its movement. The security force commander must know the main body's scheme of maneuver to maneuver his force to remain between the main body and the enemy. The value of terrain occupied by the security force hinges on the protection it provides to the main body commander.
12-9. The security force aggressively and continuously seeks the enemy and reconnoiters key terrain. It conducts active area or zone reconnaissance to detect enemy movement or enemy preparations for action and to learn as much as possible about the terrain. The ultimate goal is to determine the enemy's COA and assist the main body in countering it. Terrain information focuses on its possible use by the enemy or the friendly force, either for offensive or defensive operations. Stationary security forces use combinations of OPs, aviation, patrols, intelligence collection assets, and battle positions (BPs) to perform reconnaissance. Moving security forces perform zone, area, or route reconnaissance along with using OPs and BPs, to accomplish this fundamental.
12-10. Once the security force makes enemy contact, it does not break contact unless specifically directed by the main force commander. The security asset that first makes contact does not have to maintain that contact if the entire security force maintains contact with the enemy. The security force commander ensures that his subordinate security assets hand off contact with the enemy from one security asset to another in this case. The security force must continuously collect information on the enemy's activities to assist the main body in determining potential and actual enemy COAs and to prevent the enemy from surprising the main body. This requires continuous visual contact, the ability to use direct and indirect fires, freedom to maneuver, and depth in space and time.
12-11. Military history contains numerous examples of the importance of security operations. The following historical example illustrates the major role of security operations in ensuring the success of an operation. This non-US example illustrates that the study of other armies and other times can contribute toward helping to understand the art and science of tactics.
|
12-12. There are a number of general considerations when conducting security operations. These apply to all forms of security operations but are most applicable to screen, guard, and cover missions.
12-13. Security operations are depicted on overlays using a lightning bolt on either side of the symbol representing the unit conducting the security operation and are labeled with the letter S, G, or C to denote screen, guard, or cover. The end of the lightning bolt has arrowheads that touch the designated operational graphics, which define the left and right limits of the security operation. (See Figure 12-1.)
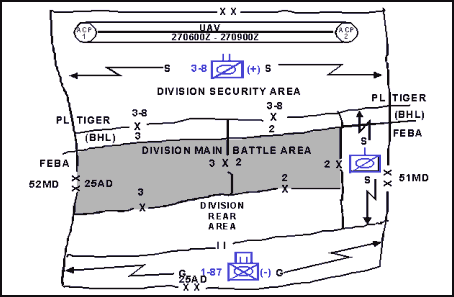
Figure 12-1. Common Security Control Measures
12-14. The screen, guard, and cover have many common control measures, starting with boundaries defining the security area. The main body commander establishes the security area. For a security force operating to the front of the main body, the lateral boundaries of the security area are normally an extension of the lateral boundaries of the main body. The security force's rear boundary is normally the battle handover line (BHL).
12-15. To establish a screen to the rear of a force, the lateral boundaries are also an extension of the boundaries of the main body, with the screening force's rear boundary being the rear boundary of the entire force. For a flank screen, the lateral boundaries of the security area are an extension of the rear boundary of the main body and its forward edges of the battle area (FEBA) or forward line of own troops (FLOT). The rear boundary of a flank screen is the lateral boundary of the main body. The rear boundary or another phase line (PL) may serve as a BHL between the security force and the main body to control the passing of responsibility for the enemy to the main body. Normally, the responsibility of the flank security force begins at the trail element of the advance security force or the lead combat element in the main body. It ends at the rear of the main body or the lead element of the rear security force. The main body commander clarifies responsibilities as necessary.
12-16. Either the main body or the security force commander designates additional PLs to control the operation. These PLs may serve as subsequent screen or delay lines. Each element of the security force must report when crossing or occupying them. Displacement to these subsequent PLs is event-driven. The approach of an enemy force, relief of a friendly unit, or movement of the protected force dictates the movement of the security force. The security force commander normally assigns additional lateral boundaries within the security area to delineate the areas of operations (AOs) for subordinate units.
12-17. The commander uses checkpoints and named areas of interest (NAIs) to indicate specific areas of interest and to coordinate movement and surveillance. He uses contact points to facilitate coordination with flank units during front and rear security missions or between elements of a security force within the security area. Units conducting flank security for a moving force physically contact the main body at contact points. If the security force commander wants to ensure coverage of a specific NAI or avenue of approach, he establishes OPs.
12-18. In addition to the planning considerations applicable to other types of operations discussed in this manual, such as control of key terrain and avenues of approach, the commander assigning a security mission and the security force commander must address special considerations:
Force to be secured.
Location and orientation of the security area.
Initial observation post locations.
Types of OPs.
Time to establish the security force.
Criteria for ending the security mission.
Augmentation of security forces.
Intelligence support to security operations.
Special requirements or constraints.
Fire planning.
Integration of ground and air operations.
Planning the engineer effort.
Reporting.
Positioning of command and control (C2) and CSS assets.
Combat service support.
12-19. The main body commander must designate the exact force to secure. This designation determines the limits of the security force's responsibilities. The security force must orient on the force it is securing. If the main body moves, the security force also moves to maintain its position in relation to the main body. Table 12-1, shows the typical size of security forces for a given echelon. The limited capabilities of most maneuver platoons prohibit them from having a mission separate from their parent company. Scout platoons are the exception to this rule.
Table 12-1. Typical Size of Security Forces for a Given Mission and Echelon
| SECURITY MISSION | ||||
| ECHELON | Screen | Advance Guard | Flank/Rear Guard | Cover |
| Battalion/Task Force | PLATOON | CO/TM | ||
| Brigade | CO/TM | BN TF | CO/TM | BN TF(+) |
| Division | DIV CAV BN TF |
DIV CAV (+) BDE |
DIV CAV BN TF |
DIV CAV (+) BDE |
| Corps | AR CAV SQD BN TF BDE |
ACR | AR CAV SQD(+) or BN TF |
ACR (+) or Division |
| Echelons Above Corps (JTF/Numbered Army) |
ACR (+) | DIV (+) or Corps |
ACR or BDE |
DIV (+) or Corps |
12-20. The main body commander determines the location, orientation, and depth of the security area in which he wants his security force to operate. He identifies specific avenues of approach and NAIs he wants covered. Depth in the security area provides the main body with more time to react to approaching enemy ground units. Occupying a deep security area allows the security force to destroy enemy reconnaissance assets without compromising critical OPs or positions. It also prevents the enemy from penetrating the security area too easily and prevents gaps from occurring when OPs or units displace or are lost. The wider the area to secure, the less the security force can take advantage of the increased depth because it will have fewer forces to position in depth. A very shallow security area may require a guard to provide needed reaction time.
12-21. The security force commander conducts a detailed analysis of the terrain in the security area. He establishes his initial dispositions (usually a screen line) as far forward as possible on terrain to allow good observation of avenues of approach. Next, he assigns clear responsibility for identified avenues of approach and designated NAIs. For a screen or guard, the initial screen line must be within supporting range of the main body, yet provide the desired amount of early warning.
12-22. The security force commander determines tentative initial OP locations along or behind the screen line to ensure effective surveillance of the sector and designated NAIs. The unit or asset that occupies each OP may shift its exact location to achieve the commander's intent. A commander may place more than one OP along a high-speed avenue of approach to allow an enemy contact to be tracked from one OP to another, thus maintaining enemy contact without requiring security forces to displace. The security force commander tasks subordinate units to perform reconnaissance and combat patrols to cover gaps between OPs. To prevent fratricide, the commander places a restrictive fire support coordinating measure around OP locations.
