 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
 RDL Homepage |
 Table of Contents |
 Document Information |
 Download Instructions |
| Regardless of the considerations which dictated the adoption of a defensive attitude, the tactics of defensive combat are essentially to develop the maximum firepower against an advancing enemy, to reduce our own losses by a better knowledge and utilization of the terrain, and thereby to stop the enemy's advance or throw him back by counterattack. |
| FM 100-5, Field Service Regulations: Operations, May 1941, Para 652 |
The area defense is a type of defensive operation that concentrates on denying enemy forces access to designated terrain for a specific time rather than destroying the enemy outright (FM 3-0). An area defense capitalizes on the strength inherent in closely integrated defensive organization on the ground. The commander may assign corps, divisions, and separate brigades the task of conducting an area defense as part of their mission. Subordinate echelons defend within their assigned areas of operations (AOs) as part of the larger-echelon's operation.
9-1. A commander should conduct an area defense when the following conditions occur:
When directed to defend or retain specified terrain.
When he cannot resource a striking force.
The forces available have less mobility than the enemy.
The terrain affords natural lines of resistance and limits the enemy to a few well-defined avenues of approach, thereby restricting the enemy's maneuver.
There is enough time to organize the position.
Terrain constraints and lack of friendly air superiority limit the striking force's options in a mobile defense to a few probable employment options.
9-2. The commander conducting an area defense combines static and mobile actions to accomplish his assigned mission. Static actions usually consist of fires from prepared positions. Mobile actions include using the fires provided by units in prepared positions as a base for counterattacks and repositioning units between defensive positions. The commander can use his reserve and uncommitted forces to conduct counterattacks and spoiling attacks to desynchronize the enemy or prevent him from massing.
9-3. The commander organizes his force to accomplish reconnaissance, security, main battle area (MBA), reserve, and sustaining operations. He has the option of defending forward or defending in depth. When the commander defends forward within an AO, he organizes his force so that he commits most of his combat power early in the defensive effort. To accomplish this he may deploy forces forward or plan counterattacks well forward in the MBA or even beyond of the MBA. If the commander has the option of conducting a defense in depth, he uses his security forces and forward MBA element to identify, define, and control the depth of the enemy's main effort while holding off secondary thrusts. This allows him to conserve his combat power, strengthen his reserve, and better resource the counterattack.
9-4. The commander directs his intelligence, surveillance, and reconnaissance (ISR) assets to determine the locations, strengths, and probable intentions of the attacking enemy force before and throughout the defensive operation. The commander places a high priority on early identification of the enemy's main effort. He may need to complement surveillance with combat actions that test enemy intentions. Fighting for information can have two benefits—it can force the enemy to reveal his intentions and disrupt his preparations.
9-5. In the defense, ISR operations overlap the unit's planning and preparing phases. Leaders performing reconnaissance tasks must understand that they often deploy before the commander fully develops his plan and they must be responsive to changes in orientation and mission. The commander ensures that his staff fully plans, prepares, and executes reconnaissance missions.
9-6. The commander balances the need to create a strong security force to shape the battle with the resulting diversion of combat power from his main body's decisive operation. The commander usually allocates security forces to provide early warning and protect those forces, systems, and locations necessary to conduct his decisive operation from unexpected enemy contact. On a battlefield where forces are contiguous with one another, the location of security forces is usually in front of the main defensive positions. On a noncontiguous battlefield they are located on avenues of approach between the protected force and known or suspected enemy locations.
9-7. Battalion and brigade security forces normally conduct screen or guard missions. At division level and above, the commander may use a covering force. A division commander may elect to have his security force conduct a guard mission if a corps covering force exists. Because an area security mission usually ties in closely with flank units, flank security forces are needed if there are gaps on the unit's flanks, which occurs during noncontiguous operations, or if gaps develop during the operation. A flank screen or guard is critical if an enemy avenue of approach into the defended area from the flanks could be uncovered during the defense. A commander does not normally assign a force the mission of conducting rear guard or rear cover during contiguous operations since it is unlikely that his force's rear area will become uncovered during the defense. He resources rear area security forces, to include a tactical combat force (TCF) or accepts the risk to his sustainment effort of not performing this function.
9-8. The commander builds his decisive operation around identified decisive points, such as key terrain or high-payoff targets. The commander's decisive operation in an area defense focuses on retaining terrain by using fires from mutually supporting, prepared positions supplemented by one or more counterattacks and the repositioning of forces from one location to another. The commander's decisive operation normally involves close combat since an area defense emphasizes terrain retention.
9-9. The commander normally positions his main body—the bulk of his combat power—within the MBA where he wants to conduct his decisive operation. The commander organizes his main body to halt, defeat, and ultimately destroy attacking enemy forces. The majority of the main body deploys into prepared defensive positions within the MBA. However, mobile elements of the force are ready to deploy where and when needed.
9-10. The commander's defensive plan should be able to succeed without using his reserve. However, the most likely mission of the reserve is to conduct a counterattack in accordance with previously prepared plans. A lower-echelon commander uses his reserve primarily to conduct local counterattacks to restore his defense's integrity or to exploit an opportunity. A senior commander uses his reserve to seize the initiative from the enemy when the opportunity presents itself. For example, a corps commander may target the effects of his reserve against enemy fire support and follow-on forces to achieve that effect.
9-11. The reserve is not a committed force. The commander can assign it a wide variety of tasks on its commitment, and it must be prepared to perform other missions. In certain situations, it may become necessary to commit the reserve to restore the integrity of the defense by blocking an enemy penetration or reinforcing fires into an engagement area (EA). These secondary tasks include—
Reinforcing the defense of committed forces.
Blocking or containing enemy forces that penetrate friendly defensive positions.
Relieving depleted units and providing for continuous operations.
Reacting to threats directed against the friendly force's sustainment effort. This includes acting as the echelon TCF when a separate TCF cannot be resourced.
Extending the flanks of a defending unit to prevent its envelopment.
Covering a retrograde movement.