12-23. Observation posts may be either mounted or dismounted. Mounted OPs can use their vehicular optics, weapon systems, and speed of displacement. However, an enemy can detect them more readily than dismounted OPs. Dismounted OPs provide maximum stealth but lack the speed of displacement, optics, and weapons of mounted OPs. It takes a minimum of two soldiers to man an OP, and then for no more than 12 hours. Observation posts manned for more than 12 hours require, as a minimum, an infantry squad or scout section to ensure continuous operation. The screening force patrols dead space and the area between OPs, conducts resupply operations, and rests or sustains its personnel.
12-24. The main body commander must determine when to establish the security force. He decides this based on the activity of the main body and expected enemy activity. He must allow enough time for the security force to move into and occupy the security area to prevent enemy forces from penetrating the security area undetected. The factors of METT-TC influence how the security force deploys to and occupies the screen line. If the security mission is the result of a current reconnaissance mission, the security force is already positioned to begin its mission. This occurs frequently when a reconnaissance mission halts at a designated PL. Analyzing the factors of METT-TC determines which deployment technique meets mission requirements.
12-25. Security missions are usually time- or event-driven. The criteria for ending a security mission can be an action by the main body (such as completing a specific mission), a fixed-time period (for example, not allowing enemy penetration of a PL for two hours), or criteria based on the enemy force (such as its size). To terminate its security mission, the security force commander normally requires the permission of the main body commander to withdraw behind the rear boundary.
12-26. The main body commander is responsible for reinforcing the security force. When the security area is large, additional combat and CS assets may reinforce the security force's organic combat power. Any unique requirement posed by the mission may require assets not organic to the security force. Ground surveillance radars, engineers, and chemical reconnaissance elements are common attachments at the company or troop level.
12-27. Intelligence assets can greatly enhance security operations. These assets can conduct rapid surveillance of large areas to detect enemy presence. Remote sensors, unmanned aerial vehicles, battlefield surveillance radars, signal intelligence systems, and downlinks from theater and national assets can expand the area under surveillance and cue the security force. Advanced aircraft, such as the OH-58D Kiowa Warrior and the AH-64D Longbow, can detect and report enemy forces at extended ranges with thermal imaging and other advanced detection equipment. This permits a commander to concentrate his security force on likely enemy avenues of approach, NAIs, targeted areas of interest (TAIs), and restrictive terrain that degrades sensor performance. The commander can use his intelligence assets to detect enemy movements. This gains time to reposition his security force and mass other assets to counter enemy actions. The commander increases the size of his security force to reduce his risk if he cannot anticipate sufficient advance warning from his intelligence assets.
12-28. The main body commander may impose special requirements or constraints, including engagement, disengagement, and bypass criteria. He may order the security force not to become decisively engaged or fall below a certain combat strength. He may be willing to accept a lesser degree of security, which results from either the loss of more terrain or reduced preparation time by the main body, to preserve his security force for later use.
12-29. The main body commander positions his fire support assets to support his screen and guard forces. He allocates additional artillery to support a covering force. If the security force is assigned a wide AO, the commander may have to position his fire support assets to provide effective coverage of only the most likely enemy avenues of approach. This is particularly important for a screen because often the screen force can rely only on indirect fire to delay or disrupt the enemy. Providing adequate indirect fire support to the security force may require the main body to position its artillery well forward in the formation of the main body.
12-30. Integrating ground and air operations is critical to the success of many security missions. Aviation units, especially air cavalry, assist in reconnaissance of the security area as the ground element of the security force moves forward. They can perform the following tasks:
Extend the screen in front of the flank security element's screen line.
Screen forward of the ground security force.
Conduct reconnaissance of areas between ground maneuver units.
Assist in maintaining contact between the security force and the main body.
Assist in clearing the area between the flank security element and the main body during moving flank security missions.
Assist in disengaging ground units, which is especially valuable when conducting battle handover and passage of lines with the main body.
Monitor terrain that is hard to reach or would require too much time to cover with ground reconnaissance assets.
12-31. Countermobility plays a critical role in the security area. With properly integrated obstacles, the security force can maintain a mobility advantage over the enemy. The commander may mass engineer support in the security area initially and then shift support to the main battle area (MBA) once those units are prepared to begin developing engagement areas. They also enhance the mobility of the security force by identifying repositioning routes and task organizing engineers to provide breaching capability. However, the senior commander must consider the impact of prioritizing the countermobility effort in the security area rather than in the MBA or at the decisive point. In the offense, a commander can employ situational obstacles, covered by fire, on the flanks of an advancing force to provide additional security.
12-32. The security force reports enemy activities to the main body. The main body headquarters is responsible for disseminating that information to other affected friendly forces. The main body commander ensures that the security force has access to all pertinent intelligence and combat information obtained by the main body. This supplements the security force's capabilities. By continuously exchanging information, both the security force commander and the main body commander have time to choose a suitable COA. Force digitization greatly assists commanders in maintaining a common operational picture.
12-33. The unit logistics staff ensures that security element sustainment requirements are embedded in the unit's logistic chain and CSS orders and annexes. A key component in security element sustainment is developing, maintaining, and using standing operating procedures (SOP). Logisticians and operators must use the SOP and should be involved in their development. The SOP should be exercised and tested during training and changes made as needed. The commander ensures that his staff includes the sustainment of these security elements in logistics rehearsal.
12-34. The security element commander designates the individual within the security element who is responsible for sustaining the element. This is normally the senior noncommissioned officer within platoons and companies assigned security tasks. For example the platoon sergeant of a scout platoon assigned the mission of establishing a flank screen for a battalion task force would coordinate with the first sergeant of the adjacent company team to include the scout platoons sustainment requirements in the company team's logistics package. Likewise the first sergeant of a brigade reconnaissance troop assigned a screening mission coordinates directly with the brigade logistics and forward support battalion staffs for resupply and medical treatment. This individual must have access to the appropriate nets to coordinate logistic support and casualty evacuation.
12-35. That individual coordinates with the appropriate supporting logistics point of contact as soon as possible after receiving the security mission warning order. Coordination includes such items as the mission of the security element, the AO assigned to the security element, the routes it will take to that area from its current location, and movement times. He gives the exact sustainment requirements for the security element-including any specialized items of supply required by the mission, such as cratering charges-to the supporting logistics element. He ensures the support element establishes communication links with the security element and receives a copy of the support element's CSS overlay.
12-36. The commander must place special attention on treating and evacuating casualties for security elements operating removed from normal medical support because of time, terrain, or distance factors, or a need for the security element to remain undetected by the enemy. For this reason, the security element should include as many soldiers trained as combat lifesavers as is possible. The more combat lifesavers within the security element, the more prepared it is for casualties.
12-37. The security force commander positions himself where he can best control the operation. This is often where he can observe the most dangerous enemy avenue of approach. He positions his command post to provide continuous control and reporting during initial movements. His combat trains position behind masking terrain but remain close enough to the combat elements of the security force to provide rapid response. They are best sited along routes that provide good mobility laterally and in-depth.
12-38. All stationary security missions are established in a similar manner. In deploying into the security area, the security force must deal with competing requirements: to establish the security area quickly to meet mission requirements, and to provide the necessary level of security for itself. The security force moves into the security area using one of three basic methods: tactical road march, movement to contact, or zone reconnaissance.