9-12. Defending commanders are usually hard-pressed to establish and resource reserve forces because they are normally facing an enemy with superior combat power. Nevertheless, commanders at each echelon down to the battalion task force retain reserves as a means of ensuring mission accomplishment and for exploiting opportunities through offensive action. (Company commanders may retain a reserve based on the factors of METT-TC.) Commanders do not hold artillery and other fire support systems in reserve. (Such systems committed to rear area security operations are not in reserve.) Each echelon's reserve must have the mobility and striking power required to quickly isolate and defeat breakthroughs and flanking attempts. It must be able to seize and exploit fleeting opportunities in a powerful manner to throw the enemy's overall offensive off balance. The commander must resource his reserve so it can repeatedly attack, regroup, move, and attack again.
9-13. The size of the reserve is relative to the commander's uncertainty about the enemy's capabilities and intentions. The more uncertainty that exists, the larger the reserve. The reverse is also true. If the commander knows the size, dispositions, capabilities, and intentions of the enemy, he requires only a comparatively small reserve.
9-14. In some situations, the commander may not be able to resource a separate reserve. Therefore, he may constitute all or a portion of his reserve from his security force after it conducts a rearward passage of lines through MBA units. If the security force is the reserve for an area defense, the commander must withdraw it so it has sufficient time to occupy its reserve position, perform the necessary degree of reconstitution, and prepare plans for its reserve role. However, this is not the preferred option. Before battle handover, the senior commander must state the acceptable risk to the security force or the disengagement criteria in quantifiable terms, such as friendly strength levels, time, or event. In this case, after completing the rearward passage, the security force moves to an assembly area to prepare for its subsequent operations. This area should be free from enemy interference and clear of MBA units, main supply routes (MSRs), and the movements of other portions of the reserve.
9-15. The operations of the reserve usually become the echelon's decisive operation once committed. However, the commander can commit his reserve in a shaping operation to allow his ongoing decisive operation to achieve success. It no longer constitutes the force reserve on its commitment in either case, so the commander should designate another uncommitted force as his reserve. If he does not have that flexibility, he must hold his reserve for commitment at the decisive moment and accept risk.
9-16. The commander organizes an area defense by designating his MBA and assigning AOs, battle positions (BPs), or both to subordinate units located within the MBA. He creates a security area in front of the MBA. When possible, the boundaries of the subordinate elements of the security force coincide with those of the major defending units in the MBA. The security area should be deep enough to make the enemy displace as much of his supporting forces as possible, such as cannon artillery, sensors, and air defense artillery gun systems, before carrying his attack into the MBA. The commander also designates his rear area. (See Chapter 12 for a discussion of security operations.)
9-17. Area defense maneuver graphic control measures also include EAs, the forward edge of the battle area (FEBA), battle handover line (BHL), strong points, target reference points (TRPs), named areas of interest (NAIs), targeted areas of interest (TAIs), decision points, and various other fire control and countermobility control measures. (Figure 9-1 depicts the most common control measures. Chapters 2 and 8, and Appendix B define these defensive control measures.)
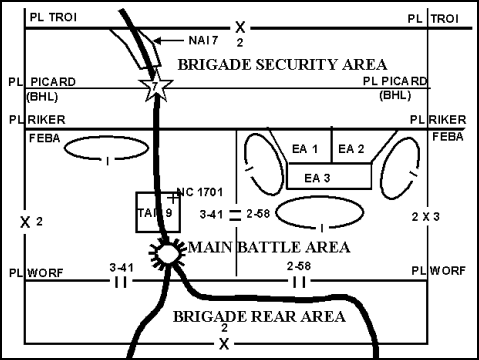
Figure 9-1. Typical Control Measures for an Area Defense
9-18. If the commander assigns a BP and an AO to a subordinate, the subordinate commander has specific guidance on the initial positioning of his forces. The commander ensures the synchronization of each of his subordinate units' defensive plans, and that his control measures, such as contact points and phase lines, are sufficient to ensure the continued control of his subordinates. He is responsible for fire and movement planning between the positions of his subordinate units. If subordinate unit commanders prepare their defensive plans in isolation, one or more assailable flanks between subordinate units could easily develop. (The organization of forces, control measures, planning, preparation, and execution of a passage of lines—a tactical enabling operation—are the subject of Chapter 15.)
9-19. The key to a successful area defense is the integration and synchronization of all available assets. The commander achieves this when he can employ the effects of his combined arms team at the decisive time and place. (The general defensive planning considerations addressed in Chapter 8 apply to the area defense.) The commander assigns missions, allocates forces, and apportions combat support (CS) and combat service support (CSS) resources within the battlefield organization of decisive, shaping, and sustaining operations. He decides where to concentrate his effort and where to take risks. The commander can rapidly redirect attack aviation and artillery systems initially allocated to shaping operations to support decisive operations at the appropriate time. (See Figure 9-2 for a graphical depiction of the organization of forces for an area defense in a contiguous AO. See Figure 9-3 for a graphical depiction of the organization of forces for an area defense in a noncontiguous AO.)
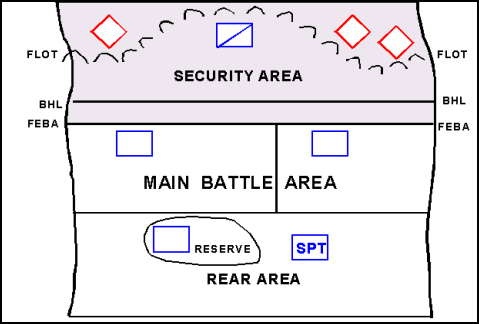
Figure 9-2. Organization of Forces for an Area Defense—Contiguous Area of Operations
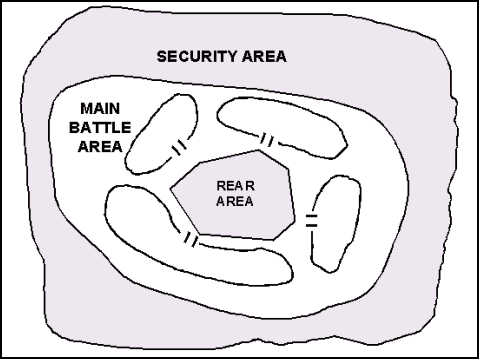
Figure 9-3. Organization of Forces for an Area Defense—Noncontiguous Area of Operations
9-20. The commander describes his concept of operation in sufficient detail so that his staff and subordinate commanders understand precisely how he intends to fight the battle. He ensures the coordination of maneuver and supporting actions among his subordinates. (FM 5-0 discusses the military decision making process and troop leading procedures.)
9-21. The commander's keys to a successful area defense are—
Capability to concentrate effects.
Depth of the defensive area.
Security.
Ability to take full advantage of the terrain, such as intervisibility lines.
Flexibility of defensive operations.
Timely resumption of offensive actions.
The crux of the commander's defensive challenge is to gain time to ensure a synchronized, effective defense. The commander organizes his defensive effort based on an analysis of the factors of METT-TC and the higher commander's concept. He decides where to concentrate his efforts and how to economize his forces. He forces the enemy forces to enter his EAs. To succeed in its area defense mission, the unit must also counteract the enemy's initiative. The commander should take advantage of available offensive opportunities that do not risk the integrity of his defense, such as a spoiling attack or counterattack.
9-22. In planning an area defense, the commander may choose between two forms of defensive maneuver. He can organize either a defense in depth or a forward defense. A higher commander may dictate the form of maneuver or impose restrictions that eliminate a subordinate commander's form of maneuver. These restrictions can include time, security concerns, and directed retention of specific terrain. These two deployment choices are not totally exclusionary. Part of a commander's forces can conduct a forward defense while the other part conducts a defense in depth.
9-23. In determining the form of maneuver, the commander decides where the defensible terrain is located within his assigned AO based on its terrain characteristics and his estimate of the enemy's chosen course of action (COA). Those terrain characteristics include terrain relief patterns, avenues of approach into and within the AO, the location of any key or decisive terrain, existing obstacles and choke points, to include rivers and fording sites. The other factors of METT-TC also influence the commander's decision.
9-24. Attempting to defend everything defends nothing. Therefore, the commander carefully designs his defense plan to ensure his defending force can halt the enemy attack and develop an opportunity to seize the initiative and undertake offensive operations. The cohesion of the defending force has a significant impact on the overall effectiveness of the defense. The commander must be prepared to adjust the defensive dispositions to meet changes in the enemy's dispositions to maintain that cohesion if the defense is to remain viable.
9-25. The area defense concept requires that defensive positions accomplish their mission independently or in combination by defeating the enemy by fire, absorbing the strength of the attack within the position, or destroying the enemy with a local counterattack. The commander combines the advantages of fighting from prepared positions, obstacles, planned fires, and local counterattacks to isolate and overwhelm selected enemy formations. He must be prepared to rapidly shift the nature and location of his main effort throughout his AO. The commander may have to reposition defending units within their defensive positions or reposition between terrain features as he masses overwhelming effects against the attacking enemy. The defensive plan should designate axes of advance and routes for the commitment or movement of reserves, or the forward or rearward passage of one unit through another. It should identify air axes for aerial maneuver by attack helicopters, air assault units, or fixed-wing aircraft. This capability to reposition is dependent on the defending force having superior tactical mobility. Without tactical mobility, defending forces stay in their prepared positions and accept the possibility of becoming decisively engaged.
9-26. The commander assigning the defensive mission defines the area to defend. A commander defending on a broad front is forced to accept gaps and conduct noncontiguous operations. His forward line of own troops (FLOT) will be discontinuous. Defending shallow areas of operations reduces flexibility and requires the commander to fight well forward. Narrow frontages and deep areas of operations increase the elasticity of an area defense by increasing the commander's maneuver options.
9-27. The ideal area defense is where effective mutual support exists throughout the width and depth of the defender's tactical positions. The commander organizes and occupies these positions based on their natural defensive strength; their retention ensures the integrity of his defense whether he employs a defense in an AO, defends by BP, or employs a combination of both. He maintains tactical integrity within each defensive area. A unit conducting an area defense normally addresses the security requirements of each flank by assigning responsibility to a subordinate element or organizing a security force to specifically execute that mission.
9-28. A defense in depth is normally the commander's preferred option. Forces defending in depth absorb the momentum of the enemy's attack by forcing him to attack repeatedly through mutually supporting positions in depth. Depth gives the commander's fire support assets time to generate devastating effects and affords him multiple opportunities to concentrate the effects of overwhelming combat power against the attacking enemy. This also provides more reaction time for the defending force to counter the attack. The commander gathers more information about the attacking enemy's intentions before the enemy commits to a COA. This reduces the risk of the enemy force quickly penetrating the main line of defense.
9-29. The commander also employs a defense in depth when the enemy has the capability to employ large quantities of precision-guided munitions or weapons of mass destruction. Defense in depth results in friendly units and facilities being dispersed throughout the defensive AO. The commander takes area damage-control measures to reduce the effects of weapons of mass destruction on the friendly force and denies the enemy lucrative targets. The degree of dispersal adopted by defending forces is both a function of the enemy's capabilities and the friendly forces' capability to rapidly concentrate overwhelming combat power at decisive points.
9-30. The commander positions his units in successive layers of battle positions along likely enemy avenues of approach when he conducts a defense in depth. (See Figure 9-4.) The commander usually decides to conduct a defense in depth when—
The mission is not restrictive and allows the commander to fight throughout the depth of the battlefield.
The terrain does not favor a defense well forward, and there is better defensible terrain deeper within the AO.
The AO is deep compared to its width, and there is significant depth available.
The cover and concealment on or near the FEBA is limited.
The enemy has several times the combat power of the defender.
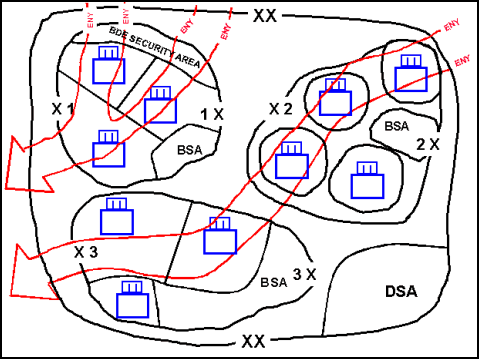
Figure 9-4. Division Conducting a Defense in Depth with Subordinate Brigades
Deployed in Noncontiguous Areas of Operations with Enemy Avenues of Approach Depicted
9-31. Divisions and corps employing a defense in depth can conduct an area defense on a wider frontage than they can if they adopt a forward defense because a forward defense has no time or space to reposition forces. A defense in depth allows the commander to use his security and forward MBA forces to identify the enemy's decisive operation and control the depth of the enemy's penetration into the MBA. By their defensive actions, they provide the commander with time to react to enemy actions and allow him to take offensive steps that eliminate enemy options, such as conducting a counterattack into the flank of an enemy force.