12-39. The fastest but least secure method of deploying is a tactical road march from the rear boundary of the security area to the initial positions. The security force moves to a release point on the rear boundary. From the release point, subordinate elements deploy to occupy initial positions, moving by the quickest means possible. This method is appropriate when enemy contact is not expected, time is critical, or an aviation unit is conducting a zone reconnaissance forward of the ground element and has found no enemy in the security area.
12-40. In the second method, the security force conducts a movement to contact from a line of departure (usually the rear boundary of the security area) to the initial positions. This method is slower than a tactical road march but more secure. It is appropriate when enemy contact is likely, time is limited, terrain reconnaissance is not needed, or an aviation unit is conducting zone reconnaissance forward of the ground element and enemy forces have been detected in the security area.
12-41. The most secure method for moving to the initial positions is for the security force to conduct a zone reconnaissance from the security area rear boundary to its initial security line positions or the forward limit of the security area. Given adequate time, this method is preferred because it allows the security force to clear the security area and become familiar with the terrain that it may have to defend. The security force can reconnoiter potential subsequent positions and fire support system firing positions as it moves to its initial positions. A zone reconnaissance is appropriate when time is available and information about the enemy or terrain is unknown. While this technique provides information of tactical value on the enemy and terrain in the area, it may also be time consuming. Using air reconnaissance forward of the ground units increases the speed and security of the movement.
12-42. There are three techniques of occupying and moving in a flank security area for moving security missions based on how the security force crosses the line of departure:
Security force crosses the line of departure (LD) separately from the main body and deploys to perform the mission.
Security force crosses the LD separately from main body; lead elements conduct a movement to contact.
Security force crosses the LD with the main body and conducts a zone reconnaissance out to the limit of the security area.
12-43. The security force should not be required to make its own penetration when it faces prepared enemy defenses. This may prevent or significantly delay the security force from assuming its duties. These three techniques are often combined.
12-44. In the first technique, illustrated in Figures 12-2 and 12-3, the security force crosses the LD separately from the main body and deploys to perform the mission. The security force then conducts a tactical road march, an approach march, or tactical movements parallel to the main body and drops off OPs or occupies BPs along the flank of the main body. This technique keeps the two forces from interfering with each other during deployment. It is appropriate when another force penetrates the line of contact, the main body is not in contact with the enemy and is moving quickly, the LD is uncontested, and the IPB process indicates that enemy contact is not likely in the area through which the security force is moving. It is the fastest but least secure technique.
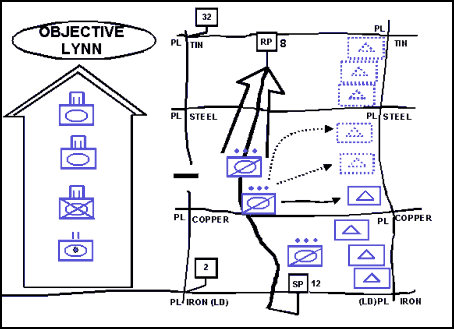
Figure 12-2. Security Force Crossing the LD Separately from the Main Body to Establish a Flank Screen
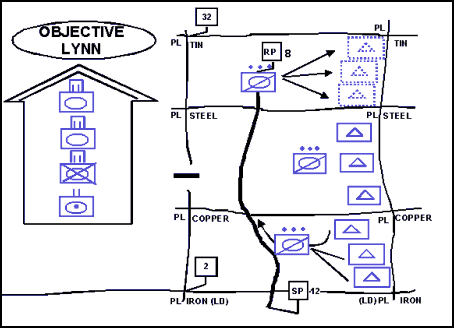
Figure 12-3. Security Force Continuing to Cross the LD Separately from the Main Body to Establish a Flank Screen
12-45. In the second technique, the security force crosses the LD separately from the main body, and its lead elements conduct a movement to contact. Follow-on elements occupy positions as they are reached. (See Figure 12-4.) This technique is appropriate to use when the main body is moving slower than in the first method, the LD is uncontested, and the IPB process indicates possible enemy contact. It is slower than the previous technique but provides better security.
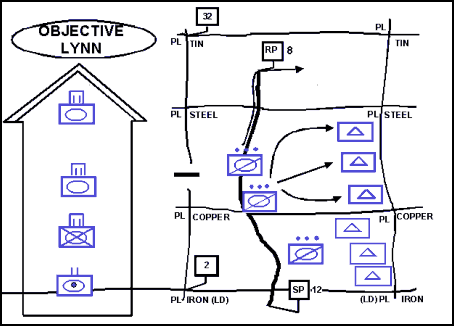
Figure 12-4. Second Technique Used by a Moving Flank Security Force to Establish a Moving Flank Screen
12-46. Finally, in the third technique, the security force crosses the LD with the main body and conducts a zone reconnaissance out to the far limit of the security area. (See Figure 12-5.) This technique is appropriate when the LD is also the line of contact, the main body makes its own penetration of the enemy defenses along the line of contact, the main body is moving slowly, and the enemy situation is not clearly understood. The security force may follow the lead element of the main body through the gap and deploy when the situation permits. This technique provides increased security for both the security force and the main body; it is also the most time-consuming.
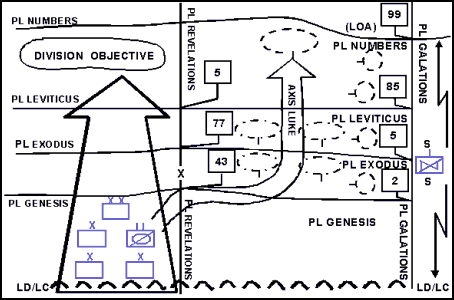
Figure 12-5. Third Technique Used by a Moving Flank Security Force to Establish a Flank Guard or Cover
12-47. A unit performing a screen observes, identifies, and reports enemy actions. Generally, a screening force engages and destroys enemy reconnaissance elements within its capabilities-augmented by indirect fires-but otherwise fights only in self-defense. The screen has the minimum combat power necessary to provide the desired early warning, which allows the commander to retain the bulk of his combat power for commitment at the decisive place and time. A screen provides the least amount of protection of any security mission; it does not have the combat power to develop the situation.
12-48. A screen is appropriate to cover gaps between forces, exposed flanks, or the rear of stationary and moving forces. The commander can place a screen in front of a stationary formation when the likelihood of enemy action is small, the expected enemy force is small, or the main body needs only limited time, once it is warned, to react effectively. Designed to provide minimum security with minimum forces, a screen is usually an economy-of-force operation based on calculated risk. If a significant enemy force is expected or a significant amount of time and space is needed to provide the required degree of protection, the commander should assign and resource a guard or cover mission instead of a screen. The security element forward of a moving force must conduct a guard or cover because a screen lacks the combat power to defeat or contain the lead elements of an enemy force.
12-49. A security force normally conducts a screen by establishing a series of OPs and patrols to ensure adequate surveillance of the assigned area. The commander uses reconnaissance patrols (mounted, dismounted, and aerial), relocates OPs, and employs technical assets to ensure continuous and overlapping surveillance. The commander also employs terrain data base analytical support systems to ensure the integration of his reconnaissance and surveillance assets to provide that necessary coverage.
12-50. Unless the commander orders otherwise, a security force conducting a screen performs certain tasks within the limits of its capabilities. A unit can normally screen an avenue of approach two echelons larger than itself, such as a battalion scout platoon screening a battalion-size avenue of approach or a cavalry troop screening a regimental or brigade-size avenue of approach. If a security force does not have the time or other resources to complete all of these tasks, the security force commander must inform the commander assigning the mission of the shortfall and request guidance on which tasks must be completed and their priority. After starting the screen, if the security unit commander determines that he cannot complete an assigned task, such as maintain continuous surveillance on all avenues of approach into an AO, he reports and awaits further instructions. Normally, the main force commander does not place a time limit on the duration of the screen, as doing so may force the screening force to accept decisive engagement. Screen tasks are to—
Allow no enemy ground element to pass through the screen undetected and unreported.
Maintain continuous surveillance of all avenues of approach larger than a designated size into the area under all visibility conditions.
Destroy or repel all enemy reconnaissance patrols within its capabilities.
Locate the lead elements of each enemy advance guard and determine its direction of movement in a defensive screen.
Maintain contact with enemy forces and report any activity in the AO.
Maintain contact with the main body and any security forces operating on its flanks.
Impede and harass the enemy within its capabilities while displacing.
12-51. A screen normally requires the subordinate elements of the security force to deploy abreast. A screen force normally organizes itself into a number of OPs determined by the number of avenues of approach into the main force and any additional NAIs it must cover, as specified by the main force commander. The screening force may retain a small reaction force or reserve to extract endangered OPs.
12-52. The size of the avenue of approach kept under surveillance varies by echelon. Normally, a unit maintains observation over avenues of approach used by operationally significant enemy forces. These are normally avenues of approach used by enemy forces one echelon smaller than the friendly unit. For example, a battalion maintains surveillance over enemy company-size avenues of approach, while the corps maintains surveillance over division-size avenues of approach. The situation may require the unit to maintain surveillance over mobility corridors that can be used by enemy units two echelons smaller than the friendly force.
12-53. The control measures necessary to conduct a screen were previously discussed in this chapter under common security control measures in paragraphs 12-13 to 12-17. (Figure 12-6 displays examples of control measures associated with a screen.)
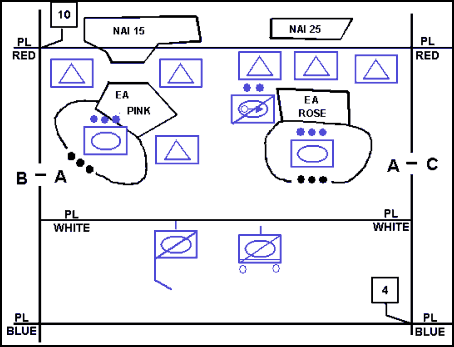
Figure 12-6. Control Measures Used in a Screen Mission
12-54. In setting up the screen, the screening force establishes OPs with overlapping fields of observation. The screen commander adjusts the location of his screening elements to take advantage of established links with higher-echelon sensors and collection assets. Patrols reconnoiter areas that cannot be observed from an OP. The force retains a small reserve if possible. If forces are available and the depth of the security area allows, the screening force establishes OPs in-depth on high-speed avenues of approach. The commander plans routes between the initial and subsequent screen lines to facilitate rapid occupation of subsequent screen lines. The screening force reserve deploys in-depth and positions itself to react to contingencies that develop during the screen. The screening force takes advantage of its surveillance, target acquisition, and night-observation equipment and information provided by higher-level systems to expand the area and quality of security provided.
12-55. Observation posts should remain undetected while those manning them report the presence of enemy elements. Prompt, accurate reporting is essential to keep the assets constituting the screen from being overrun or unknowingly bypassed. Once the enemy is detected, the OP uses fire support channels to direct engagement of the enemy at maximum range. This helps the OP avoid detection by the enemy and prevents the enemy from penetrating the screen line. The screening force may destroy enemy reconnaissance assets with direct fire if indirect fire cannot accomplish this task. It also attempts to slow the movement of other enemy elements, primarily using indirect fires and close air support.
12-56. As enemy pressure threatens the security of the OP, the unit reports and requests to move to the next screen line. The commander may have previously established criteria that allow the screening force to displace to subsequent screen lines, based on certain enemy or friendly actions. These criteria should allow subordinates to use their initiative when conducting operations. When displacing from one screen line to another, the screening force emphasizes rapid movement while maintaining contact with the enemy. This ensures that any gaps that occur during movement are quickly closed. The screen's C2 elements displace as required to maintain control and keep from being overrun. The force repeats this procedure as often as necessary.
12-57. The screening force commander decides when to move from one screen line to another. However, the main body commander decides when the screening force can move behind the PL that designates the rear boundary of the security area and hand off the battle to the main body.
12-58. The screening force may use several methods to move the screen as the protected force moves. Table 12-2 summarizes each method's advantages and disadvantages.
Table 12-2. Screen Movement Methods
| METHOD | CHARACTERISTICS | ADVANTAGES | DISADVANTAGES |
| Alternate Bounds by OPs |
|
|
|
| Alternate Bounds by Units |
|
|
|
| Successive Bounds |
|
|
|
| Continuous Marching |
|
|
|
|
12-59. A force maintains a moving screen along the flanks and rear of the protected force. The screen movement is keyed to time and distance factors associated with the main body's movement. (See Figure 12-7.) Responsibilities for a moving flank screen begin at the front of the main body's lead combat element and end at the rear of the protected force. They do not include front and rear security forces. A force executes a moving screen in the same way it conducts a stationary screen, except for the movement techniques.
12-60. The commander considers the factors of METT-TC in his decision regarding the movement method employed. Figures 12-8 and 12-9, illustrate four methods of controlling movement along a screen line:
Alternate bounds by individual OPs from the rear to the front. (This method is usually employed at the company/troop level and below.)
Alternate bounds by subordinate units from the rear to the front.
Successive bounds by units along the screen line.
Continuous marching along the route of advance.
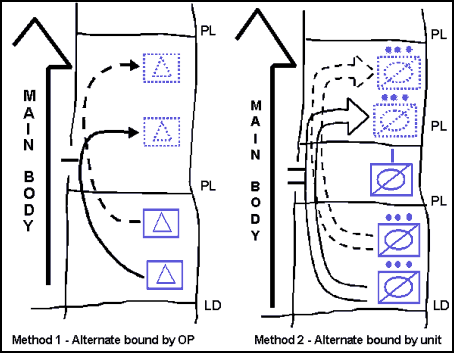
Figure 12-8. Displacement Methods for a Flank Screen
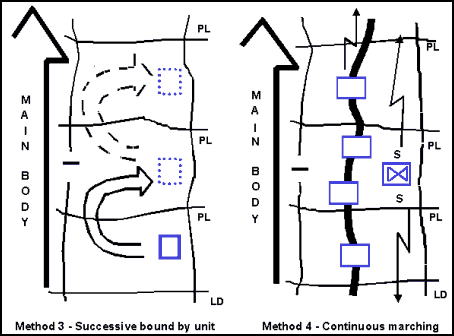
Figure 12-9. More Displacement Methods for a Flank Screen
12-61. Limited visibility often affects the screening force's ground and air observation capabilities. During limited visibility, the screening force uses all available night and thermal observation devices and depends more on electronic surveillance devices. Although the screening force can use technical reconnaissance and surveillance assets to offset limited visibility, it should also adjust its techniques and procedures to the conditions. For example, the commander of a screening force may need to adjust the number and location of his OPs in limited-visibility conditions. He can establish more OPs to cover avenues of approach that become masked in these conditions. He plans for indirect illumination and uses it when necessary. He closely coordinates his patrols to prevent misidentification and engagement by friendly elements. Rigorous sound and light discipline prevents compromise and potential bypass of OPs by enemy reconnaissance forces. Near OPs and along dismounted avenues of approach, the screening force can use trip flares, protective minefields, and mechanical devices, such as noisemakers integrated into tanglefoot obstacles, to detect the enemy and warn of his approach. Additional OPs along enemy avenues of approach can provide depth to facilitate detecting enemy forces that may have eluded forward security elements.