9-32. The commander conducts his decisive operation from forward defensive positions near the FEBA in a forward defense. (See Figure 9-5.) He concentrates a significant portion of his available combat power into EAs along the FEBA. His intent is to prevent significant enemy penetration into the defensive area. The commander conducting a forward defense fights to retain these positions along the FEBA and violently counterattacks any enemy penetration. However, if the enemy penetrates the main defensive positions, the defender's lack of depth may allow the enemy to rapidly exploit success.
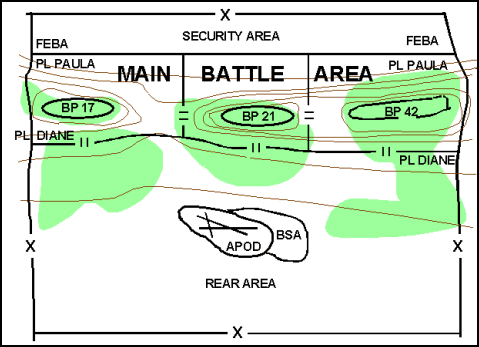
Figure 9-5. Brigade Conducting a Forward Defense in a Contiguous Area of Operations
9-33. In general, the commander uses a forward defense when a higher commander directs him to retain forward terrain for political, military, economic, and other reasons. Alternatively, a commander may choose to conduct a forward defense when the terrain in that part of his AO—including natural obstacles—favors the defending force because—
The best defensive positions are located along the FEBA.
Strong natural obstacles are located near the FEBA.
Natural EAs occur near the FEBA.
Cover and concealment in the rear portion of the AO are limited.
9-34. Whatever the commander's choice—forward or in depth—once the enemy commits his forces, the defending commander has the ability to seize the initiative by counterattacking over familiar ground to destroy a halted, disorganized enemy while protected by overwatching fires from friendly positions. Whenever possible, the commander should direct these counterattacks against the enemy's rear or flanks. The commander's reserve is a key component of the counterattack.
9-35. When deciding where to place his reserve, the commander decides whether to orient his reserve on its most likely mission or its most important mission. He expends significant effort during the planning process to ensure he can effectively use his reserve when needed. He may locate his reserve within the AO where it can employ the road network to rapidly displace throughout the AO in response to a number of opportunities or contingencies. The commander must consider terrain, MSRs of forward units, enemy avenues of approach, and probable enemy penetrations when determining the exact location for his reserve. He may choose to initially position his reserve in a forward location to deceive the enemy and obscure subordinate unit boundaries, especially those of dissimilar units such as armor and light infantry.
9-36. In restrictive terrain that lacks routes for movement, the commander can task organize his reserve into small elements and position them where they can react quickly to local combat developments. This dispersion improves force protection but reduces the ability of the reserve to mass fires. Covered lateral and forward high-speed deployment routes should be available. The reserve must have movement priority along those routes. He must ensure the maintenance of communication between these dispersed elements. This may require establishing retransmission nodes for combat net radios. In open terrain, the commander maintains a centrally located reserve positioned somewhat farther from the FLOT. He considers the enemy's potential to employ weapons of mass destruction and conduct air interdiction when deciding where to position his reserve.
9-37. Whenever possible, the commander positions his reserve beyond the enemy's direct fire range. This is easier to achieve at higher echelons than at lower echelons. The reserve takes defensive measures to prevent being acquired and attacked by enemy indirect fire systems. These include camouflage, local security, and control of electronic emissions.
9-38. The commander also plans how to reconstitute his reserve once he commits his original reserve. Forces most easily designated are subordinate unit reserves. If his higher headquarters has not committed its reserve, he has more flexibility and can take greater risk in employing his reserve.
9-39. A spoiling attack preempts or seriously impairs the enemy's ability to launch an attack, while a counterattack prevents the enemy from exploiting his successes. The forces conducting either form of attack must be large and strong enough to develop the situation, protect themselves, and force the enemy to react, placing his plan at risk.
9-40. The commander considers the enemy situation and estimates the time and distance factors of any follow-on enemy forces in planning either a spoiling attack or a counterattack by his reserve and other forces. Then he determines which of his units will attack, where they will be after the attack, and what interdiction is necessary to isolate the targeted enemy element. (See Figure 9-6.) His counterattacking forces plan to avoid enemy strength when possible. The most effective attacks seize strong positions that permit the counterattacking force to deliver fire on an exposed enemy unit's flanks and rear. If it is tasked to stay and defend against enemy follow-on forces, the counterattacking force must establish a viable defensive position before any following enemy units can make contact.
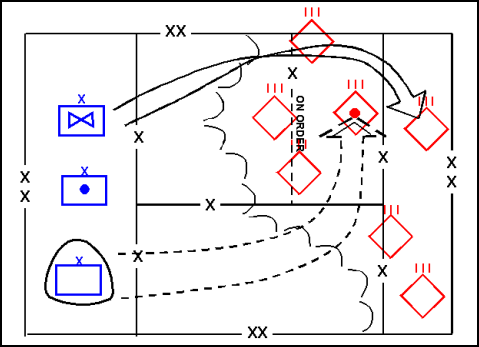
Figure 9-6. Division Counterattack
9-41. Counterattack plans include assumptions regarding the size and shape of the anticipated penetration or enemy formation; the strength and composition of the enemy force; and the status of the reserve and forces in the MBA. Other factors that affect the counterattack include the capability to contain the enemy, shaping operations to support the attack, and the strength and responsiveness of the reserve at the time of the counterattack.
9-42. The commander's staff prepares counterattack plans and then allocates subordinate headquarters sufficient time to make their plans. The control measures for a counterattack are the same ones discussed in Chapter 5 for the attack. If possible, the commander distributes his counterattack plans along with the basic defense plan. Reserve unit commanders conduct detailed counterattack planning that includes conducting reconnaissance, selecting multiple routes, determining time and space factors, rehearsing, coordinating with appropriate elements of the forward defending force, and fire planning. The commander adjusts his counterattack plans as necessary based on the lessons learned during rehearsals.