12-62. A guard differs from a screen in that a guard force contains sufficient combat power to defeat, cause the withdrawal of, or fix the lead elements of an enemy ground force before it can engage the main body with direct fire. A guard force routinely engages enemy forces with direct and indirect fires. A screening force, however, primarily uses indirect fires or close air support to destroy enemy reconnaissance elements and slow the movement of other enemy forces. A guard force uses all means at its disposal, including decisive engagement, to prevent the enemy from penetrating to a position were it could observe and engage the main body. It operates within the range of the main body's fire support weapons, deploying over a narrower front than a comparable-size screening force to permit concentrating combat power.
|
12-63. The three types of guard operations are advance, flank, and rear guard. A commander can assign a guard mission to protect either a stationary or a moving force. (See Figure 12-10.)
12-64. A unit conducting a guard performs certain tasks within its capabilities unless ordered otherwise. If a unit does not have the time or other resources to complete all of these tasks, it must inform the commander assigning the mission of the shortfall and request guidance on which tasks to complete or the priority of tasks. After starting the guard, if the unit determines that it cannot complete an assigned task, such as cause deployment of the enemy advance guard, it must report this to the commander and await further instructions. Guard tasks—
Destroy the enemy advance guard.
Maintain contact with enemy forces and report activity in the AO.
Maintain continuous surveillance of avenues of approach into the AO under all visibility conditions.
Impede and harass the enemy within its capabilities while displacing.
Cause the enemy main body to deploy, and then report its direction of travel.
Allow no enemy ground element to pass through the security area undetected and unreported.
Destroy or cause the withdrawal of all enemy reconnaissance patrols.
Maintain contact with its main body and any other security forces operating on its flanks.
12-65. A commander employs a guard when he expects enemy contact and requires additional security beyond that provided by a screen. The multiple requirements of the guard mission are often performed simultaneously over relatively large areas. While the guard force's exact size is determined by prevailing METT-TC conditions, Table 12-1 provides general guidance on the size of an echelon's guard force.
12-66. Whether the guard is for a stationary (defending) or moving (attacking) force, the various types of guard missions and knowledge of the terrain and enemy dictate the specific task organization of the guard force. The guard force commander normally plans to conduct the guard mission as an area defense (Chapter 9), a delay (Chapter 11), a zone reconnaissance (see FM 3-55), or a movement to contact (Chapter 4) mission within the security area.
12-67. The commander uses graphic control measures to control the operations of his guard force within the security area. The assigned mission also influences the size of the AO given to subordinate elements. For example, a movement to contact normally takes place across a narrower frontage than if the same unit makes a zone reconnaissance to allow adequate concentration of combat power.
12-68. The guard force may task its subordinate elements to conduct screen missions to the front and flanks of the guard force. This provides early warning of enemy forces and helps maintain contact with flank forces and any higher-echelon security force. An example of the latter would be a corps covering force operating in front of a division advance guard. The presence of a higher-echelon security force also influences how the guard force commander organizes his force and conducts operations. It specifically impacts the areas of fire support and CSS.
12-69. An advance guard for a stationary force is defensive in nature. It defends or delays in accordance with the main body commander's intent. An advance guard for a moving force is offensive in nature. (See Figure 12-11.) The advance guard develops the situation so the main body can use its combat power to the greatest effect. The main body's combat power must not be dissipated through piecemeal commitment. The full combat power of the main body must be available immediately to defeat the main enemy force.
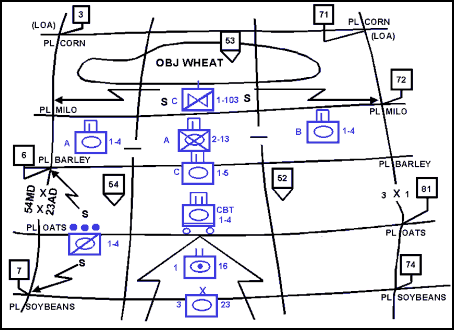
Figure 12-11. Advance Guard for a Division Shaping Attack
12-70. An advance guard for a moving force normally conducts a movement to contact. It organizes and uses the graphics of a movement to contact. (See Chapter 4.) Ground subordinate elements of a guard are normally deployed abreast to cover the axis of advance or the main body's AO.
12-71. The advance guard is responsible for clearing the axis of advance or designated portions of the AO of enemy elements. This allows the main body to move unimpeded, prevents the unnecessary delay of the main body, and defers the deployment of the main body for as long as possible.
|
12-72. The advance guard may operate behind the security force of a higher echelon. For example, a division may use its cavalry squadron (reinforced) as an offensive covering force, while each subordinate brigade column organizes one of its battalion task forces into an advance guard. (See Figure 12-12.) In these situations, the higher-echelon security force will initially develop the situation. A commander may task the advance guard to—
Coordinate and conduct the rearward passage of lines of the covering force.
Reduce obstacles to create lanes or improve existing lanes as required to support the maneuver of the main body.
Eliminate enemy forces bypassed by the covering force.
Coordinate and conduct a forward passage of lines through the covering force and fix enemy forces in the enemy's main defensive positions to allow the friendly main body to maneuver.
12-73. The movement of multiple security forces and the handoff of a detected enemy force from the higher-echelon security force to the lower-echelon security force is controlled using PLs, checkpoints, contact points, BHLs, and disengagement criteria, in addition to other graphic control measures. As a minimum, the covering force has a rear boundary that is also the forward boundary of the advance guard.
12-74. The advance guard engages in offensive operations when necessary to accomplish the mission. After the guard makes enemy contact, the commander determines whether the guard mission requires an attack, a defense, or a delay based on the factors of METT-TC. For example, if the guard force has sufficient combat power to defeat an enemy, it may conduct a hasty attack or defend from its current location. The guard force will not assault strong enemy positions from the front if this can be avoided. The advance guard then destroys the withdrawing enemy force as it exposes itself by moving to other positions. If the advance guard encounters an enemy force that it cannot stop from interfering with the movement of the main body, the security force reports its presence to the main body. It then establishes a defense, continues reconnaissance operations, and prepares to pass elements of the main body forward while facilitating the deployment of the main body.
12-75. If the guard force does not have enough combat power to defeat an approaching enemy, and the depth of the security area permits, the commander can delay back one or more positions before becoming decisively engaged. This reduces the enemy's combat power. Unless the security force is relieved of the guard mission, it must accept decisive engagement to prevent enemy ground forces from using direct fires to engage the main body.
12-76. A flank guard protects an exposed flank of the main body. A flank guard is similar to a flank screen except that the commander plans defensive positions in addition to OPs.
12-77. The commander of the main body designates the general location of the flank guard's positions. Areas of operation assigned to the flank guard should be sufficiently deep to provide early warning and reaction time. However, flank guards must remain within supporting range of the main body. To determine the guard force's exact initial positions, the flank guard commander considers the front and rear of the flank of the main body, the axis taken by the main body, the enemy's capabilities, and the available avenues of approach.
12-78. The flank guard moves to its initial positions using one of the movement techniques discussed in paragraphs 12-42 to 12-46. On reaching the initial positions, the flank guard establishes defensive positions in assigned BPs or within its assigned AO and establishes a screening element forward of these positions. (See Figure 12-13.) In situations where knowledge about the enemy is vague, the flank guard maintains a larger reserve than in situations where the enemy's actions are more predictable.
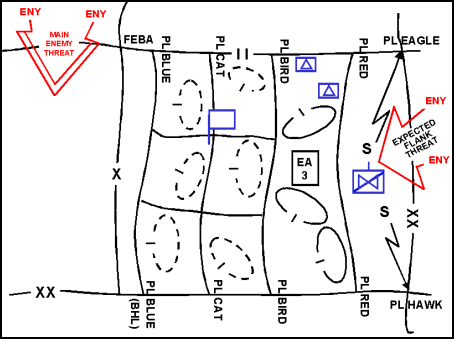
Figure 12-13. Stationary Flank Guard
12-79. Once the flank guard makes contact with the enemy, it can attack; defend to defeat or fix enemy ground forces in their current positions before they can engage the main body; or conduct a delay as required by the situation.
12-80. When conducting a moving flank guard, a commander must address additional considerations beyond those applying to conducting a moving flank screen. Instead of occupying a series of OPs, the security force plans a series of BPs. The tasks associated with a guard mission apply to a moving flank guard. However, the number and location of echelon-specific avenues of approach over which the security force maintains continuous surveillance change as the main body moves. The security force monitors potential enemy avenues of approach for as long as they threaten the main body.
12-81. The lead element of a moving flank guard must accomplish three tasks. It must maintain contact with the protected force's main body, reconnoiter the area between that main body and the flank guard's routes of advance, and reconnoiter the flank guard's route. It accomplishes these tasks by conducting a zone reconnaissance. The speed of the main body determines how thoroughly it can carry out the reconnaissance. The exact size of the AO for any given unit conducting a guard is METT-TC dependent. For example, on typical central European terrain, an AO wider than 10 kilometers from the guard line to the boundary of the main body should not be assigned to a company or troop. An organization of this size quickly finds itself unable to match the movement of the main body. When the distance from the guard line to the main body boundary exceeds 10 kilometers, the commander of the flank security element should use two or more company-size elements abreast. This ensures that the element making contact with the main body is not overtasked and can match the tempo of the main body. An air cavalry troop may maintain contact with the main body, or a following ground element may perform route reconnaissance along the flank guard's route of advance. Under these conditions, the lead security element does not reconnoiter BPs or occupy them unless required when making contact.
12-82. The rest of the flank guard marches along the route of advance and occupies BPs as necessary. Criteria for the route are the same as in a moving flank screen. The commander designates company-size BPs parallel to the axis of the main body. He places these BPs outside the flank guard's route of advance and along avenues of approach into the flank guard. The flank guard occupies OPs along a screen line forward of these BPs.
12-83. Since the flank guard is moving in one direction and orienting on providing protection to the secured force in another direction, the flank guard commander plans control measures to facilitate this dual orientation. These control measures are normally associated with the moving screen, as well as PLs that run parallel to the direction of movement of the main body. The commander uses these PLs to control the delay or defense if the enemy attacks from the flank being protected. (See Figure 12-14.) He may also assign the flank guard an objective that secures the flank for the main body's objective or otherwise serves to orient its security efforts.
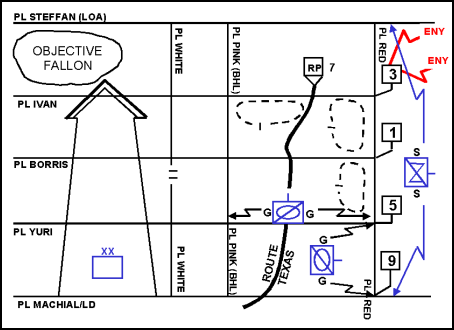
Figure 12-14. Moving Flank Guard Control Measures
12-84. The flank guard regulates its movement along the route of advance by the pace of the main body, the distance to the objective, and the enemy situation. The three methods of movement are successive bounds, alternate bounds, or continuous marching. (See Chapter 14.) If the main body stops, the flank guard occupies blocking positions. As the speed of the main body changes, the flank guard changes its movement methods. The guard commander must not allow the force to fall behind the main body or present a lucrative target by remaining stationary along the route.
12-85. If the flank guard becomes overextended, the guard commander informs the main body commander and recommends one of the following COAs:
Reinforce the flank guard.
Reduce the size of the flank guard's AO.
Screen a portion of the area and guard the rest.
12-86. The rear guard protects the exposed rear of the main body. This occurs during offensive operations when the main body breaks contact with flanking forces or during a retrograde. The commander may deploy a rear guard behind both moving and stationary main bodies. The rear guard for a moving force displaces to successive BPs along PLs or delay lines in depth as the main body moves. The nature of enemy contact determines the exact movement method or combination of methods used in the displacement (successive bounds, alternate bounds, and continuous marching).
12-87. During a retrograde, the rear guard normally deploys its ground maneuver elements abreast, behind the main body's forward maneuver units, generally across the entire AO. After the main body conducts a rearward passage of lines, the rear guard accepts battle handover and then defends or delays. Alternatively, the rear guard may conduct a relief in place as part of a deception plan or to take advantage of the best defensive terrain. In both cases, the rear guard establishes passage points and assists the rearward passage of the main body, if necessary. The rear guard accomplishes its defensive mission in the same way as any other guard operation after the main body clears the security area. As the main body moves, the rear guard moves to subsequent PLs in depth. Contact with the enemy force may eventually be lost if it does not follow the retrograding friendly force. Fighting a defense or a delay is necessary if the enemy detects the movement and attacks. (Chapter 11 discusses retrograde operations.)
12-88. The covering force's distance forward of the main body depends on the intentions and instructions of the main body commander, the terrain, the location and strength of the enemy, and the rates of march of both the main body and the covering force. The width of the covering force area is the same as the AO of the main body.
12-89. A covering force is a self-contained force capable of operating independently of the main body, unlike a screening or guard force. A covering force, or portions of it, often becomes decisively engaged with enemy forces. Therefore, the covering force must have substantial combat power to engage the enemy and accomplish its mission. A covering force develops the situation earlier than a screen or a guard force. It fights longer and more often and defeats larger enemy forces.
12-90. While a covering force provides more security than a screen or guard force, it also requires more resources. Before assigning a cover mission, the main body commander must ensure that he has sufficient combat power to resource a covering force and the decisive operation. When the commander lacks the resources to support both, he must assign his security force a less resource-intensive security mission, either a screen or a guard.
12-91. A covering force accomplishes all the tasks of screening and guard forces. A covering force for a stationary force performs a defensive mission, while a covering force for a moving force generally conducts offensive actions. A covering force normally operates forward of the main body in the offense or defense, or to the rear for a retrograde operation. Unusual circumstances could dictate a flank covering force, but this is normally a screen or guard mission.
12-92. Whether the cover is for a stationary (defending) or moving (attacking) force, the various types of cover missions, as well as knowledge of the terrain and enemy, dictate the specific task organization of the covering force. The covering force commander normally plans to conduct the cover mission as an area defense (Chapter 9), a delay (Chapter 11), a zone reconnaissance (see FM 3-55), or a movement to contact (Chapter 4) mission within the security area.