9-43. Enemy movement into an NAI helps the commander determine the enemy's scheme of maneuver and possible objectives. He uses decision points and NAIs throughout his AO to trigger his counterattack. The commander identifies TAIs for attack to support his operations.
9-44. Preparations focus on planning those additional ISR operations required to answer the commander's critical information requirements, refining the plan, increasing coordination and synchronization, and conducting shaping actions within the force's capability and operations security guidelines. If the commander decides that he must conduct a deliberate defense but knows that the enemy will attack before he is prepared, he may have to commit substantial forces to security operations or conduct a spoiling attack. This buys time and space to prepare for a deliberate defense.
9-45. A unit normally transitions to the defense after it completes the deployment process of force projection, completes offensive operations, or is in an assembly area. The commander issues a warning order stating the mission and identifying any special considerations. His staff conducts detailed planning while the rest of the unit completes its current mission. The staff coordinates for the pre-positioning of ammunition and barrier material in a secure area near the unit's defensive positions before starting the operation.
9-46. Before occupying any position, leaders at all echelons conduct some type of reconnaissance. This reconnaissance effort is as detailed as the factors of METT-TC permit. It may consist of a simple map reconnaissance or a more detailed leaders' reconnaissance and initial layout of the new position.
9-47. The defending unit occupies its defensive positions as soon as practical after receiving the mission. It conducts reconnaissance of the defensive area and establishes a forward security area before occupying the positions The unit may pre-position supplies such as ammunition and barrier materiel once it establishes security. The unit can accomplish many defensive tasks simultaneously; the factors of METT-TC are the deciding consideration in establishing priorities of work. Those priorities may be—
Establishing local security and deploying a security force.
Identifying EAs where the commander wants to engage and destroy the enemy.
Planning fire control measures, such as TRPs, trigger lines, and final protective fires to support the EAs.
Positioning key weapon systems to engage into the EAs and TRPs and develop range cards and sector sketches.
Positioning observers who can see both targets and trigger lines.
Siting obstacle groups to support weapon systems.
Designating and clearing fields of fire.
Preparing primary fighting positions based on the anticipated fighting conditions, such as the time of day and weather conditions.
Emplacing obstacles and surveying indirect fire targets to support these obstacles.
Providing concealment and camouflage for fighting and survivability positions as they are constructed.
Positioning any available critical friendly zones over friendly positions by establishing sensor coverage and quickfire links between the sensor and shooter.
Installing night and limited-visibility aids, such as thermal hot spots and chemical lights on TRPs during daylight.
Updating range cards and sector sketches as required.
Preparing alternate fighting positions.
Designating and preparing supplementary positions.
Designating hide positions and rehearsing movements to and from fighting positions. (Units may place their combat and tactical vehicles in hide positions at any time while preparing the defensive position.)
Positioning the reserve.
Establishing contact points with any adjacent units so that the defensive efforts of both units can be tied together.
Emplacing wire for communications.
Improving mobility on counterattack routes.
Prestocking ammunition in revetments or bunkers where it can survive the enemy's preparatory fires.
Rehearsing movements under daylight and limited-visibility conditions.
Continuing to improve the defense.
9-48. Survivability positions enhance the strength of a defensive position by providing soldiers and weapon systems with some degree of cover from enemy fires. Units initiate construction of survivability positions in accordance with their priority of work and continue to build and improve them until the last possible moment. The overhead cover provided varies with the location of the sheltered troops and enemy capabilities. As time and resources allow, the defending unit improves communication routes throughout its defensive positions to ease movement of supplies and forces, particularly the reserve. It quickly establishes wire communications among its various subordinate elements to reduce its electromagnetic signature.
9-49. The defending unit rehearses how to move from its hide positions to its primary positions and how it will occupy alternate and supplementary positions to continue to engage the enemy if he progresses into the unit's defensive positions. These rehearsals establish the time necessary to conduct these movements under different environmental conditions. It modifies existing plans based on the results of rehearsals and changes in the factors of METT-TC. The commander takes steps to ensure that the routes taken during these rehearsals do not show obvious signs of heavy use. These steps can include the conduct of only dismounted rehearsals, only moving one vehicle per platoon, and taking steps to eliminate signs of movement such as sweeping snow back over the tracks made during the rehearsal.
9-50. The commander ensures close coordination among his subordinates. During the preparation phase, he can take his subordinate commanders to a vantage point in the MBA to rehearse the battle and plan coordination among their units if such a site is available. This helps the commander in transmitting his intent and in establishing common control measures for subordinate units.
9-51. The location, composition, and movement of the reserve are essential elements of friendly information. Enemy reconnaissance efforts focus on finding the reserve and reporting when and where it is committed. Avoiding detection by the enemy is vital to the success of the reserve.
9-52. The CSS rehearsal should be integrated into the maneuver rehearsal to verify that routes for support do not cross or conflict with routes used by reserve forces or other maneuver elements. The commander should balance the use of ammunition caches against the defending unit's ability to guard them. The commander should also ensure that alternate MSRs are adequate to accommodate contingency plans and that changing MSRs can be accomplished effectively.
9-53. The commander ensures that his combat multipliers are completely integrated with his intended maneuver. This includes the use of camouflage, deception, and smoke to confuse enemy reconnaissance assets. Having key representatives from each of these multipliers simultaneously rehearse the plan with his subordinate maneuver unit is an effective technique for ensuring integration. After issuing the order and receiving briefbacks from his subordinate commanders and other leaders, the commander verifies that they have a common understanding of the plan and can execute it with minimal guidance.
9-54. A defending unit within the MBA uses a variety of tactics, techniques, and procedures to accomplish the mission. At one end of the defensive continuum is a totally static defense oriented on terrain retention. This defense depends on the use of firepower from fixed positions to deny the enemy terrain. At the other end is a dynamic defense focused on the enemy. That defense depends on maneuver to disrupt and destroy the enemy force.
9-55. A commander combines the static element to control, stop, or canalize the attacking enemy and the dynamic element to strike and defeat him. A successful area defense uses forces in relatively fixed positions to create the opportunity for the reserve to strike at the enemy from an unanticipated direction and strength. (See Figure 9-7.) The defending force repeatedly lures the enemy into EAs where it kills selected portions of the enemy force.
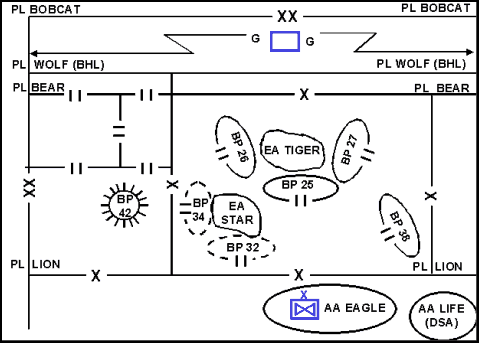
Figure 9-7. Area Defense Using Static and Dynamic Elements
9-56. In an area defense, defending forces fight mainly from prepared, protected positions to concentrate combat power effects against attempted enemy breakthroughs and flanking movements. The commander uses mobile forces to cover gaps between defensive positions, reinforce those positions as necessary, and counterattack to seal penetrations or block enemy attempts at flanking movements.
9-57. Conducting shaping operations in an area defense is similar to shaping operations in the offense. The factors of METT-TC determine how closely the commander synchronizes his shaping operations with his decisive operations. The commander conducts shaping operations designed to regain the initiative by limiting the attacker's options and disrupting the enemy's plan. He conducts shaping operations to prevent enemy forces from massing and creates windows of opportunity for decisive offensive operations, allowing his force to defeat them in detail. The commander also employs shaping operations to disrupt enemy operations by attacking command posts at critical stages in the battle or by striking and eliminating key elements, such as river crossing equipment and supplies in a region that contains numerous unfordable rivers. Reconnaissance and security operations are normally components of the echelon's shaping operations.
9-58. This manual divides execution into five steps:
Gain and maintain enemy contact.
Disrupt the enemy.
Fix the enemy.
Maneuver.
Follow through.
This does not imply that these steps occur sequentially; they may occur simultaneously.
9-59. Gaining and maintaining contact with the enemy in the face of his determined efforts to destroy friendly ISR assets is vital to the success of defensive operations. As the enemy's attack begins, the defending unit's first concerns are to identify committed enemy units' positions and capabilities, determine the enemy's intent and direction of attack, and gain time to react. Initially, the commander accomplishes these goals in the security area. The sources of this type of intelligence include reconnaissance and security forces, intelligence units, special operations forces, and aviation elements. The commander ensures the distribution of a common operational picture throughout the force during the battle as a basis for subordinate commanders' actions. (See FM 6-0.) The commander uses the information available to him, in conjunction with his military judgment, to determine the point at which the enemy is committed to a COA.
9-60. The security force seeks to strip enemy reconnaissance forces and hide the defending force's dispositions, capabilities, and intent at the same time as friendly ISR assets help to determine the enemy's chosen COA. Ideally, the fight in the security area should force the enemy to conduct a movement to contact against a prepared defense.
9-61. A single force in the security area can perform both reconnaissance and security functions. The security force uses every opportunity for limited offensive action to delay and harass the enemy and to gain information. As the security element displaces, the commander makes preparations to pass it through or around the MBA force as quickly as possible by using multiple passage points, gaps, or lanes along the FEBA. This usually occurs in one location at a time until the security force has completely withdrawn. However, the security force may pass in sequence based on enemy pressure. Transfer of responsibility occurs forward of the FEBA at the BHL. (See Figure 9-8.) Taking advantage of previous liaison and plans, the security force makes any required last-minute coordination with MBA forces at contact points to ensure its rapid passage through the MBA force.
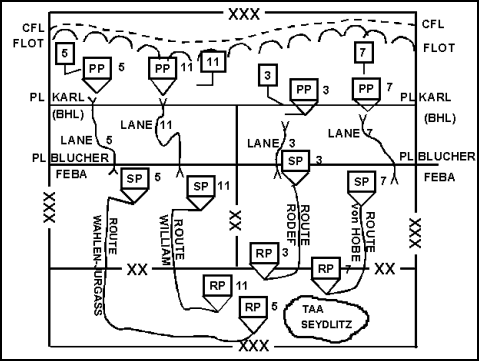
Figure 9-8. Battle Handover Line
9-62. The entire security force should not withdraw automatically as soon as the first enemy units reach the FEBA. The commander can leave in place security elements located in areas where the enemy has not advanced. The security force adjusts to the enemy's advance and continues to conduct security operations as far forward as possible. It continues to resist the enemy's shaping operations, such as the enemy's reconnaissance effort, thereby upsetting his coordination and allowing the MBA commander to fight one engagement or battle at a time. Doing this increases the chances for success even if the enemy attack penetrates into the MBA in some areas. In some cases, the security force can attack the enemy force from its rear, engage high-payoff targets, or drive between echelons to isolate leading enemy units.
9-63. As the enemy force approaches the MBA, the commander may order reconnaissance and surveillance assets within his security force to displace to one or both sides of the enemy penetration and continue to maintain surveillance. By observing and providing access to enemy flanks, reconnaissance and surveillance elements can facilitate the conduct of friendly counterattacks. However, to prevent the encirclement of these assets, the commander may plan to monitor those areas where the enemy has not advanced into the MBA solely by technical means.
9-64. Battle handover between the security force and MBA forces requires close coordination and occurs as quickly and efficiently as possible to minimize their vulnerability to enemy fire. The security force commander must retain freedom to maneuver until he initiates the passage of lines. The commander's fire support assets help cover the withdrawal of security forces. Combat support and CSS elements of the security force should move to the rear as early as possible to avoid hampering the movement of combat forces. Normally, battalion-size units of the security force hand off the battle to the brigades through which they pass. (See Chapter 16 for a discussion of rearward passage of lines.)
9-65. The commander must consider the security force's next mission prior to battle handover between the security force and the MBA force. Factors that may affect his decision are the status of the security force, its subsequent mission preparation requirements, and the size and nature of the reserve required by the situation. He may decide to employ it immediately as his reserve, which would release his initial reserve for other tasks. Alternately, the commander may decide to use the security force to conduct additional security operations on the flanks of MBA forces as the battle progresses. However, it may be some time before the security force is ready for commitment. Therefore, the commander is more likely to wait until the security force has been reconstituted and the initial reserve committed before designating the former security force as his reserve.