12-93. The commander normally assigns subordinate units one of these missions or the mission of screen or guard. The covering force uses those organizations and control measures associated with these missions. In addition, the commander establishes those control measures necessary for conducting the covering force's passage of lines (forward and rearward). (See Chapter 15.)
12-94. Although the commander can deploy any mobile force as a covering force, the corps covering force is normally built around the armored cavalry regiment or a division. Both have the C2 structures necessary for the forces involved and the capability to cover the geographical area typically required in a cover security mission. The corps commander tailors this unit to be self-contained by reinforcing it with assets such as attack helicopters, field artillery, engineers, air defense, tank, and infantry units with appropriate CSS to sustain the resulting force. A covering force is usually allocated additional artillery and engineer support beyond that normally given to a force of its size because it is operating beyond the main body's supporting range. The covering force commander normally maintains a sizable reserve to conduct counterattacks in the defense and to defeat enemy counterattacks in the offense.
12-95. A division covering force is normally a reinforced brigade, often with the divisional cavalry squadron as part of the covering force, to perform reconnaissance or other security missions. If the division AO is narrow enough, an adequately reinforced cavalry squadron may perform a cover mission. At both corps and division echelons, the amount of reinforcement provided to the covering force determines the distance and time it can operate away from the main body. These reinforcements typically revert to their parent organizations on passage of the covering force. Brigades and battalions typically organize a guard force instead of a covering force because their resources are limited.
12-96. Since one task of the covering force is to deceive the enemy into thinking he has found the main body, the commander should supply the covering force with combat systems that are representative of the main body. For example, if the main body has organic or reinforcing systems, such as MLRS, available to it, the commander should organize the covering force with the same systems.
|
12-97. An offensive covering force seizes the initiative early for the main body commander, allowing him to attack decisively. Figure 12-15 shows an attacking main body with an advance covering force and a flank guard.
12-98. Unless the commander orders otherwise, an offensive covering force performs specific tasks within its capabilities. If a unit does not have the time or other resources to complete all of these tasks, it must inform the commander assigning the mission of the shortfall and request guidance on which tasks to complete or the priority of tasks. After starting the mission, if the unit determines that it cannot complete an assigned task, such as destroying or repelling enemy reconnaissance and security forces in the enemy security area, it must report this to the commander and await further instructions. Offensive covering force tasks include—
Performing zone reconnaissance along the main body's axis of advance or within the AO.
Clearing or bypassing enemy forces within the AO in accordance with bypass criteria.
Denying the enemy information about the strength, composition, and objective of the main body.
12-99. Covering tasks against a defending enemy include—
Penetrating the enemy's security area to locate enemy main defensive positions.
Determining enemy strengths and dispositions.
Locating gaps or weaknesses in the enemy's defensive scheme.
Defeating or repelling enemy forces as directed by the higher commander.
Deceiving the enemy into thinking the main body has been committed and causing him to launch counterattacks prematurely.
Fixing enemy forces to allow the main body to maneuver around enemy strengths or through weaknesses.
12-100 In a meeting engagement, covering tasks include—
Destroying enemy reconnaissance, the advance guard, and the lead elements of the main body.
Determining the location of enemy assailable flanks.
Fixing enemy forces to allow the main body to maneuver around enemy strengths or through weaknesses.
12-101. Planning for offensive covering force operations is similar to planning for zone reconnaissance or movement to contact. Mission analysis using the products of the IPB process helps determine the width of the area to cover and areas (NAIs and TAIs) or routes of special importance. The commander determines specific missions for subordinate elements and assigns boundaries. The covering force commander retains a reserve, which is ready to deploy anywhere in the covering force area. This reserve may be centrally located; it typically locates itself on the most dangerous or critical avenue of approach in the security area.
12-102. The covering force advances on a broad front, normally with its subordinate ground maneuver elements abreast (except for the reserve). This force should clear the enemy's security area of small combat elements while penetrating into the enemy's main defenses. Air cavalry normally reconnoiters forward of advancing ground covering force elements. On enemy contact, the air cavalry reports the enemy's location to the appropriate ground unit and maintains contact. Once the air cavalry makes contact, the covering force rapidly develops the situation. It reports enemy dispositions immediately to the main body commander so he can exploit enemy weaknesses. The covering force fixes encountered enemy forces and destroys them using fire and movement. The covering force does not bypass enemy forces without the permission of the main body commander.
12-103. If the covering force discovers a gap in the enemy's defenses, it prepares to exploit the weakness and disrupt the integrity of that defense. The covering force commander immediately reports this to the main body commander so he can divert main body follow-on forces to support the penetration. The main body commander synchronizes the penetration by the covering force with the arrival of other maneuver units, CS, and CSS to prevent counterattacking enemy forces from isolating and destroying the penetrating elements of the covering force.
12-104. When the covering force can advance no farther, it defends and prepares to assist the forward passage of lines of main body units. It continues to perform reconnaissance of enemy positions to locate gaps or assailable flanks. The covering force may guide main body units as they attack through or around the covering force. If the covering force has accomplished its mission, the main body commander will attack the enemy's weak point with previously uncommitted main body forces at the appropriate time.
12-105. When the main body commander perceives a significant threat to one of his flanks, he normally establishes a flank covering force. That force conducts its mission in much the same way as a flank guard performs its mission. The main differences between the two missions are the scope of operations and the distance the covering force operates away from the main body.
12-106. Just as in a flank guard, the flank covering force must clear the area between its route of advance and the main body. It must also maintain contact with an element of the main body specified by the main body commander. This element is normally part of the advance guard for the flank unit of the main body.
12-107. A defensive covering force prevents the enemy from attacking at the time, place, and combat strength of his choosing. (See Figure 12-16.) Defensive cover gains time for the main body, enabling it to deploy, move, or prepare defenses in the MBA. It accomplishes this by disrupting the enemy's attack, destroying his initiative, and establishing the conditions for decisive operations. The covering force makes the enemy deploy repeatedly to fight through the covering force and commit his reserve or follow-on forces to sustain momentum.
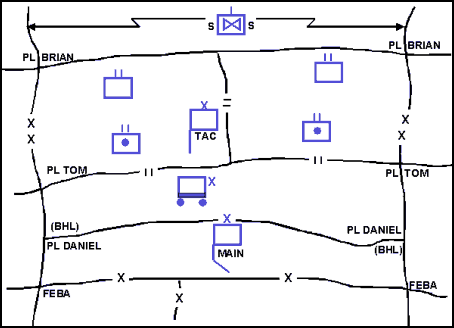
Figure 12-16. Generic Depiction of a Defensive Cover
12-108. Unless the commander orders otherwise, a defensive covering force performs certain tasks within its capabilities. If a unit does not have the time or other resources to complete all of these tasks, it must inform the commander assigning the mission of the shortfall and request guidance on which tasks to complete or the priority of tasks. After starting the mission, if the unit determines that it cannot complete an assigned task, such as defeat enemy advance guard formations, it must report this to the commander and await further instructions. A defensive covering force emphasizes the following tasks—
Prevent the main body from being surprised and becoming engaged by direct-fire weapons.
Defeat enemy advance guard formations.
Maintain continuous surveillance of high-speed avenues of approach into the security area.
Defeat all enemy reconnaissance formations before they can observe the main body.
Cause the deployment of the enemy main body.
Determine the size, strength, composition, and direction of the enemy's main effort.