9-66. The commander should base the location of his security force's assembly area on its follow-on mission. The commander wants those assembly areas located to rapidly support ongoing operations yet keep withdrawn security units from interfering with ongoing decisive and shaping operations. After passage, the security force normally moves to these locations to prepare for subsequent operations. At a minimum he must rearm and refuel the security force. Additional CSS concerns include casualty evacuation, maintenance requirements, and resupply of the other classes of supply.
9-67. The commander executes his shaping operations to disrupt the enemy regardless of his location within the AO. After making contact with the enemy, the commander seeks to disrupt his plan, his ability to control his forces, and his combined arms team. Ideally, the results of the commander's shaping operations should force a disorganized enemy, whose ability to synchronize its elements has been degraded, to conduct a movement to contact against prepared defenses. Once the process of disrupting the enemy begins, it continues throughout a defensive operation.
9-68. The commander initiates his shaping operations simultaneously with the preparation of his MBA positions. These shaping operations typically focus on high-payoff targets, command and control nodes, engineer, fire support, and air defense assets for destruction or disruption. They can also force the enemy to use avenues of approach covered by friendly EAs. These shaping operations destroy the enemy's cohesion and disrupt the tempo of his approach to the MBA. This, in turn, disrupts the timely introduction of enemy follow-on forces into the engagement. For example, offensive information operations directed against the enemy's C2 nodes and air defense assets increase the enemy's vulnerability to other shaping operations while simultaneously slowing the enemy's reaction to these shaping operations. (FM 3-13 discusses offensive information operations.) Follow-on engagements focus on degrading the enemy's fire support and engineer assets, thereby disrupting the movement of his approaching units.
9-69. Other targets for shaping operations include enemy reconnaissance and intelligence assets. Destroying these assets allows the commander to repeatedly force enemy units to deploy into combat formations on ground of his choosing, thus contributing to the disruption and desynchronization of the enemy's plan. The timing of these shaping operations is important. The enemy cannot be allowed to recover from their effects prior to the decisive operation. The commander may also execute offensive operations to further disrupt the enemy, such as spoiling attacks, raids, ambushes, feints, or demonstrations.
9-70. The commander does everything in his power to limit the options available to the enemy when conducting an area defense. In addition to disrupting the enemy, the commander conducts shaping operations to constrain the enemy into a specific COA, control his movements, or fix him in a given location. These actions limit the enemy's options. While executing these operations, the commander continues to find, and delay or attrit enemy follow-on and reserve forces to keep them from entering the MBA.
9-71. The commander has several options to help him fix an attacking force. The commander can design his shaping operations—such as securing the flanks and point of a penetration—to fix the enemy and allow friendly forces to execute decisive maneuver elsewhere. Previously discussed in Chapter 8, combat outposts and strong points can also deny enemy movement to or through a given location. A properly executed military deception operation can constrain the enemy to a given COA.
9-72. The commander uses obstacles covered by fire to fix, turn, block, or disrupt to limit the options available to the enemy. Properly executed obstacles are a result of the synthesis of top-down and bottom-up obstacle planning and emplacement. Blocking forces can also affect enemy movement. A blocking force may achieve its mission from a variety of positions depending on the factors of METT-TC.
9-73. In an area defense, the decisive operation occurs in the MBA. This is where the effects of shaping operations, coupled with sustaining operations, combine with the decisive operations of the MBA force to defeat the enemy. The commander's goal is to prevent the enemy's further advance through a combination of fires from prepared positions, obstacles, and mobile reserves.
9-74. Generating massed effects is especially critical to the commander conducting the defense of a large area against an enemy with a significant advantage in combat power. The attacker has the ability to select the point and time of the attack. Therefore, the attacking enemy can mass his forces at a specific point, thus dramatically influencing the ratio of forces at the point of attack. An enemy three-to-one advantage in overall combat power can easily turn into a local six-to-one or higher ratio. The defending commander must quickly determine the intent of the enemy commander and the effects of terrain. This allows his units and their weapon systems to use agility and flexibility to generate the effects of combat power against the enemy at those points and restore a more favorable force ratio.
9-75. Forces in the MBA assume responsibility for the battle at the BHL. As the security force approaches the FEBA, it may be necessary to increase the intensity of fire support from the MBA to allow the security force to break contact. Both direct and indirect fire assets from MBA forces provide support to cover the withdrawal of the security force and to close passage lanes through obstacle complexes. The commander may also employ smoke to assist the security force break contact with the enemy. The security force's withdrawal through the forward positions of the MBA must be carefully planned and coordinated. The commander must guard gaps in obstacles left for the withdrawal of the security force and arrange for closing them after the passage of the security force.
9-76. After the enemy reaches the MBA, he tries to find weak points and attempts to force a passage, possibly by a series of probing attacks. As the attack develops, defending units engage the enemy's lead forces. The enemy advance may slow because of canalization and the increased density of forces resulting from limited maneuver space, presenting good targets for defensive fire and air support. The maximum effects of simultaneous and sequential fires are brought to bear at this stage of the battle.
9-77. The commander's subordinate elements maneuver using massed direct and indirect fire and movement to gain positional advantage over the assaulting enemy force. The commander also directs the engineer obstacle and sustainment effort by his assignment of priorities. The commander must reposition his forces to meet the enemy where he is rather than where the commander would like him to be. The commander directs operations and supports his subordinate elements by providing the necessary CS and CSS. He controls the commitment of the reserve and, at division echelon and above, engages enemy follow-on forces. If enemy follow-on forces can be delayed, the enemy's attack may be defeated in detail, one echelon at a time. If the defending unit can force the enemy to commit follow-on forces sooner than planned, it can disrupt the enemy's timetable, which can lead to the creation of exploitable gaps between the committed and subsequent echelons.
9-78. Gaps between defensive positions may be necessary, but they are not left where the commander expects the enemy's probable main effort. They are kept under surveillance, covered by fire or, where possible, blocked by barriers or repositioned friendly forces. The commander clearly defines the responsibility for dealing with each enemy penetration. He leverages the use of choke points and obstacles to prevent enemy penetration. If the enemy succeeds in penetrating the MBA, the commander blocks the penetration immediately and destroys this enemy force as soon as possible; hence, the need for a mobile reserve. He may extend his actions within the depth of his AO to counter enemy penetrations that cannot be stopped farther forward.
9-79. The commander never allows the attacking enemy to consolidate unless it fits his scheme of maneuver. He conducts a local counterattack with all available local resources to prevent the enemy from consolidating his gains. The lowest possible echelon conducts this local counterattack; however, the commander must be aware of the problem of piecemeal commitment. A unit does not abandon a position unless it fits within the higher commander's intent or he grants permission to do so. If the defending force is unable to repulse the enemy, it tries to contain the enemy penetration until it can attack in concert with major counterattacking forces. The commander coordinates his counterattacks with the efforts of his fire support system.
9-80. Although the commander plans for the counterattack in his defensive planning, he is aware that his plan may not correspond exactly with the existing situation when he launches the counterattack. As the situation develops, the commander reassesses his plan based on his revised situational understanding that results from an updated common operational picture as new intelligence and combat information becomes available to answer the following basic questions:
Is a counterattack feasible, or should the commander use the reserve to contain enemy successes?
When and where should the defending forces counterattack?
In the case of enemy penetrations, what should the defending forces counterattack and what should they block or contain?
Is there enough time to complete the counterattack before the arrival of enemy follow-on forces?
Can he conduct a counterattack using his fire support systems?
9-81. When counterattacking, the commander employs all available resources necessary to ensure success. The reserve usually becomes the echelon's decisive operation on its commitment, so he avoids its premature or piecemeal commitment. One of the commander's most critical decisions is committing the reserve. He may reinforce his reserve force before committing it to give it greater capability to counter enemy action. The commander does not counterattack as an automatic reaction to an enemy penetration, nor does he commit the reserve solely because the enemy has reached a certain phase line or other location. Fire support assets and local counterattacks by forces already defending could destroy, disrupt, or attrit enemy penetrations, thus relieving the commander of the need to commit his reserve. When possible, the commander launches the counterattack when the enemy presents his flank or rear, overextends himself, or his momentum dissipates. Once the commander identifies the flanks of the enemy's main effort, he can target counterattacks to isolate and destroy enemy forces within the MBA.
9-82. Sometimes the commander may determine that he cannot afford to use his reserve to counterattack. Therefore, he must use his resources to block, contain, or delay the enemy to gain time to employ higher-echelon reserves. In these cases, the commander and his staff must plan how to integrate reinforcing companies and battalions into the defensive scheme, adjust boundaries, and place BPs. He plans the routes these units will use, and what adjustments will be necessary in existing C2 arrangements. He can speed the process of positioning and moving reinforcements or the reserve by designating routes and providing traffic-control personnel and guides at contact points to lead and brief them on the situation. Scouts, military police, and divisional cavalry units can provide traffic control.
9-83. The purpose of defensive operations is to retain terrain and create conditions for a counteroffensive that regains the initiative. The area defense does this by causing the enemy to sustain unacceptable losses short of his decisive objectives. A successful area defense allows the commander transition to an attack. An area defense could also result in a stalemate with both forces left in contact with each other. Finally, it could result in the defender being overcome by the enemy attack and needing to transition to a retrograde operation. Any decision to withdraw must take into account the current situation in adjacent defensive areas. Only the commander who ordered the defense can designate a new FEBA or authorize a retrograde operation.
9-84. During this follow-through period, time is critical. Unless the commander has a large, uncommitted reserve prepared to quickly exploit or reverse the situation, he must reset his defense as well as maintain contact with the enemy. Time is also critical to the enemy, because he will use it to reorganize, establish a security area, and fortify his positions.
9-85. There is a difference between local counterattacks designed to restore the defense and a decisive operation designed to wrest the initiative from the enemy and then defeat him. To conduct a decisive counterattack, the defending force must bring the enemy attack to or past its culminating point before it results in an unacceptable level of degradation to the defending force. To do this, the defending force must disrupt the enemy's ability to mass, causing him to disperse his combat power into small groups or attrit his forces to gain a favorable combat power ratio. The defending force must continue to disrupt the enemy's ability to introduce follow-on forces and to destroy his sustainment system. In the defense, the commander must prepare to quickly take advantage of fleeting opportunities, seize the initiative, and assume the offense. Ideally, he already has a counterattack plan appropriate to the existing situation. He must rapidly reorganize and refit selected units, move them to attack positions, and attack. Alternatively, he must conduct an attack using those units already in contact with the enemy, which is normally the least favorable COA.
9-86. It is extremely difficult for the enemy to fight a defensive battle in response to a friendly counterattack after he reaches a culminating point for the following reasons:
His defensive preparations are hasty.
His forces are not adequately organized for defense.
Reorganizing for a defense requires more time than the friendly commander should allow.
The enemy force is dispersed, extended in depth, and weakened.
Enemy attacks rarely culminate on ground ideally suited for defense.
Physical fatigue.
9-87. The shift to defense requires enemy soldiers to make a psychological adjustment. Soldiers who have become accustomed to advancing, and thus winning, must now halt deep in the opposing force's territory and fight defensively, sometimes desperately, on new and often unfavorable terms. If the enemy commander decides to conduct retrograde operations to more defensible ground, his soldiers find it even harder to adjust psychologically.
9-88. If the defensive battle leads to a stalemate with both forces left in contact with each other, the defending force must seek to retain the initiative and set the conditions for the next encounter. The commander must prepare the defending unit to move rapidly to a subsequent defensive position during a lull in the battle because it is risky to defend from the same position twice. The enemy will know the location of the defending force's position and subject them to his supporting fires unless the defending force moves. Nevertheless the defending unit should normally stay in place and continue to fight unless it can suppress the enemy's approaching forces or take other actions to distract the enemy. This is because of the risk to a unit when it moves out of its prepared positions while still under enemy pressure.
9-89. If the defending unit is unable to maintain the integrity of its defense, it must transition to a retrograde operation or risk destruction. The commander must analyze how to execute this transition and prepare contingency plans. If the situation requires a retrograde movement, the commander conducts the operation according to the retrograde fundamentals and principles addressed in Chapter 11. In the retrograde, if the defending force can trade space for time without sustaining unacceptable losses, the commander can usually reestablish the conditions required for a successful defense.