Destroy, defeat, or attrit enemy forces within its capacity.
Deprive the enemy of his fire support and air defense umbrellas, or require him to displace them before he attacks the MBA.
Deceive the enemy regarding the location of main body and main defensive positions.
Avoid being bypassed.
12-109. The defensive covering force may be required to defend, delay, or counterattack. If the covering force area is not occupied, the force may have to reconnoiter and clear the area before establishing the cover. As in offensive operations, aerial reconnaissance is necessary to extend the area covered. Aviation units can screen less threatened areas and rapidly reinforce with their fires when other elements of the covering force are heavily engaged.
12-110. Whatever the command relationships may be at the outset, as the defensive covering force battle progresses, the covering force will be forced back toward the MBA. At this time, some or all of the covering force units fall under the control of the brigades charged with defending the MBA. Once the defensive covering force completes its mission, ground maneuver task forces reinforcing the covering force can do one of three things, separately or in combination. They can take up positions in the MBA, undergo reconstitution, or become part of the echelon reserve. The commander may use cavalry and other reconnaissance elements from the covering force as flank or rear security forces. Alternatively, he may use them to locate and follow the movement of the enemy's follow-on forces. They only establish BPs in the MBA as a last resort.
12-111. The conduct of a rearward passage of lines is an inherent part of the conduct of a defensive cover with its associated requirement to transfer responsibility for the battle between units. The commander must thoroughly plan this complex task as an integral part of the covering force mission. Passage of lines may not occur simultaneously for all covering force units. As some units begin passage, others may still be taking advantage of offensive opportunities in other parts of the security area. The covering force commander prepares to continue fighting in those portions of the security area where his forces are successful to set up offensive opportunities for the main body.
12-112. The covering force commander must exercise caution when issuing orders within the covering force. Commanders at each echelon will have a different perspective of the battle. This is never truer than in a covering force action. For example, while the covering force commander may be told to delay forward of a river line for 72 hours, he may tell his task force commanders to defend in certain BPs, perhaps for a specified period of time. Once the period expires, the covering force should not automatically retire from the covering force area. It must create enough resistance to force the enemy to deploy his main forces. Commanders at each echelon must precisely state the mission to their subordinate commanders without telling them how to do it. (This is mission command. See FM 6-0.) All too often, a small-unit commander, when told to delay, yields to an urge to shoot too little, pull back too early, and move back too far. Thus, it is imperative that each commander conveys to his subordinates precisely what their mission is in the context of the overall mission. Within a covering force, company teams and troops are mainly involved in a series of defensive operations.
12-113. Area security operations may be offensive or defensive in nature. They focus on the protected force, installation, route, or area. Forces to protect range from echelon headquarters through artillery and echelon reserves to the sustaining base. Protected installations can also be part of the sustaining base or they can constitute part of the area's infrastructure. Areas to secure range from specific points (bridges and defiles) and terrain features (ridge lines and hills) to large population centers and their adjacent areas.
12-114. Operations in noncontiguous AOs require commanders to emphasize area security. During offensive and retrograde operations, the speed at which the main body moves provides some measure of security. Rapidly moving units in open terrain can rely on technical assets to provide advance warning of enemy forces. In restrictive terrain, security forces focus on key terrain such as potential choke points.
12-115. A commander executes rear area and base security as part of an echelon's sustaining operations responsibilities or as part of stability operations and support operations. (Rear area and base security and route and convoy security operations are the subject of Appendix E.) During conventional operations, area security operations are normally economy-of-force measures designed to ensure the continued conduct of sustaining operations designed to support the echelon's decisive and shaping operations. All area security operations take advantage of the local security measures performed by all units regardless of their location within the AO.
12-116. Since civilians are normally present within the AO, a unit restrains its use of force when conducting area security operations. However, the commander always remains responsible for protecting his force and considers this responsibility when establishing his rules of engagement. Restrictions on conducting operations and using force must be clearly explained and understood by everyone. Soldiers must understand that their actions, no matter how minor, may have far-reaching positive or negative effects. They must realize that either friendly or hostile media and psychological operations organizations can quickly exploit their actions, especially the manner in which they treat the civilian population.
12-117. Sometimes area security forces must retain readiness over long periods without contact with the enemy. This occurs most often during area security operations when the enemy knows that he is seriously overmatched in terms of available combat power. In this case, he normally tries to avoid engaging friendly forces unless it is on his terms. Forces conducting area security should not develop a false sense of security even if the enemy appears to have ceased operations within the secured area. The commander must assume that the enemy is observing his operations and is seeking routines, weak points, and lax security for the opportunity to strike with minimum risk.
12-118. Local security includes any local measure taken by units against enemy actions. It involves avoiding detection by the enemy or deceiving the enemy about friendly positions and intentions. It also includes finding any enemy forces in the immediate vicinity and knowing as much about their positions and intentions as possible. Local security prevents a unit from being surprised and is an important part of maintaining the initiative. The requirement for maintaining local security is an inherent part of all operations. Units perform local security when conducting full spectrum operations, including tactical enabling operations.
12-119. Units use both active and passive measures to provide local security. Active measures include-
Using OPs and patrols.
Establishing specific levels of alert within the unit. The commander adjusts those levels based on the factors of METT-TC.
Establishing stand-to times. The unit SOP should detail the unit's activities during the conduct of stand-to.
12-120. Passive local security measures include using camouflage, movement control, noise and light discipline, and proper communications procedures. It also includes employing available ground sensors, night-vision devices, and daylight sights to maintain surveillance over the area immediately around the unit.
12-121. A combat outpost is a reinforced OP capable of conducting limited combat operations. (See Figure 12-17.) Using combat outposts is a technique for employing security forces in restrictive terrain that precludes mounted security forces from covering the area. They are also used when smaller OPs are in danger of being overrun by enemy forces infiltrating into and through the security area. The commander uses a combat outpost when he wants to extend the depth of his security area, when he wants his forward OPs to remain in place until they can observe the enemy's main body, or when he anticipates that his forward OPs will be encircled by enemy forces. Both mounted and dismounted forces can employ combat outposts.
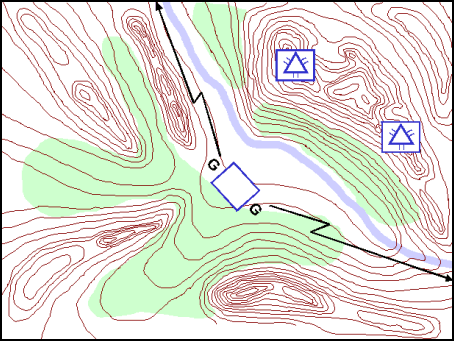
Figure 12-17. Combat Outposts
12-122. While the factors of METT-TC determine the size, location, and number of combat outposts established by a unit, a reinforced platoon typically occupies a combat outpost. A combat outpost must have sufficient resources to accomplish its designated missions, but not so much as to seriously deplete the strength of the main body. It is usually located far enough in front of the protected force to preclude enemy ground reconnaissance elements from observing the actions of the protected force.
12-123. The commander organizes a combat outpost to provide an all-around defense to withstand a superior enemy force. When the enemy has significant armored capability, a combat outpost may be given more than a standard allocation of antitank weapons. Forces manning combat outposts can conduct aggressive patrolling, engage and destroy enemy reconnaissance elements, and engage the enemy main body prior to their extraction. The commander should plan to extract his forces from the outpost before the enemy has the opportunity to overrun them.